- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
Sequence
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
Overview
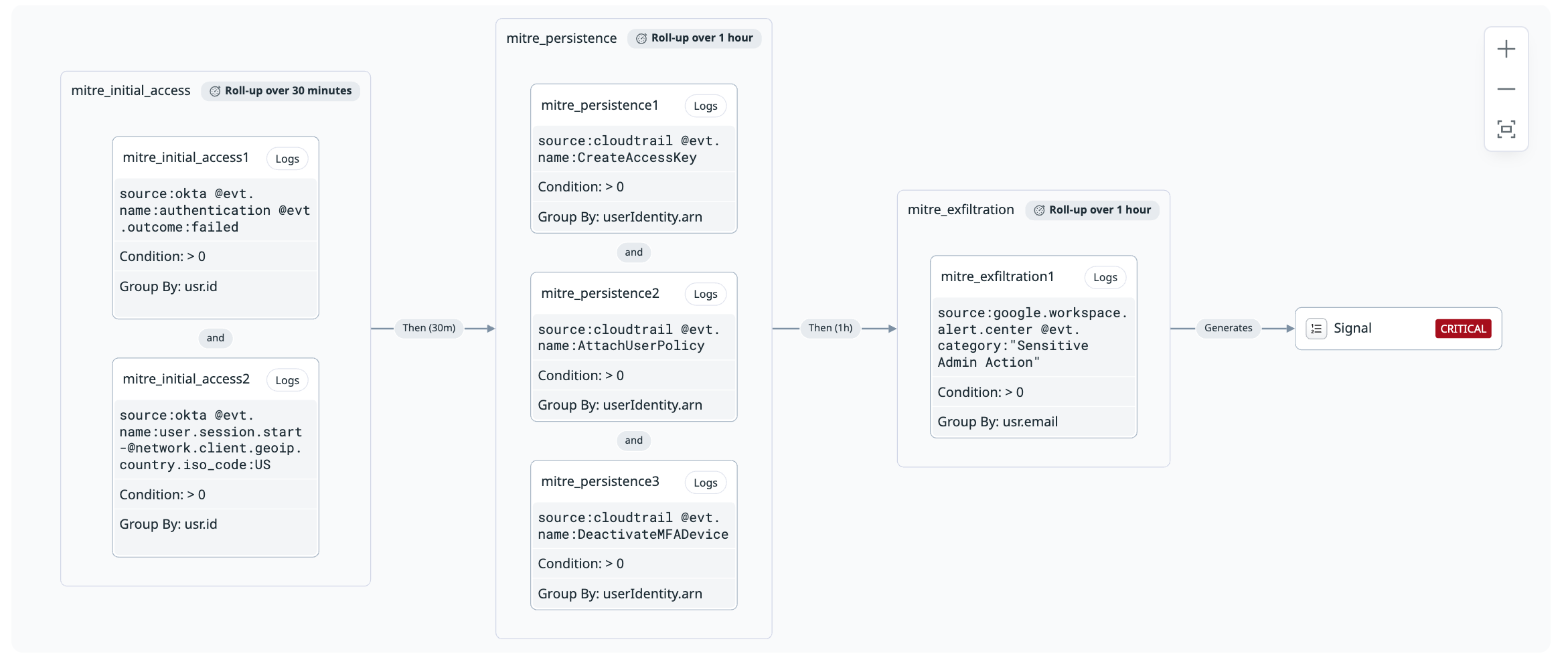
The sequence method enables you to detect multi-stage attacks by identifying ordered patterns of related events, such as initial access, privilege escalation, and data exfiltration.
You can define a sequence of steps that must occur within a defined time frame and across related entities, such as a user, host, or IP address. Each sequence can combine conditions from multiple logs or signals to identify coordinated activity that might be missed by individual rules.
See Create Rule for instructions on how to configure a sequence rule.
How the sequence method works
Detection logic
Sequence detection evaluates a defined series of steps that represent distinct stages of suspicious behavior. Each step corresponds to:
- A condition such as a threshold on a log query or a signal match
- Transitions that define the order and time constraints between steps
The rule is triggered when all steps occur in the specified order and within the configured time windows.
Linking entities
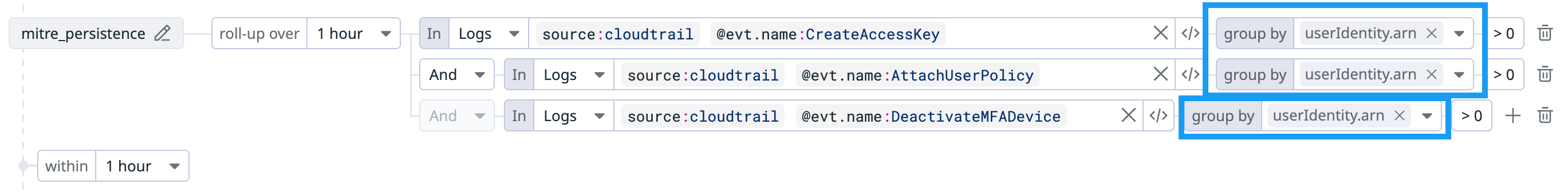
The sequence of steps can be correlated across users, accounts, IP addresses, and other fields to automatically track linked entities through group by fields. This allows you to follow an attacker’s path across different identities and systems.
Evaluation window
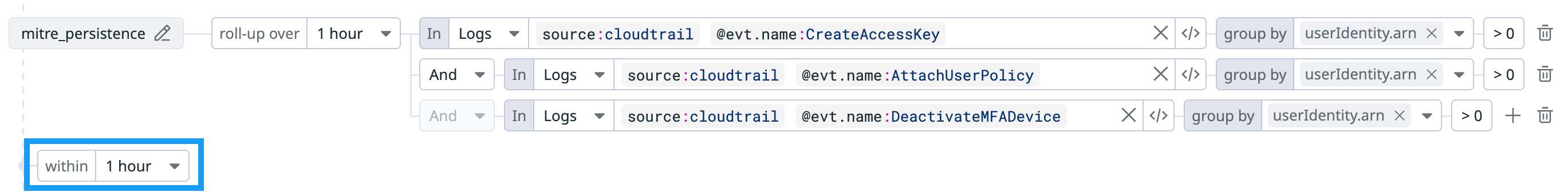
Each transition between steps has a configurable evaluation window that determines how long the rule waits for the next step to occur. For example, a rule might trigger when user login from an unusual location is followed within 20 minutes by a privilege escalation, where the user might have gone from a standard role to an admin role.
Configuration options
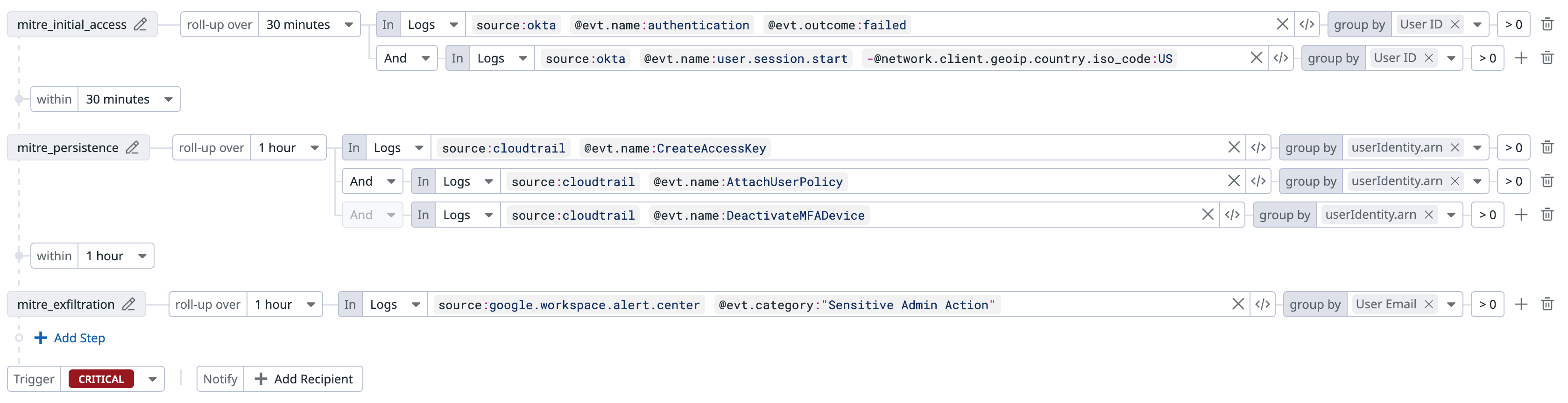
When you create a sequence detection rule, you can configure these options:
| Setting | Description | Impact |
|---|---|---|
| Data type | Specify whether each query evaluates logs, signals, or rules. | Defines data sources for detection. |
| Steps | Define each detection condition, including query and threshold. | Determines which behaviors are monitored. |
| Step transitions | Define the order and time relationship between steps. | Controls when a sequence qualifies for a signal. |
| Evaluation window | After a step has occurred, the time (in seconds) to wait for the next step. | Larger windows increase detection coverage, but may result in more noise. |
| Group by fields | Fields used to link activity across steps (for example, @usr.email, @ip). | Determines how entities are correlated across queries. |
Limits
- Sequence detection supports up to 10 steps per rule and a total evaluation window of 24 hours.
- Steps must be in a linear sequence.
Further reading
お役に立つドキュメント、リンクや記事: