- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
Redact Universal Unique IDs (UUIDs) in Logs
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
This guide has been deprecated and is no longer maintained
Overview
This guide goes over how to create a custom scanning rule using a regular expression (regex) pattern to match and redact a Universally Unique Identified (UUID). For example, your organization might have a UUID for internal identification, with additional information appended, such as the user’s:
- User ID
- Department code
- Status code
If you want internal users to access these logs without exposing the UUID and user ID, you can create a custom scanning rule to redact the information.
Set up a custom rule to match a UUID
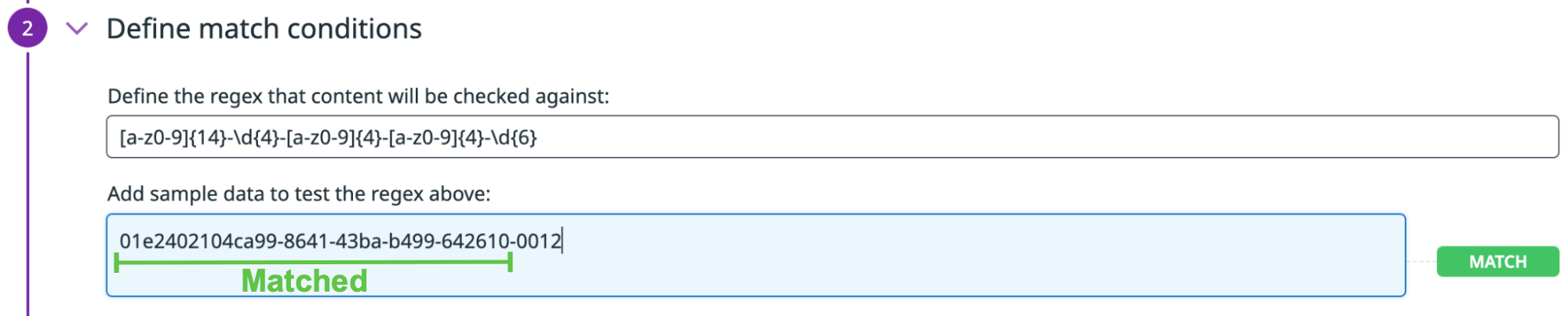
For this guide, 01e2402104ca99-8641-43ba-b499-642610-0012 is the example internal identifier being used, where:
01e2402104ca99-8641-43ba-b499is the UUID.6462610is a 6-digit value that represents the ID in byte format.0012is A 2-digit department code and 2-digit status code of a user:00is used for an active user.12for the department code.
In this example, you want to match the format of the example identifier (01e2402104ca99-8641-43ba-b499-642610-0012) and:
- Redact the UUID, user ID, and the ID in byte format.
- But not redact the department and status code of the user.
You can use the following basic regex to match the UUID and user ID that you want to redact:
[a-z0-9]{14}-\d{4}-[a-z0-9]{4}-[a-z0-9]{4}-\d{6}
- Navigate to the Sensitive Data Scanner settings page.
- Click Add and select Add Scanning Rule.
- Click Custom Rule.
- Select the scanning group to which you want to add this rule.
- Enter a name for the rule.
- Select the priority you want for the rule.
- Enter a description for the rule.
- In the Match conditions section, enter
[a-z0-9]{14}-\d{4}-[a-z0-9]{4}-[a-z0-9]{4}-\d{6}in the regex field. - Use a keyword dictionary to refine detection accuracy and avoid false positives. For this example, you want to match within 10 characters of the word
user:- Enter
useras a key word. - Enter
10for Characters before match.
- Enter
- In the Action on Match section and for this example:
- Select Entire Event for how much of the event to scan. If you have the log parsed out using the Grok Parser, you can scan by specific attributes.
- Select Redact for the action on match.
- Enter
[removed]for the replacement text. - Enter
matched_on:user_idfor the Add tags field.
- Click Add rule.
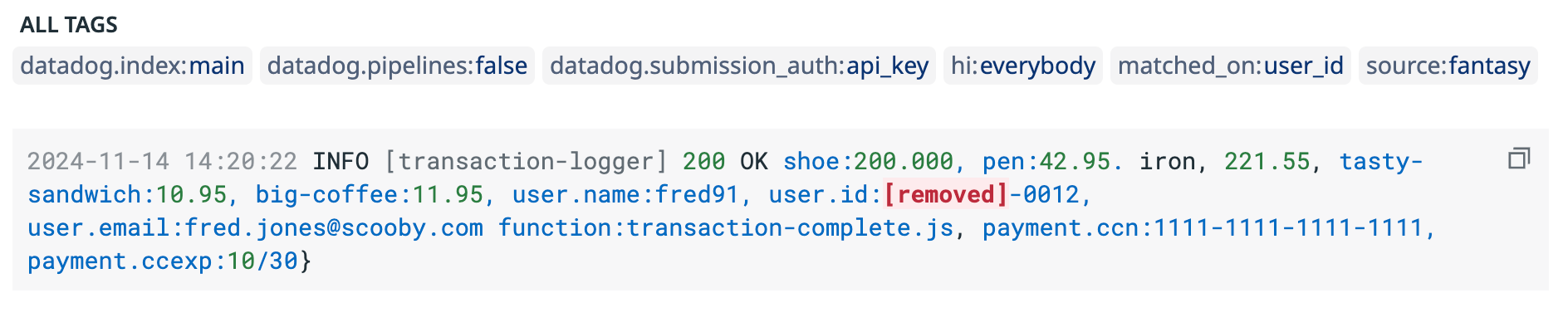
If this example log, which contains the different components of the UUID, is sent to Datadog:
2024-11-14 14:20:22 INFO [transaction-logger] 200 OK shoe:200.000, pen:42.95. iron, 221.55, tasty-sandwich:10.95, big-coffee:11.95, user.name:fred91, user.id:01e2402104ca99-8641-43ba-b499-642610-0012, user.email:fred.jones@scooby.com function:transaction-complete.js, payment.ccn:1111-1111-1111-1111, payment.ccexp:10/30}
The result is the user.id is redacted and replaced with [removed]:
Further reading
お役に立つドキュメント、リンクや記事: