- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
Configure SCIM with Microsoft Entra ID
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
SCIM is available with the Infrastructure Pro and Infrastructure Enterprise plans.
Due to a Microsoft freeze on third-party app updates in Entra following a security incident in late 2024, Team provisioning via SCIM is unavailable. To create Teams in Datadog, use one of the supported alternatives:
SAML mapping,
Terraform,
the public API, or
direct calls to the SCIM server. SCIM can still be used to provision users.
See the following instructions to synchronize your Datadog users with Microsoft Entra ID using SCIM.
For capabilities and limitations of this feature, see SCIM.
Prerequisites
SCIM in Datadog is an advanced feature available with the Infrastructure Pro and Infrastructure Enterprise plans.
This documentation assumes your organization manages user identities using an identity provider.
Datadog strongly recommends that you use a service account application key when configuring SCIM to avoid any disruption in access. For further details, see using a service account with SCIM.
When using SAML and SCIM together, Datadog strongly recommends disabling SAML just-in-time (JIT) provisioning to avoid discrepancies in access. Manage user provisioning through SCIM only.
Add Datadog to the Microsoft Entra ID application gallery
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator
- Browse to Identity -> Applications -> Enterprise Applications
- Click New Application
- Type “Datadog” in the search box
- Select the Datadog application from the gallery
- Optionally, enter a name in the Name text box
- Click Create
Note: If you already have Datadog configured with Microsoft Entra ID for SSO, go to Enterprise Applications and select your existing Datadog application.
Configure automatic user provisioning
- In the application management screen, select Provisioning in the left panel
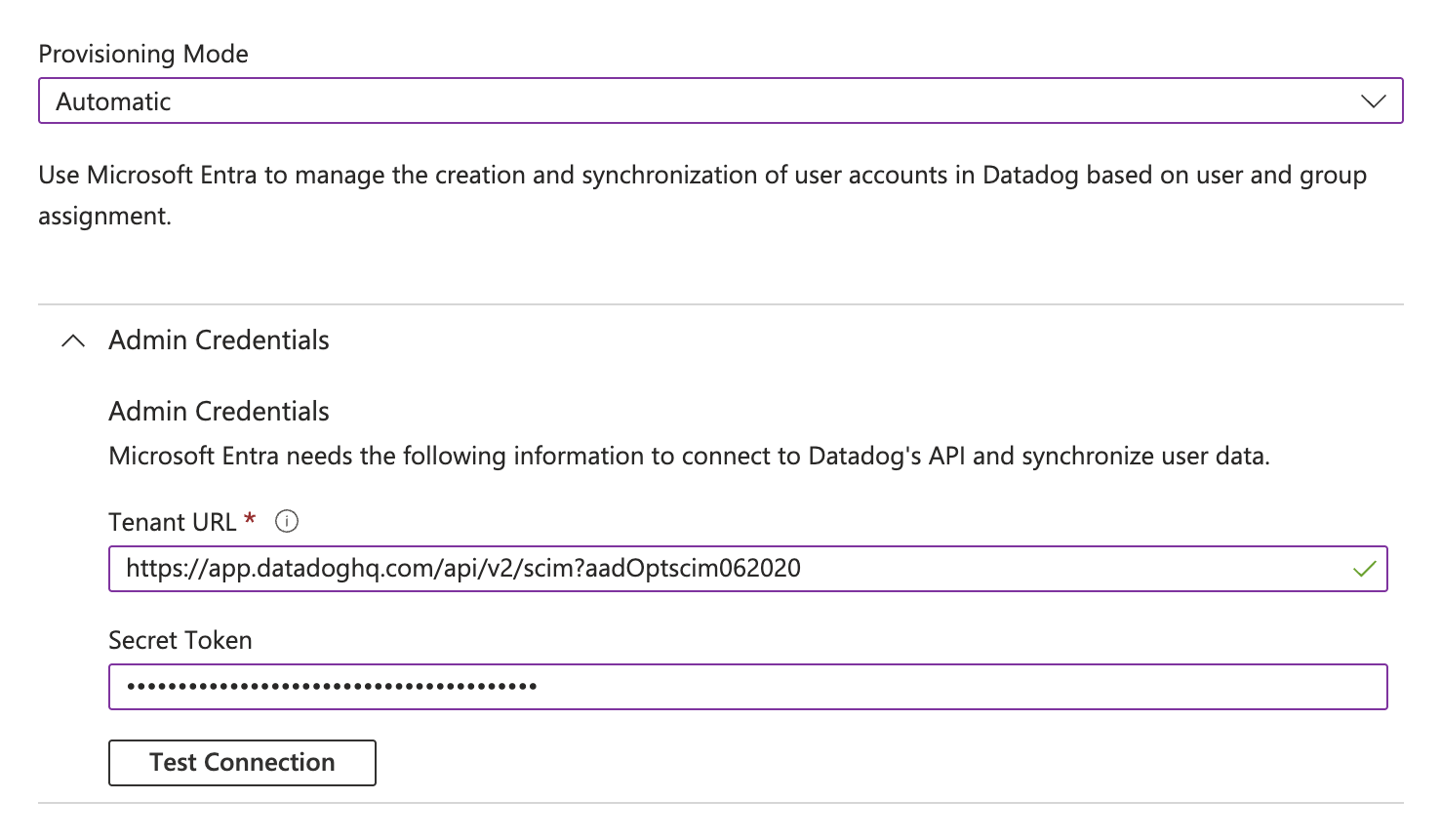
- In the Provisioning Mode menu, select Automatic
- Open Admin Credentials
- Complete the Admin Credentials section as follows:
- Tenant URL:
https:///api/v2/scim?aadOptscim062020- Note: Use the appropriate subdomain for your site. To find your URL, see Datadog sites.
- Note: The
?aadOptscim062020part of the Tenant URL is specifically for Entra ID. This is a flag that tells Entra to correct its SCIM behavior as outlined in this Microsoft Entra documentation. If you are not using Entra ID, you should not include this suffix on the URL.
- Secret Token: Use a valid Datadog application key. You can create an application key on your organization settings page. To maintain continuous access to your data, use a service account application key.
- Tenant URL:
- Click Test Connection, and wait for the message confirming that the credentials are authorized to enable provisioning.
- Click Save. The mapping section appears. See the following section to configure mapping.
Attribute mapping
User attributes
Expand the Mappings section
Click Provision Azure Active Directory Users. The Attribute Mapping page appears.
Set Enabled to Yes
Click the Save icon
Under Target Object actions, ensure Create, Update, and Delete actions are selected
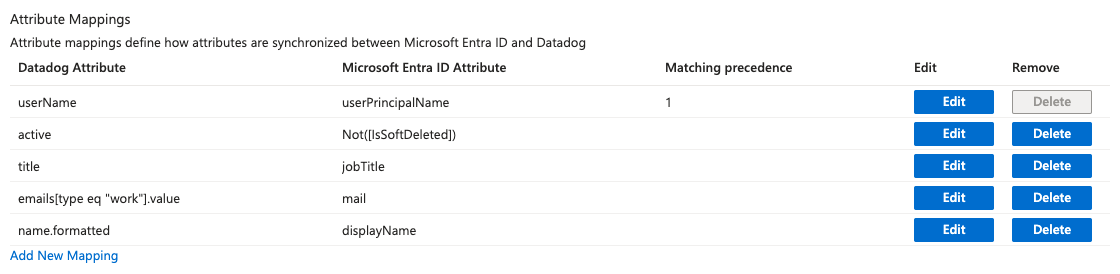
Review the user attributes that are synchronized from Microsoft Entra ID to Datadog in the attribute mapping section. Set the following mappings:
Microsoft Entra ID Attribute Datadog Attribute userPrincipalNameuserNameNot([IsSoftDeleted])activejobTitletitlemailemails[type eq "work"].valuedisplayNamename.formattedAfter you set your mappings, click Save.
Group attributes
Group mapping is not supported.