- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
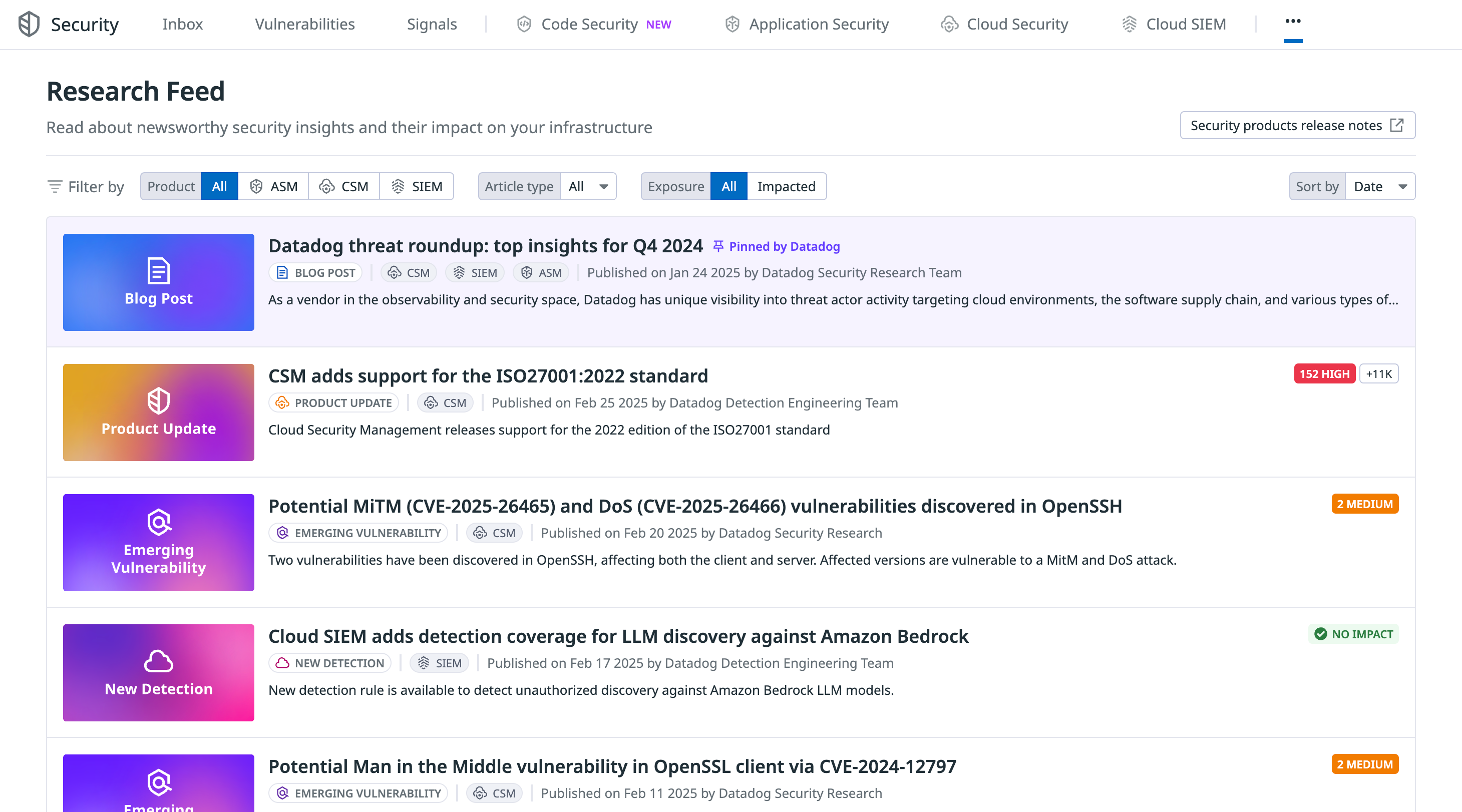
Security Research Feed
Datadog の Security Research Feed は、セキュリティ関連コンテンツを継続的に更新し、組織が新たに出現する脅威や脆弱性に先回りして備えられるよう支援します。Datadog のセキュリティ リサーチ チームとディテクション エンジニアリング チームが運用し、重要なセキュリティ動向についてタイムリーな知見を提供します。内容には、次のようなものが含まれます:
- Emerging vulnerabilities and threats: インフラに影響し得る、新たに発見された脆弱性や現在進行中の攻撃キャンペーンに関する更新です。これらの更新により、セキュリティ チームは検知カバレッジを評価し、影響を受けるシステムを特定し、想定される影響を見積もれます。
- New detection content: Datadog のディテクション エンジニアリング チームがリリースした最新の検知です。新しい戦術、技術、手順 (TTP) や、対応しているディテクション パックも含まれます。
- Product updates: Datadog のセキュリティ機能の強化に関する更新です。環境の監視と保護を、より確実に行えるようにします。
仕組み
セキュリティ リサーチ チームとディテクション エンジニアリング チームは、脅威の状況を継続的に監視し、新たな脅威が現れ次第、すぐに更新を公開します。これにより、セキュリティ担当者は次の情報を迅速に入手できます。
- 最新のセキュリティ トレンドに関する専門的な分析
- 脆弱性や脅威の影響を評価するためのコンテキスト情報
- 効果的な検知と対応戦略を実装するためのガイダンス
新たに登場した脆弱性の基準
新たに登場した脆弱性とは、ビジネス運用に重大な脅威をもたらし得る技術上のセキュリティ上の弱点を指し、次の基準の 1 つ以上を満たします:
- 広範な影響: 多数のシステムや組織に影響し、アタック サーフェスが広い状態を生み出します。
- 深刻度が高い: 悪用のしやすさや想定される被害の大きさから、直ちに対応すべきセキュリティ上の懸念となります。
- 注目度が高い: セキュリティ コミュニティや一般ニュースで広く取り上げられ、認知度と緊急度が高まっています。
新たに登場した脅威の基準
新たに登場した脅威とは、新規または進化中の攻撃キャンペーン、あるいはサプライ チェーン攻撃で、すでにビジネス運用に支障を与えた、または重大な脅威となっているものを指します。次の基準の 1 つ以上を満たします:
- 広範な影響: 広域の無差別攻撃、または標的型キャンペーンによって、すでに多数のシステムや組織に影響を与えています。
- 差し迫った脅威: すでに影響が出ている、または今後エスカレートすると見込まれ、近い将来、多くの組織が攻撃を受ける可能性があります。
- 注目度が高い: セキュリティ コミュニティや一般ニュースで広く取り上げられ、認知度と緊急度が高まっています。