- Esenciales
- Empezando
- Agent
- API
- Rastreo de APM
- Contenedores
- Dashboards
- Monitorización de bases de datos
- Datadog
- Sitio web de Datadog
- DevSecOps
- Gestión de incidencias
- Integraciones
- Internal Developer Portal
- Logs
- Monitores
- OpenTelemetry
- Generador de perfiles
- Session Replay
- Security
- Serverless para Lambda AWS
- Software Delivery
- Monitorización Synthetic
- Etiquetas (tags)
- Workflow Automation
- Centro de aprendizaje
- Compatibilidad
- Glosario
- Atributos estándar
- Guías
- Agent
- Arquitectura
- IoT
- Plataformas compatibles
- Recopilación de logs
- Configuración
- Automatización de flotas
- Solucionar problemas
- Detección de nombres de host en contenedores
- Modo de depuración
- Flare del Agent
- Estado del check del Agent
- Problemas de NTP
- Problemas de permisos
- Problemas de integraciones
- Problemas del sitio
- Problemas de Autodiscovery
- Problemas de contenedores de Windows
- Configuración del tiempo de ejecución del Agent
- Consumo elevado de memoria o CPU
- Guías
- Seguridad de datos
- Integraciones
- Desarrolladores
- Autorización
- DogStatsD
- Checks personalizados
- Integraciones
- Build an Integration with Datadog
- Crear una integración basada en el Agent
- Crear una integración API
- Crear un pipeline de logs
- Referencia de activos de integración
- Crear una oferta de mercado
- Crear un dashboard de integración
- Create a Monitor Template
- Crear una regla de detección Cloud SIEM
- Instalar la herramienta de desarrollo de integraciones del Agente
- Checks de servicio
- Complementos de IDE
- Comunidad
- Guías
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Aplicación móvil de Datadog
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- En la aplicación
- Dashboards
- Notebooks
- Editor DDSQL
- Reference Tables
- Hojas
- Monitores y alertas
- Watchdog
- Métricas
- Bits AI
- Internal Developer Portal
- Error Tracking
- Explorador
- Estados de problemas
- Detección de regresión
- Suspected Causes
- Error Grouping
- Bits AI Dev Agent
- Monitores
- Issue Correlation
- Identificar confirmaciones sospechosas
- Auto Assign
- Issue Team Ownership
- Rastrear errores del navegador y móviles
- Rastrear errores de backend
- Manage Data Collection
- Solucionar problemas
- Guides
- Change Tracking
- Gestión de servicios
- Objetivos de nivel de servicio (SLOs)
- Gestión de incidentes
- De guardia
- Status Pages
- Gestión de eventos
- Gestión de casos
- Actions & Remediations
- Infraestructura
- Cloudcraft
- Catálogo de recursos
- Universal Service Monitoring
- Hosts
- Contenedores
- Processes
- Serverless
- Monitorización de red
- Cloud Cost
- Rendimiento de las aplicaciones
- APM
- Términos y conceptos de APM
- Instrumentación de aplicación
- Recopilación de métricas de APM
- Configuración de pipelines de trazas
- Correlacionar trazas (traces) y otros datos de telemetría
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilidad del servicio
- Endpoint Observability
- Instrumentación dinámica
- Live Debugger
- Error Tracking
- Seguridad de los datos
- Guías
- Solucionar problemas
- Límites de tasa del Agent
- Métricas de APM del Agent
- Uso de recursos del Agent
- Logs correlacionados
- Stacks tecnológicos de llamada en profundidad PHP 5
- Herramienta de diagnóstico de .NET
- Cuantificación de APM
- Go Compile-Time Instrumentation
- Logs de inicio del rastreador
- Logs de depuración del rastreador
- Errores de conexión
- Continuous Profiler
- Database Monitoring
- Gastos generales de integración del Agent
- Arquitecturas de configuración
- Configuración de Postgres
- Configuración de MySQL
- Configuración de SQL Server
- Configuración de Oracle
- Configuración de MongoDB
- Setting Up Amazon DocumentDB
- Conexión de DBM y trazas
- Datos recopilados
- Explorar hosts de bases de datos
- Explorar métricas de consultas
- Explorar ejemplos de consulta
- Exploring Database Schemas
- Exploring Recommendations
- Solucionar problemas
- Guías
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Experiencia digital
- Real User Monitoring
- Pruebas y monitorización de Synthetics
- Continuous Testing
- Análisis de productos
- Entrega de software
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Configuración
- Network Settings
- Tests en contenedores
- Repositories
- Explorador
- Monitores
- Test Health
- Flaky Test Management
- Working with Flaky Tests
- Test Impact Analysis
- Flujos de trabajo de desarrolladores
- Cobertura de código
- Instrumentar tests de navegador con RUM
- Instrumentar tests de Swift con RUM
- Correlacionar logs y tests
- Guías
- Solucionar problemas
- Code Coverage
- Quality Gates
- Métricas de DORA
- Feature Flags
- Seguridad
- Información general de seguridad
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- Observabilidad de la IA
- Log Management
- Observability Pipelines
- Gestión de logs
- CloudPrem
- Administración
- Gestión de cuentas
- Seguridad de los datos
- Ayuda
Library Inventory
Este producto no es compatible con el sitio Datadog seleccionado. ().
Esta página aún no está disponible en español. Estamos trabajando en su traducción.
Si tienes alguna pregunta o comentario sobre nuestro actual proyecto de traducción, no dudes en ponerte en contacto con nosotros.
Si tienes alguna pregunta o comentario sobre nuestro actual proyecto de traducción, no dudes en ponerte en contacto con nosotros.
The Library Inventory provides a unified view of all third-party libraries detected across your codebase and services. It helps you understand which components you depend on, which versions are in use, and where vulnerabilities or license risks might exist. The inventory is built from two complementary data sources:
- Static Software Composition Analysis (Static SCA), which scans your repositories to identify every library referenced in your source code.
- Runtime Software Composition Analysis (Runtime SCA), which detects libraries that are actually loaded and used at runtime by your services. This combined visibility helps you distinguish between theoretical dependencies and real risk exposure.
Static view
The Static view lists all libraries referenced in your repositories as detected by Static SCA.
Static SCA analyzes dependency files and source code to identify all declared third-party libraries, regardless of whether they are used at runtime. Use this view to:
- See your complete dependency footprint
- Identify libraries present in specific repositories
- Track dependency versions and upgrade needs
- Explore vulnerabilities and license metadata for all referenced libraries
Static data updates on every repository scan.
Runtime view
The Runtime view lists only the libraries actively used by your services in production or other monitored environments, as detected by Runtime SCA.
Runtime SCA observes loaded dependencies through the Datadog tracing library, enabling you to:
- Prioritize vulnerabilities in libraries that are actually executed
- Reduce noise by filtering out unused dependencies
- Understand real exposure to vulnerable components
- Map vulnerable libraries to the services and environments using them
This view updates continuously as your services run.
Library details
Clicking any library in the inventory opens the library detail panel, which provides an in-depth view of its metadata, vulnerabilities, and usage.
The panel includes the following sections.
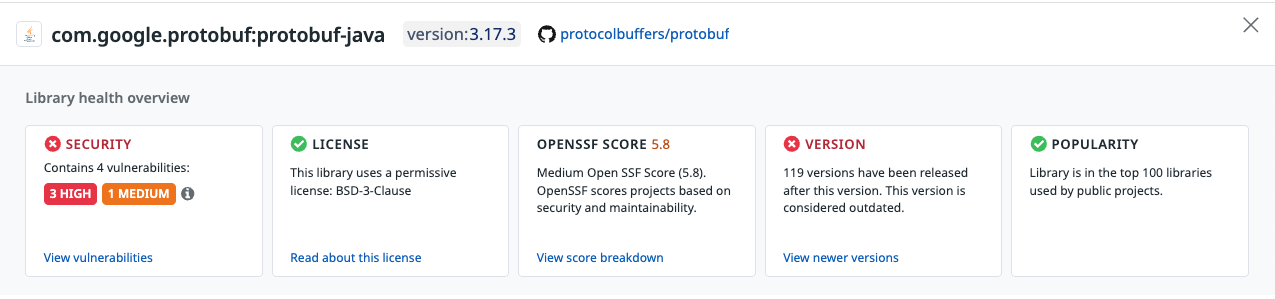
Overview
Displays key information about the selected library and version, including:
- Security status (count of Critical, High, Medium, Low vulnerabilities)
- License type
- Version status (older version, actively maintained, deprecated, etc.)
- Popularity and download statistics when available
This section provides a snapshot of the security and maintenance posture of the dependency.
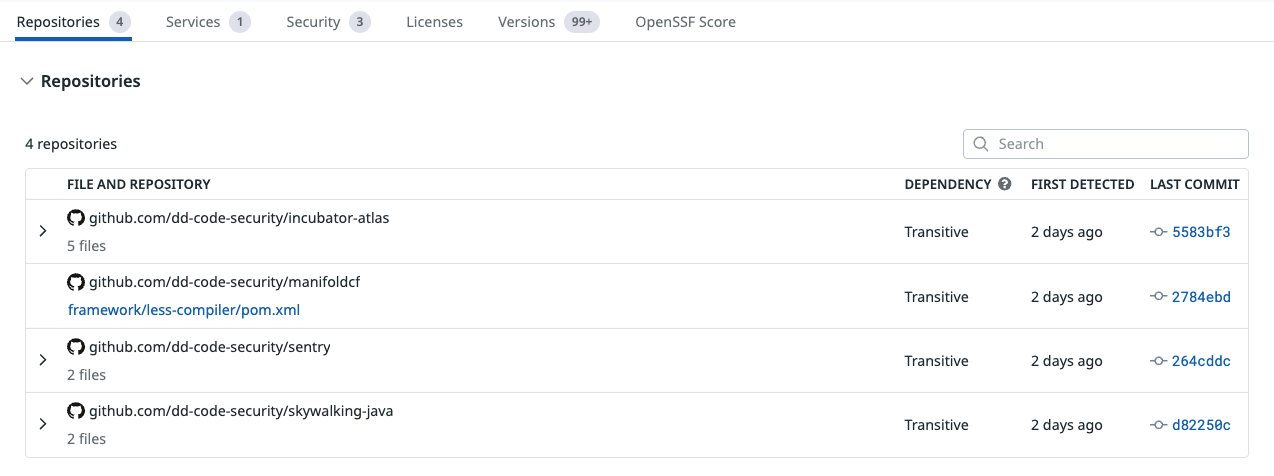
Repositories
Shows all repositories where this library is referenced, as detected by Static SCA.
For each repository, you can see:
- The file and path where the dependency was declared
- Whether the dependency is direct or transitive
- The first detection timestamp
- The latest scanned commit
Use this view to understand how widely the library is used across your codebase.
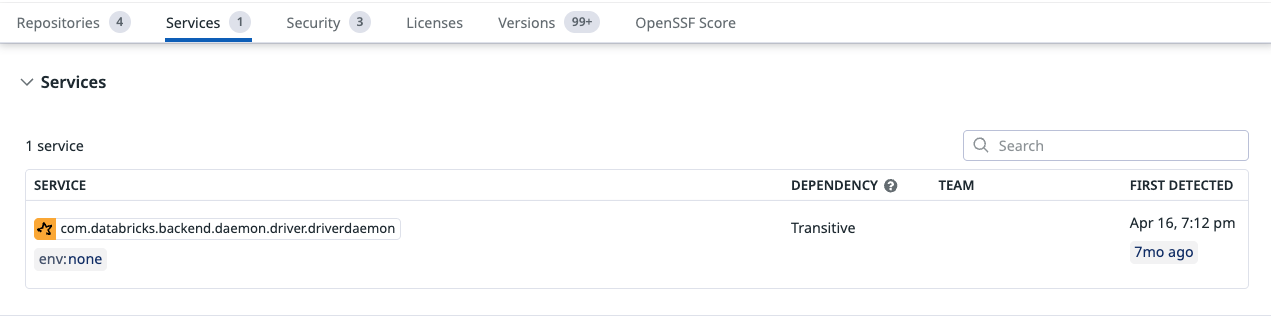
Services
Shows all services that load this library at runtime, as detected by Runtime SCA.
For each service, you can view:
- The environments where it is running (for example, env:dev, env:prod)
- The team responsible (when available)
- The first time the library was detected in that service
If no services appear, the library is referenced statically but not used at runtime.
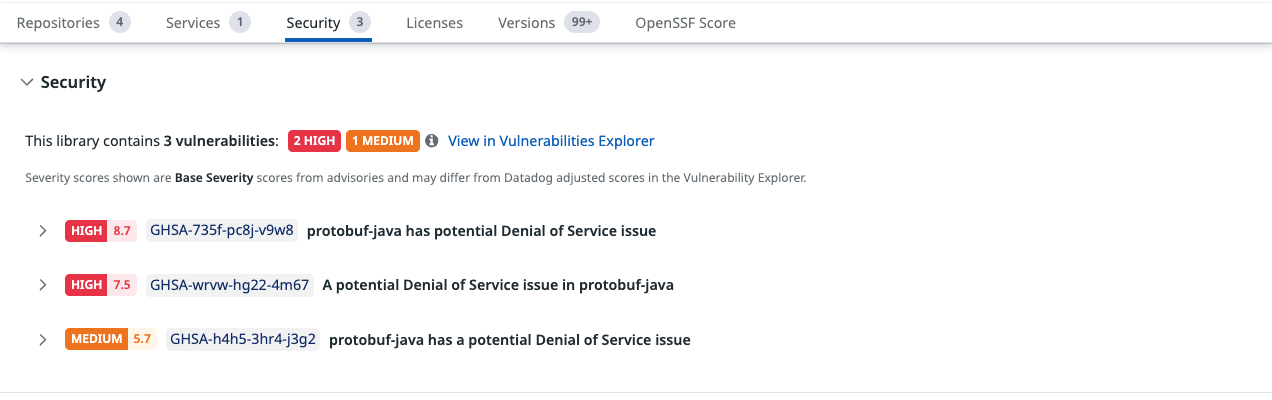
Security
Lists all known vulnerabilities affecting this library version, including:
- Severity (Critical, High, Medium, Low)
- CVE or advisory ID (for example, GHSA identifiers)
- A short description of each vulnerability
- Links to the full vulnerability details
This section consolidates all vulnerabilities detected by Datadog from upstream security advisories.
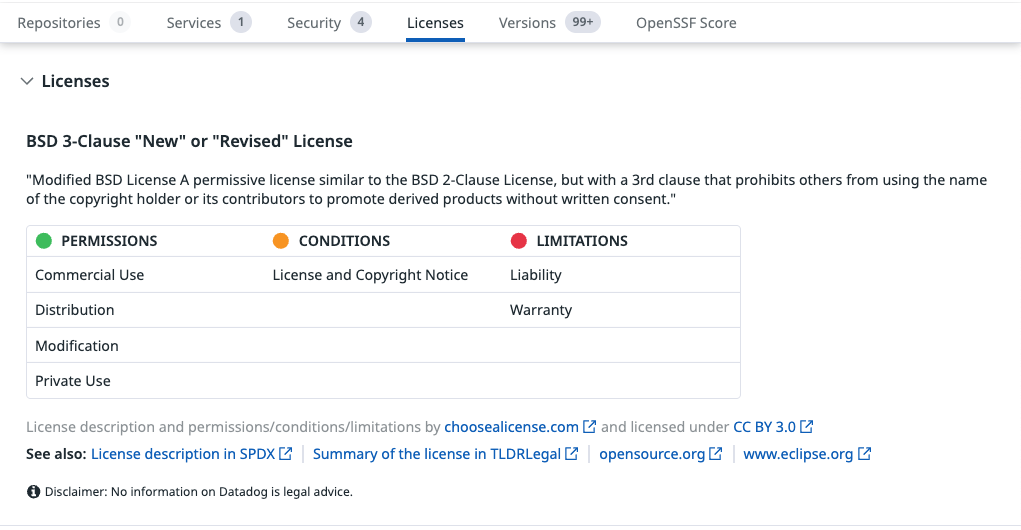
Licenses
The license table in this section is based on the Choose a License Appendix: https://choosealicense.com/appendix/
It summarizes the license’s:
- Permissions
Conditions - Limitations
Additionally, Datadog identifies license risks, including:
- Network copyleft: code must be released when offered as a network service
- Strong copyleft: derivative work must be open-sourced under the same license
- Non-standard copyleft: copyleft terms differ from common OSI-approved patterns
- Non-commercial: use is restricted to non-commercial contexts
- Non-standard / Non-free: license does not meet standard open-source definitions
Each risk contains a short explanation and links to more detailed license information.
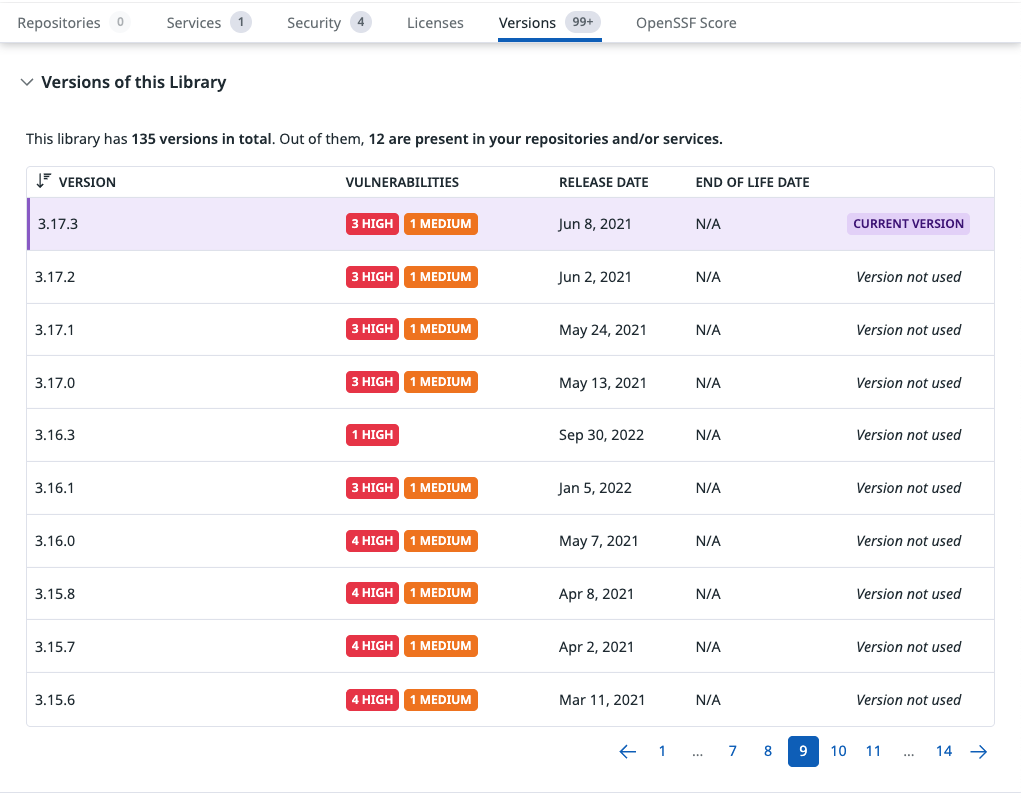
Versions
Lists all known versions of the library, along with:
- Release dates
- Vulnerability counts for each version
- Whether the version is used in your repositories or services
This helps you evaluate remediation options and identify safer upgrade paths.
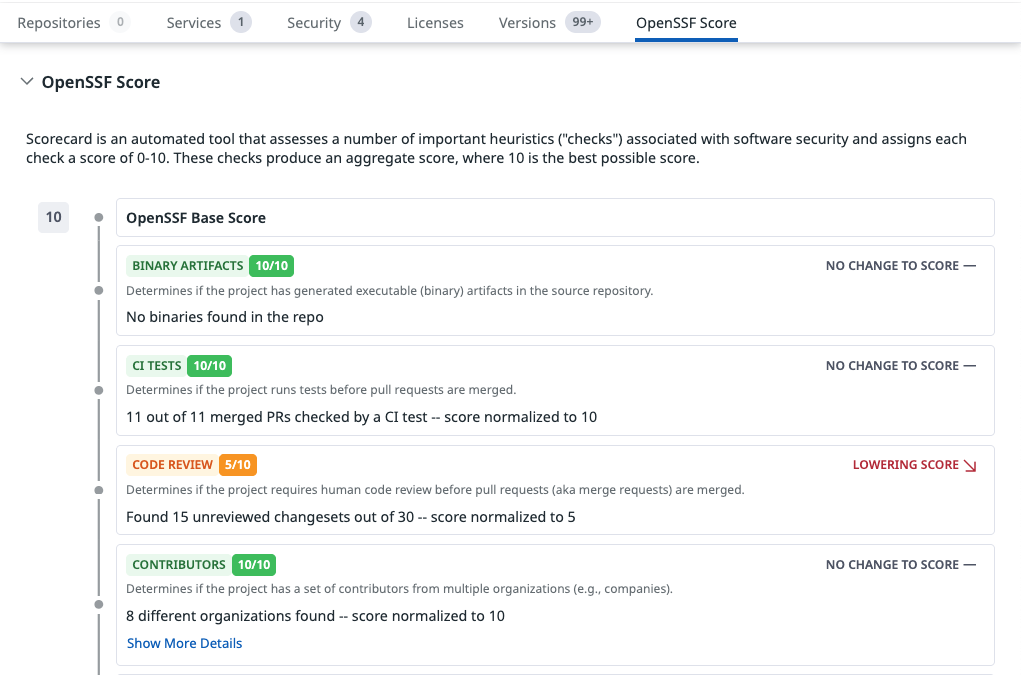
OpenSSF score
Displays the OpenSSF Scorecard results for the upstream project. Each check provides insight into the project’s security maturity, such as:
- Maintenance activity
- Use of security policies
- Safe workflow practices
- Dependency pinning
- Binary artifact usage
The score ranges from 0 to 10, where 10 indicates best practices.
Next steps
To get started with Library Inventory:
- Enable Static SCA to detect libraries in your repositories. See static setup to get started.
- Enable Runtime SCA to identify libraries actually used during execution. See runtime setup to get started.
- Use both views together to understand both your full dependency footprint and your real runtime exposure.