- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
IOC Explorer
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
The IOC Explorer is in Preview.
Overview
Indicators of Compromise (IOC) are evidence that your systems have experienced a security breach. With the IOC Explorer, you can view more details about compromises, and see related signals and logs.
Prerequisites
To view data in the IOC Explorer, all of the following must be true:
- Your organization must subscribe to Cloud SIEM.
- The indicator of compromise must be in a threat feed that was available to Datadog at the time of the log acquisition.
- For more information on the threat intelligence feeds the IOC Explorer displays content from, see Threat intelligence sources.
- A log that has a matching entity in threat intelligence must be acquired.
- The time frame for the Explorer is fixed to the last 30 days. The log must be from within that time frame.
Use the IOC Explorer
To access the IOC Explorer in Datadog, go to Security > Cloud SIEM > Investigate > IOC Explorer.
Query and filter indicators of compromise
You can write custom queries or apply filters to determine which indicators of compromise you can see in the explorer. You can query or filter by:
Additionally, you can click a column heading in the Explorer to sort by that column’s values.
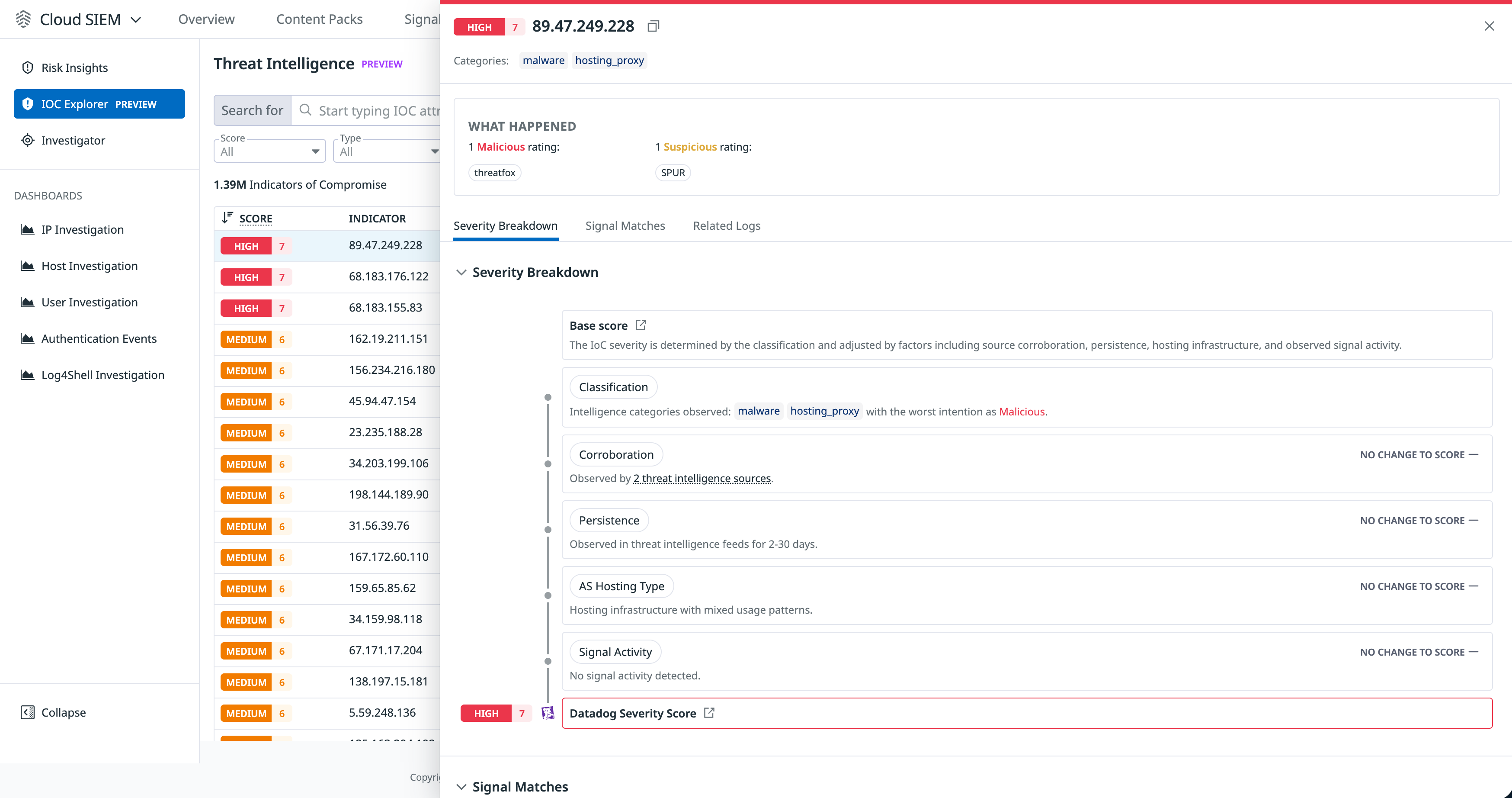
Get more context on an indicator of compromise
Click an indicator of compromise to open a side panel that contains additional information about it:
- When the indicator was first and last seen in a threat intelligence feedThis is distinct from the first or last time the indicator was seen in a log.
- Any categories and ratings assigned to it, and the threat intelligence feeds associated with those ratings
- A breakdown of the indicator’s severity score
- Signal matches, which you can view in Signals Explorer
- Related logs, which you can view in Log Explorer
Understand severity scoring
It’s important to have proper context for the severity score for an indicator, so you can properly prioritize investigations. For example, IP addresses can be volatile and require frequent reassessments as a result.
In the IOC Explorer side panel, you can see the factors that contribute to the severity score. Severity score starts from a base score based on classification, and increases or decreases based on additional factors:
- Classification: The base score associated with the indicator’s category and intent
- Corroboration: Whether the indicator appears on multiple threat intelligent feeds
- Persistence: How long threat intelligence feeds have been reporting on the indicator
- Hosting Type: Used for IP and domain entity types; evaluates whether the hosting infrastructure type is commonly used for attacks
- Signal Activity: Whether the indicator has been observed in Signals
Further reading
お役に立つドキュメント、リンクや記事: