- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
Library Inventory
This product is not supported for your selected Datadog site. ().
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
The Library Inventory provides a unified view of all third-party libraries detected across your codebase and services. It helps you understand which components you depend on, which versions are in use, and where vulnerabilities or license risks might exist. The inventory is built from two complementary data sources:
- Static Software Composition Analysis (Static SCA), which scans your repositories to identify every library referenced in your source code.
- Runtime Software Composition Analysis (Runtime SCA), which detects libraries that are actually loaded and used at runtime by your services. This combined visibility helps you distinguish between theoretical dependencies and real risk exposure.
Static view
The Static view lists all libraries referenced in your repositories as detected by Static SCA.
Static SCA analyzes dependency files and source code to identify all declared third-party libraries, regardless of whether they are used at runtime. Use this view to:
- See your complete dependency footprint
- Identify libraries present in specific repositories
- Track dependency versions and upgrade needs
- Explore vulnerabilities and license metadata for all referenced libraries
Static data updates on every repository scan.
Runtime view
The Runtime view lists only the libraries actively used by your services in production or other monitored environments, as detected by Runtime SCA.
Runtime SCA observes loaded dependencies through the Datadog tracing library, enabling you to:
- Prioritize vulnerabilities in libraries that are actually executed
- Reduce noise by filtering out unused dependencies
- Understand real exposure to vulnerable components
- Map vulnerable libraries to the services and environments using them
This view updates continuously as your services run.
Library details
Clicking any library in the inventory opens the library detail panel, which provides an in-depth view of its metadata, vulnerabilities, and usage.
The panel includes the following sections.
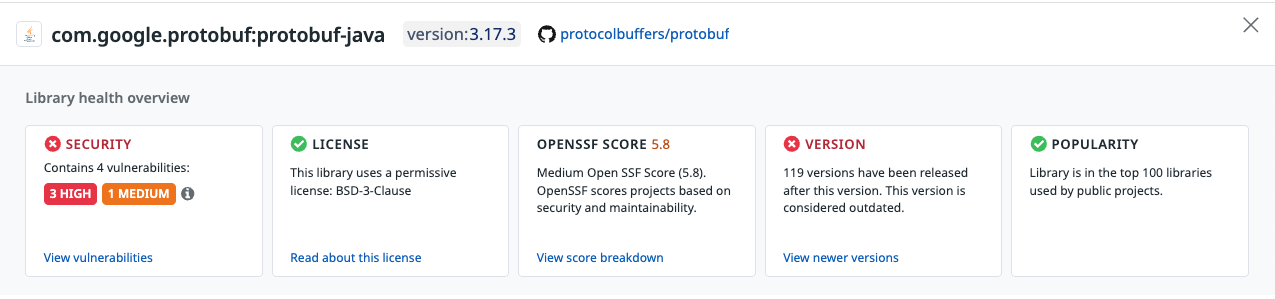
Overview
Displays key information about the selected library and version, including:
- Security status (count of Critical, High, Medium, Low vulnerabilities)
- License type
- Version status (older version, actively maintained, deprecated, etc.)
- Popularity and download statistics when available
This section provides a snapshot of the security and maintenance posture of the dependency.
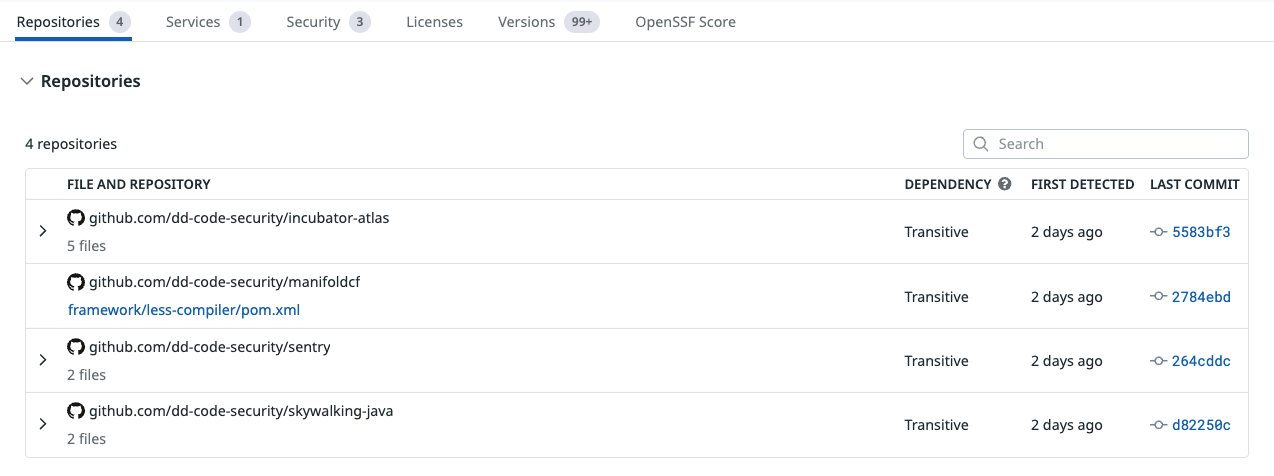
Repositories
Shows all repositories where this library is referenced, as detected by Static SCA.
For each repository, you can see:
- The file and path where the dependency was declared
- Whether the dependency is direct or transitive
- The first detection timestamp
- The latest scanned commit
Use this view to understand how widely the library is used across your codebase.
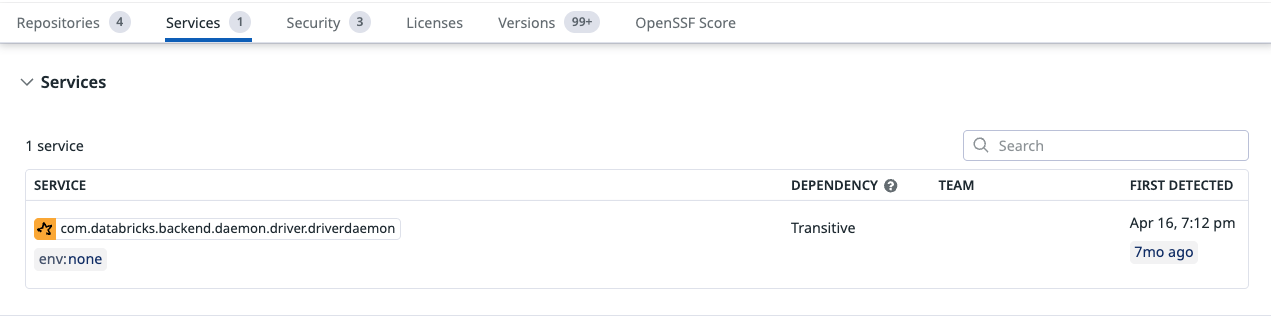
Services
Shows all services that load this library at runtime, as detected by Runtime SCA.
For each service, you can view:
- The environments where it is running (for example, env:dev, env:prod)
- The team responsible (when available)
- The first time the library was detected in that service
If no services appear, the library is referenced statically but not used at runtime.
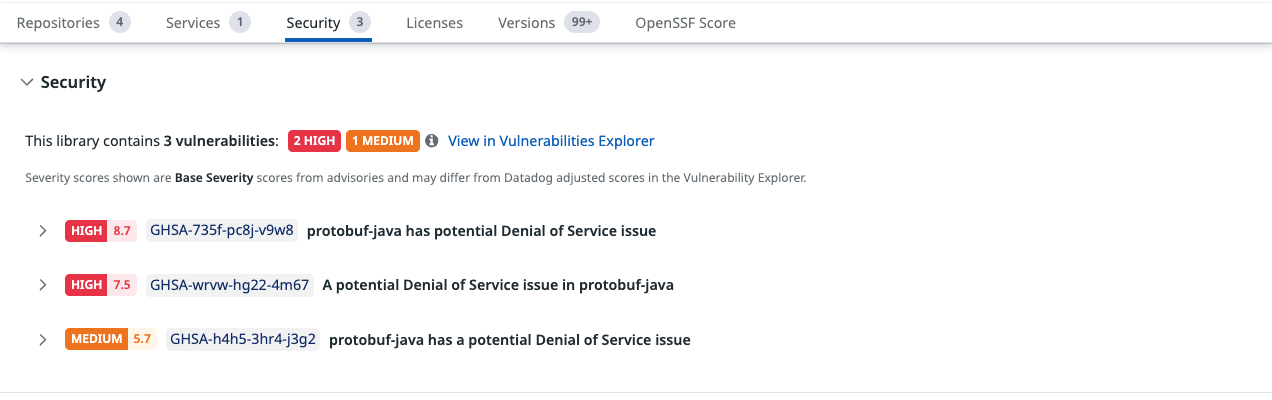
Security
Lists all known vulnerabilities affecting this library version, including:
- Severity (Critical, High, Medium, Low)
- CVE or advisory ID (for example, GHSA identifiers)
- A short description of each vulnerability
- Links to the full vulnerability details
This section consolidates all vulnerabilities detected by Datadog from upstream security advisories.
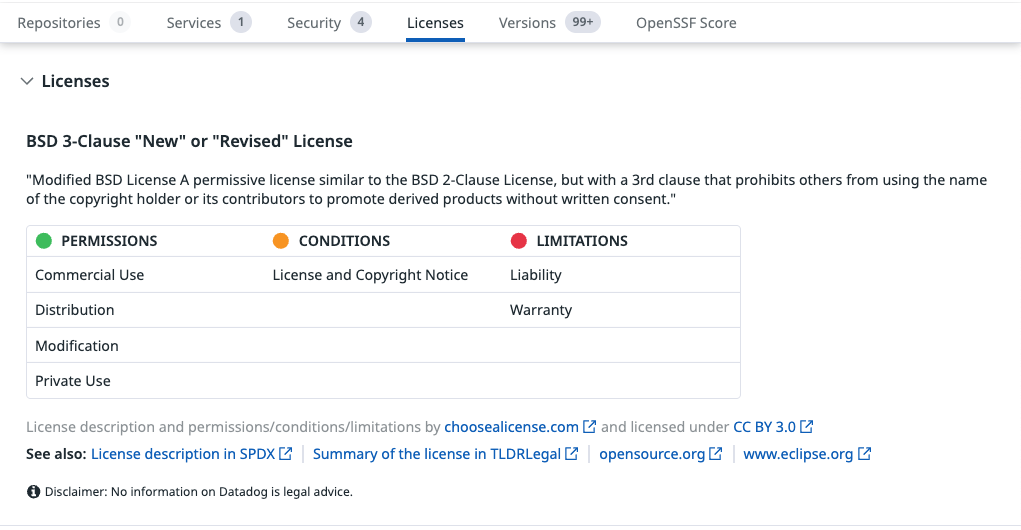
Licenses
The license table in this section is based on the Choose a License Appendix: https://choosealicense.com/appendix/
It summarizes the license’s:
- Permissions
Conditions - Limitations
Additionally, Datadog identifies license risks, including:
- Network copyleft: code must be released when offered as a network service
- Strong copyleft: derivative work must be open-sourced under the same license
- Non-standard copyleft: copyleft terms differ from common OSI-approved patterns
- Non-commercial: use is restricted to non-commercial contexts
- Non-standard / Non-free: license does not meet standard open-source definitions
Each risk contains a short explanation and links to more detailed license information.
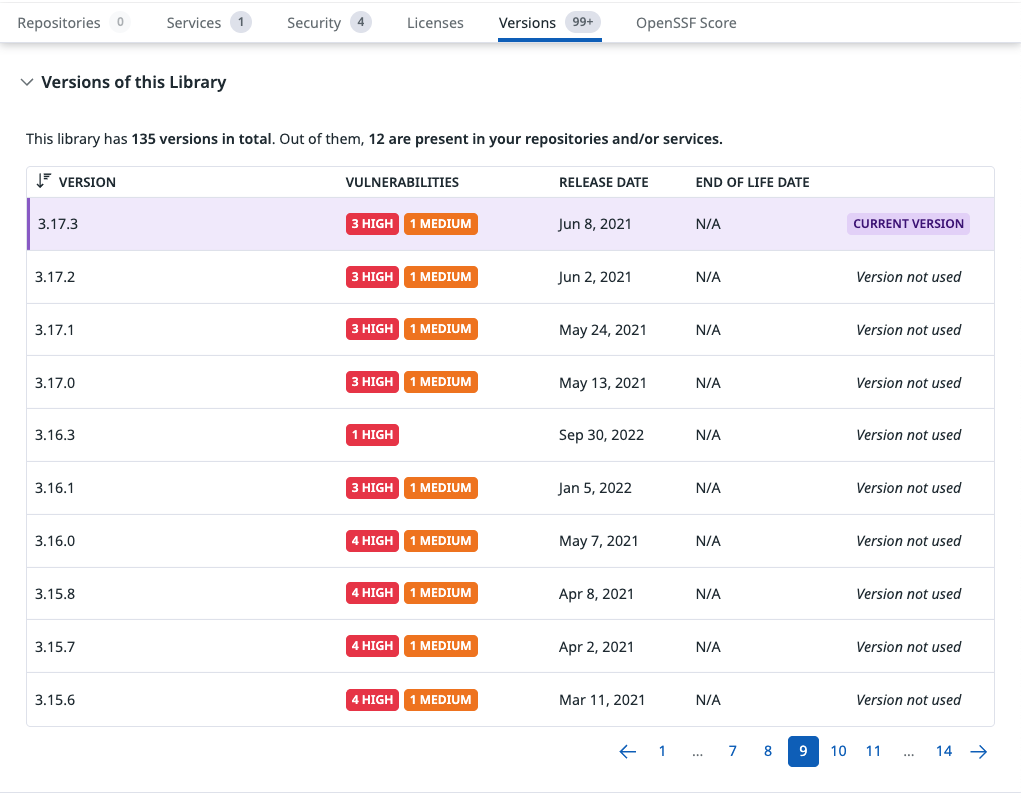
Versions
Lists all known versions of the library, along with:
- Release dates
- Vulnerability counts for each version
- Whether the version is used in your repositories or services
This helps you evaluate remediation options and identify safer upgrade paths.
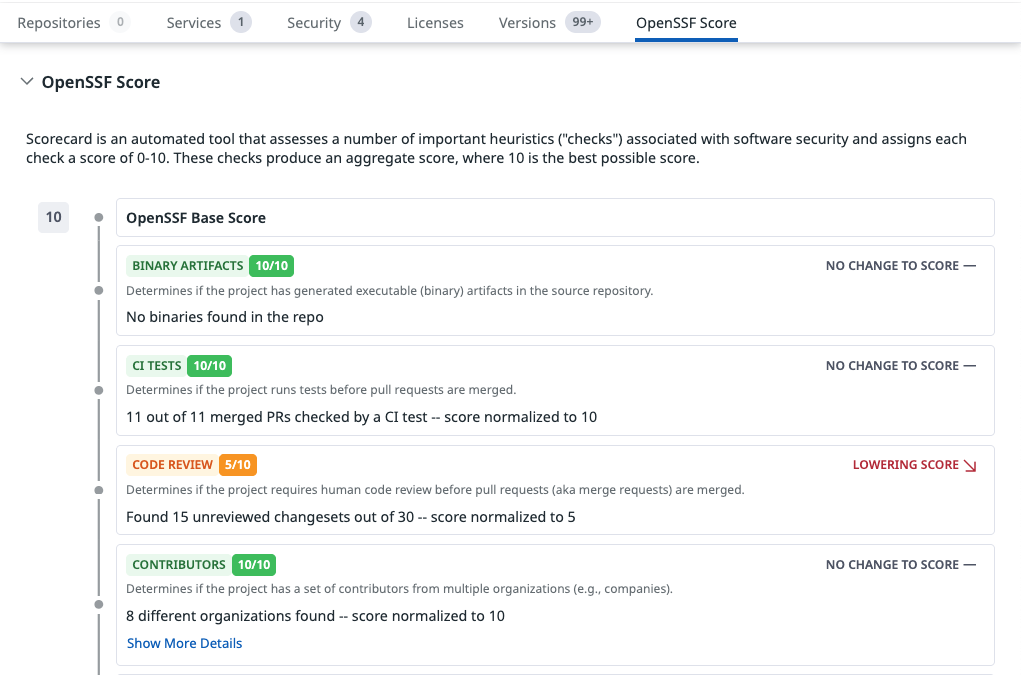
OpenSSF score
Displays the OpenSSF Scorecard results for the upstream project. Each check provides insight into the project’s security maturity, such as:
- Maintenance activity
- Use of security policies
- Safe workflow practices
- Dependency pinning
- Binary artifact usage
The score ranges from 0 to 10, where 10 indicates best practices.
Next steps
To get started with Library Inventory:
- Enable Static SCA to detect libraries in your repositories. See static setup to get started.
- Enable Runtime SCA to identify libraries actually used during execution. See runtime setup to get started.
- Use both views together to understand both your full dependency footprint and your real runtime exposure.