- Esenciales
- Empezando
- Agent
- API
- Rastreo de APM
- Contenedores
- Dashboards
- Monitorización de bases de datos
- Datadog
- Sitio web de Datadog
- DevSecOps
- Gestión de incidencias
- Integraciones
- Internal Developer Portal
- Logs
- Monitores
- OpenTelemetry
- Generador de perfiles
- Session Replay
- Security
- Serverless para Lambda AWS
- Software Delivery
- Monitorización Synthetic
- Etiquetas (tags)
- Workflow Automation
- Centro de aprendizaje
- Compatibilidad
- Glosario
- Atributos estándar
- Guías
- Agent
- Arquitectura
- IoT
- Plataformas compatibles
- Recopilación de logs
- Configuración
- Automatización de flotas
- Solucionar problemas
- Detección de nombres de host en contenedores
- Modo de depuración
- Flare del Agent
- Estado del check del Agent
- Problemas de NTP
- Problemas de permisos
- Problemas de integraciones
- Problemas del sitio
- Problemas de Autodiscovery
- Problemas de contenedores de Windows
- Configuración del tiempo de ejecución del Agent
- Consumo elevado de memoria o CPU
- Guías
- Seguridad de datos
- Integraciones
- Desarrolladores
- Autorización
- DogStatsD
- Checks personalizados
- Integraciones
- Build an Integration with Datadog
- Crear una integración basada en el Agent
- Crear una integración API
- Crear un pipeline de logs
- Referencia de activos de integración
- Crear una oferta de mercado
- Crear un dashboard de integración
- Create a Monitor Template
- Crear una regla de detección Cloud SIEM
- Instalar la herramienta de desarrollo de integraciones del Agente
- Checks de servicio
- Complementos de IDE
- Comunidad
- Guías
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Aplicación móvil de Datadog
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- En la aplicación
- Dashboards
- Notebooks
- Editor DDSQL
- Reference Tables
- Hojas
- Monitores y alertas
- Watchdog
- Métricas
- Bits AI
- Internal Developer Portal
- Error Tracking
- Explorador
- Estados de problemas
- Detección de regresión
- Suspected Causes
- Error Grouping
- Bits AI Dev Agent
- Monitores
- Issue Correlation
- Identificar confirmaciones sospechosas
- Auto Assign
- Issue Team Ownership
- Rastrear errores del navegador y móviles
- Rastrear errores de backend
- Manage Data Collection
- Solucionar problemas
- Guides
- Change Tracking
- Gestión de servicios
- Objetivos de nivel de servicio (SLOs)
- Gestión de incidentes
- De guardia
- Status Pages
- Gestión de eventos
- Gestión de casos
- Actions & Remediations
- Infraestructura
- Cloudcraft
- Catálogo de recursos
- Universal Service Monitoring
- Hosts
- Contenedores
- Processes
- Serverless
- Monitorización de red
- Cloud Cost
- Rendimiento de las aplicaciones
- APM
- Términos y conceptos de APM
- Instrumentación de aplicación
- Recopilación de métricas de APM
- Configuración de pipelines de trazas
- Correlacionar trazas (traces) y otros datos de telemetría
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilidad del servicio
- Endpoint Observability
- Instrumentación dinámica
- Live Debugger
- Error Tracking
- Seguridad de los datos
- Guías
- Solucionar problemas
- Límites de tasa del Agent
- Métricas de APM del Agent
- Uso de recursos del Agent
- Logs correlacionados
- Stacks tecnológicos de llamada en profundidad PHP 5
- Herramienta de diagnóstico de .NET
- Cuantificación de APM
- Go Compile-Time Instrumentation
- Logs de inicio del rastreador
- Logs de depuración del rastreador
- Errores de conexión
- Continuous Profiler
- Database Monitoring
- Gastos generales de integración del Agent
- Arquitecturas de configuración
- Configuración de Postgres
- Configuración de MySQL
- Configuración de SQL Server
- Configuración de Oracle
- Configuración de MongoDB
- Setting Up Amazon DocumentDB
- Conexión de DBM y trazas
- Datos recopilados
- Explorar hosts de bases de datos
- Explorar métricas de consultas
- Explorar ejemplos de consulta
- Exploring Database Schemas
- Exploring Recommendations
- Solucionar problemas
- Guías
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Experiencia digital
- Real User Monitoring
- Pruebas y monitorización de Synthetics
- Continuous Testing
- Análisis de productos
- Entrega de software
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Configuración
- Network Settings
- Tests en contenedores
- Repositories
- Explorador
- Monitores
- Test Health
- Flaky Test Management
- Working with Flaky Tests
- Test Impact Analysis
- Flujos de trabajo de desarrolladores
- Cobertura de código
- Instrumentar tests de navegador con RUM
- Instrumentar tests de Swift con RUM
- Correlacionar logs y tests
- Guías
- Solucionar problemas
- Code Coverage
- Quality Gates
- Métricas de DORA
- Feature Flags
- Seguridad
- Información general de seguridad
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- Observabilidad de la IA
- Log Management
- Observability Pipelines
- Gestión de logs
- CloudPrem
- Administración
- Gestión de cuentas
- Seguridad de los datos
- Ayuda
cert-manager
Supported OS
Versión de la integración5.3.0
Información general
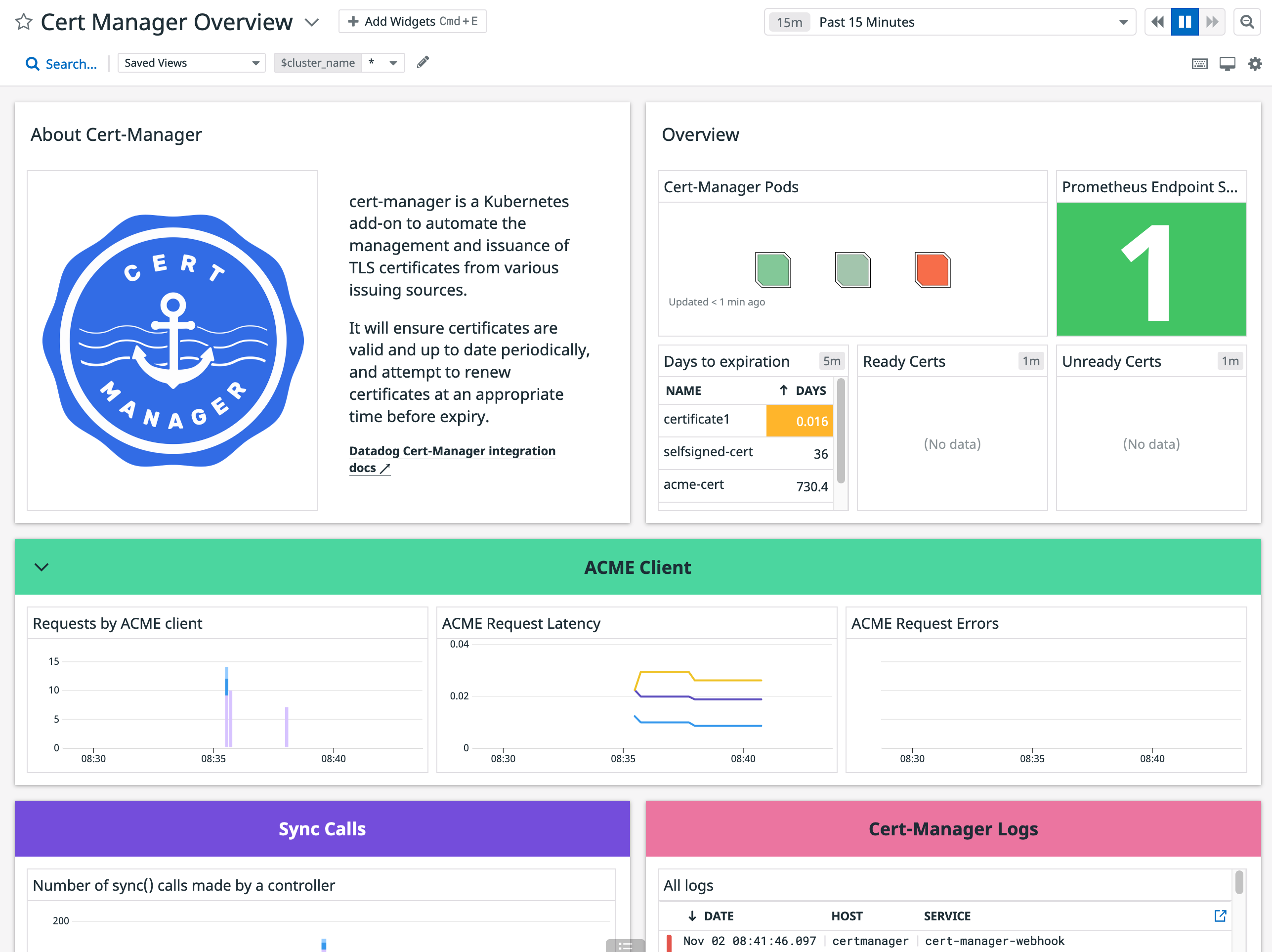
Este check recopila métricas de cert-manager.
Configuración
Sigue las instrucciones a continuación para instalar y configurar este check para un Agent que se ejecuta en un host. Para entornos en contenedores, consulta las plantillas de integración de Autodiscovery para obtener orientación sobre la aplicación de estas instrucciones.
Instalación
El check de cert_manager está incluido en el paquete del Datadog Agent. No es necesaria ninguna instalación adicional en tu servidor.
Configuración
Edita el archivo
cert_manager.d/conf.yaml, que se encuentra en la carpetaconf.d/en la raíz del directorio de configuración del Agent, para empezar a recopilar los datos de rendimiento de tu cert_manager. Para conocer todas las opciones de configuración disponibles, consulta el cert_manager.d/conf.yaml de ejemplo.
Validación
Ejecuta el subcomando de estado del Agent y busca cert_manager en la sección Checks.
Datos recopilados
Métricas
| cert_manager.certificate.expiration_timestamp (gauge) | The date after which the certificate expires. Expressed as a Unix Epoch Time Shown as second |
| cert_manager.certificate.ready_status (gauge) | The ready status of the certificate |
| cert_manager.certificate.renewal_timestamp (gauge) | The date at which the certificate will be renewed. Expressed as a Unix Epoch Time Shown as second |
| cert_manager.clock_time (gauge) | The clock time given in seconds (from 1970/01/01 UTC) Shown as second |
| cert_manager.controller.sync_call.count (count) | The number of sync() calls made by a controller |
| cert_manager.http_acme_client.request.count (count) | The number of requests made by the ACME client |
| cert_manager.http_acme_client.request.duration.count (count) | The count of the HTTP request latencies in seconds for the ACME client |
| cert_manager.http_acme_client.request.duration.quantile (gauge) | The quantiles of the HTTP request latencies in seconds for the ACME client |
| cert_manager.http_acme_client.request.duration.sum (count) | The sum of the HTTP request latencies in seconds for the ACME client |
Eventos
La integración de cert_manager no incluye ningún evento.
Checks de servicio
cert_manager.openmetrics.health
Returns CRITICAL if the agent fails to connect to the OpenMetrics endpoint, otherwise OK.
Statuses: ok, critical
Solucionar problemas
Duplicar etiquetas (tags) de nombre
Cada nombre de certificado se expone dentro de la etiqueta name en la carga útil de Prometheus y el Datadog Agent lo convierte en una etiqueta. Si tus hosts también usan la etiqueta name (por ejemplo, recopilada automáticamente por la integración de AWS), las métricas provenientes de esta integración presentarán ambos valores. Para evitar etiquetas name duplicadas, puedes usar el parámetro de configuración rename_labels para asignar la etiqueta name de Prometheus a la etiqueta cert_name de Datadog. Esto garantiza que tengas un solo valor dentro de la etiqueta cert_name para identificar tus certificados:
init_config:
instances:
- openmetrics_endpoint: <OPENMETRICS_ENDPOINT>
rename_labels:
name: cert_name
¿Necesitas más ayuda? Ponte en contacto con el servicio de asistencia de Datadog.
