- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
Configuring Single Sign-On With SAML
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
Overview
This page covers how to enable single sign-on (SSO) with SAML in Datadog, as well as how enterprise customers can enable multiple SAML identity providers (IdPs).
Notes:
- If you don’t have SAML enabled on your Datadog account, reach out to support to enable it.
- This documentation assumes that you already have a SAML Identity Provider (IdP). If you do not have a SAML IdP, there are several IdPs that have integrations with Datadog such as Active Directory, Auth0, Google, LastPass, Microsoft Entra ID, Okta, and SafeNet.
- SAML configuration requires Datadog Administrator access, or the
Org Managementpermission if you’re using custom roles.
- This documentation assumes that you already have a SAML Identity Provider (IdP). If you do not have a SAML IdP, there are several IdPs that have integrations with Datadog such as Active Directory, Auth0, Google, LastPass, Microsoft Entra ID, Okta, and SafeNet.
- SAML configuration requires Datadog Administrator access, or the
Org Managementpermission if you’re using custom roles.
Configuring SAML
To begin configuration, see your IdP’s documentation:
Download Datadog’s Service Provider metadata to configure your IdP to recognize Datadog as a Service Provider.
In Datadog, hover over your username in the bottom left corner and select Organization Settings. Select Login Methods and click Configure under SAML.
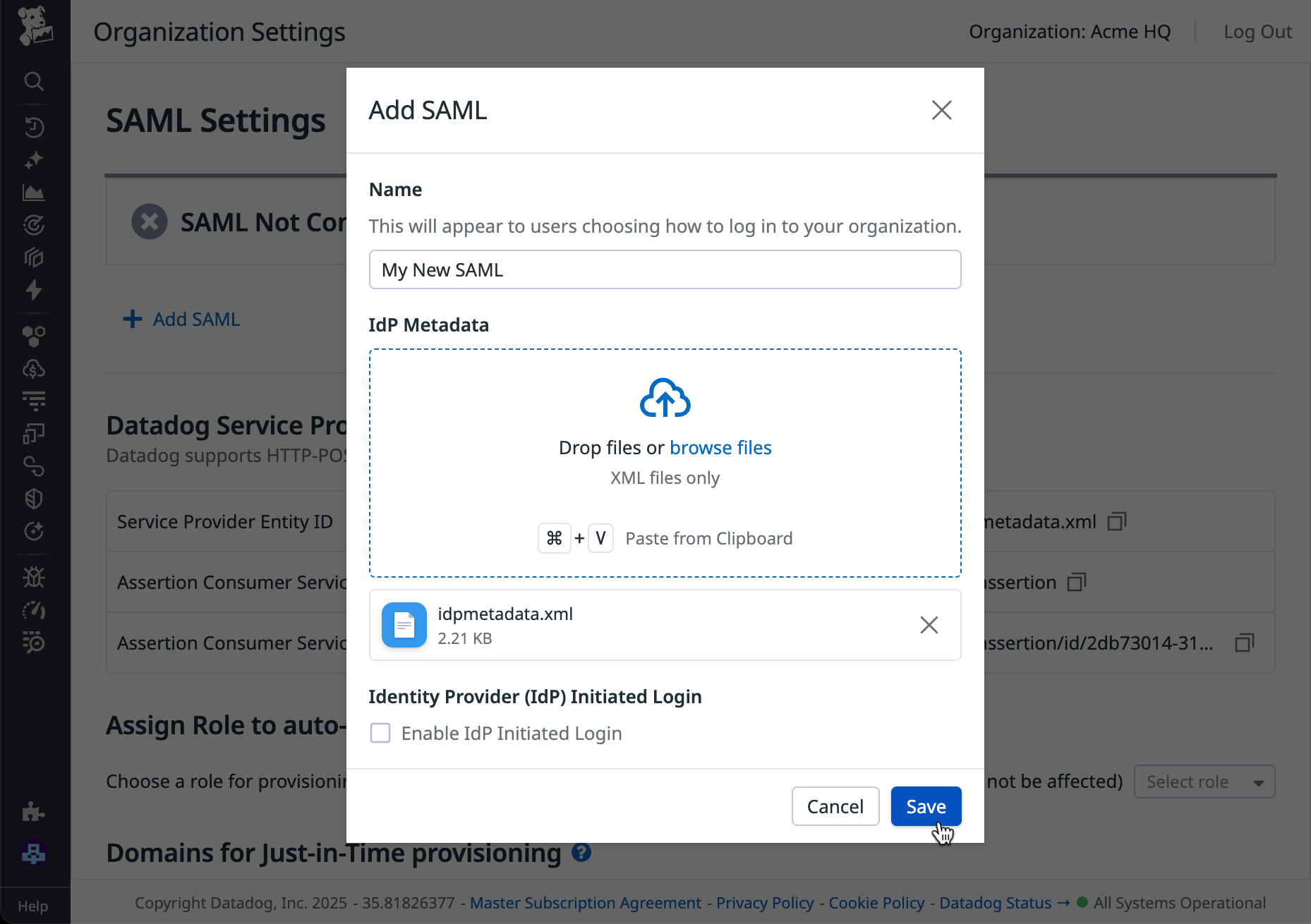
Click Add SAML.
In the configuration modal:
- Create a user-friendly name for this SAML provider. The name appears to end users when they choose a login method.
- Upload the IdP metadata from your SAML identity provider by clicking browse files or dragging and dropping the XML metadata file onto the modal.The IdP metadata must contain ASCII characters only.
Click Save.
Note: To configure SAML for a multi-org, see Managing Multiple-Organization Accounts.
Configuring multiple SAML providers
Enterprise customers can have multiple SAML configurations per organization (up to three at the same time). This feature simplifies identity management across complex environments, such as during IdP changes, mergers, or contractor onboarding.
To configure additional SAML providers:
Navigate to Organization Settings > Login Methods. Under SAML, click Update, then Add SAML.
In the configuration modal:
- Create a user-friendly name for this SAML provider. The name appears to end users when they choose a login method.All users can see and access all configured IdPs; there is no way to assign specific user groups to specific configurations. Setting clear and descriptive names for each provider helps users select the appropriate IdP during login. Also note that there is no way to set a default configuration.
- Upload the IdP metadata from your SAML identity provider by clicking browse files or dragging and dropping the XML metadata file onto the modal.
- Create a user-friendly name for this SAML provider. The name appears to end users when they choose a login method.
Click Save.
Role mapping with multiple SAML providers
If you use SAML role mapping or team mapping and want to use the same mappings in any additional providers you add, make sure the attributes in the new IdP(s) match what is defined in your mappings. If you add a new IdP, make sure to either use the same attribute names as your existing IdP, or add new mappings that align with the new IdP’s attributes to ensure roles and teams are assigned correctly when users log in with different IdPs.