- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
Network Configuration Management
This product is not supported for your selected Datadog site. ().
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
Network Configuration Management is in Preview. To request access and receive the custom Datadog Agent build, contact your Datadog representative.
Overview
Network Configuration Management (NCM) extends Network Device Monitoring (NDM) to include configuration awareness and change tracking. NCM allows you to:
- Monitor how device configurations change over time
- Compare two configuration versions side by side
- Use AI-generated summaries to understand changes and their potential impact during incidents
Note: NCM is read-only in Preview.
Prerequisites
- Network Device Monitoring (NDM) must be configured on your devices.
- Install the custom Datadog Agent build provided by your Datadog representative.
Setup
In the Agent’s root configuration directory at
conf.d/network_config_management.d/, create theconf.yamlfile and configure it as follows:init_config: ## @param namespace - string - optional - default: default ## The namespace should match namespaces of devices being monitored namespace: default ## @param min_collection_interval - integer - optional - default: 900 (15 minutes) min_collection_interval: 900 ## @param ssh - object - optional ## Global SSH configuration that applies to all device instances unless ## overridden at the device level. ssh: ## @param timeout - duration - optional - default: 30 (seconds) ## Maximum time for the SSH client to establish a TCP connection. timeout: 30 ## @param known_hosts_path - string - required (unless insecure_skip_verify is true) ## Path to the known_hosts file containing public keys of servers to ## verify the identity of remote hosts. Required for secure connections. known_hosts_path: /path/to/known_hosts ## @param insecure_skip_verify - boolean - optional - default: false ## Skip host key verification. This is INSECURE and should only be used ## for development/testing purposes. insecure_skip_verify: false instances: ip_address - string - required ## The IP address of the network device to collect configurations from. ip_address: <IP_ADDRESS> ## @param auth - object - required ## Authentication credentials to connect to the network device. auth: ## @param username - string - required ## Username to authenticate to the network device. username: <USERNAME> ## @param password - string - required (if private_key_file is not provided) ## Password to authenticate to the network device. ## Used as a fallback after private key authentication if both are provided. password: <PASSWORD> ## @param private_key_file - string - optional ## Path to the SSH private key file for authentication. ## At least one of password or private_key_file must be provided. private_key_file: /path/to/private_keyOptionally, if your devices require specific SSH algorithms, use the following configuration:
init_config: ## @param ciphers - list of strings - optional ## List of SSH encryption ciphers to use for the connection. ## If not specified, the SSH library will use its default ciphers. ssh: ciphers: [aes128-gcm@openssh.com, aes128-ctr, aes192-ctr] key_exchanges: [diffie-hellman-group14-sha256, ecdh-sha2-nistp256] host_key_algorithms: [ssh-ed25519]Restart the Agent to apply the configuration changes.
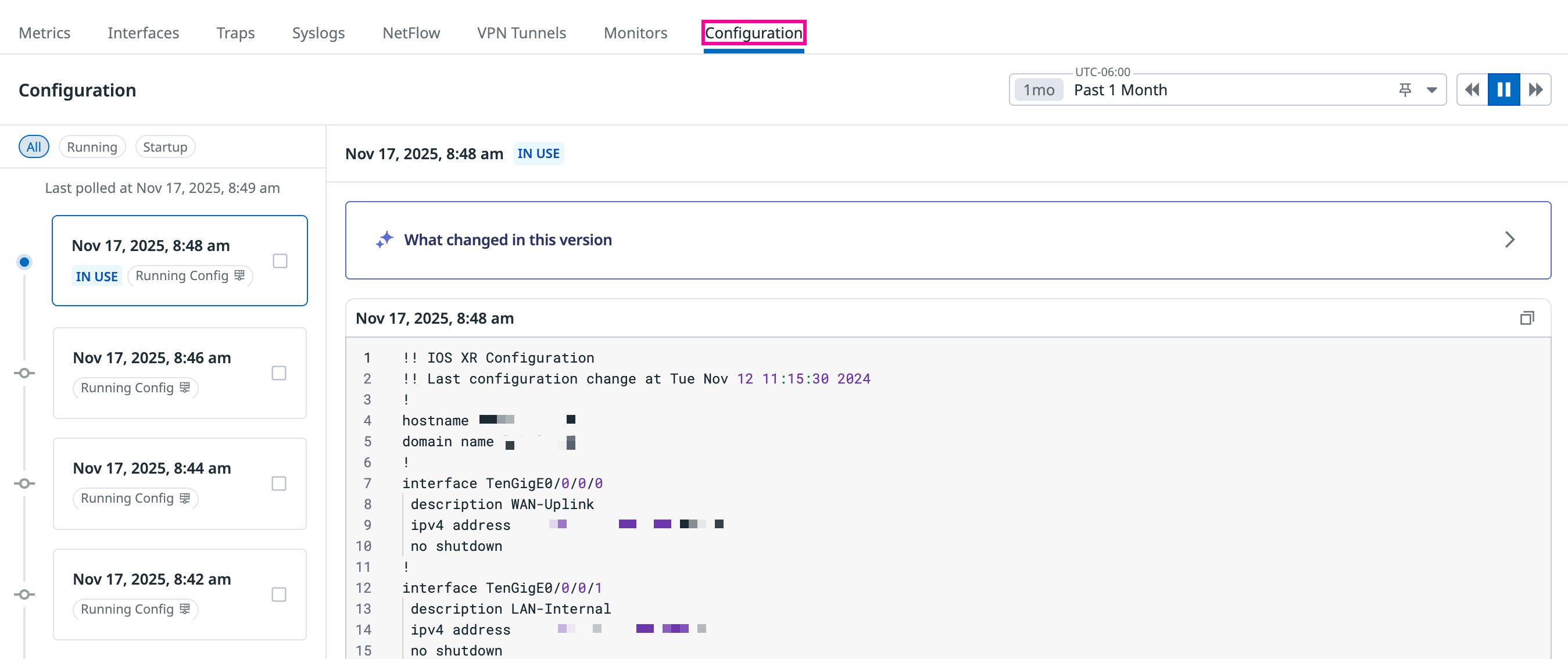
Viewing configurations
Network Configuration Management is accessible from the device side panel in Network Device Monitoring:
Navigate to Network Device Monitoring.
Select a device from the device list or from any NDM visualization such as Device Geomap or the Device Topology map.
Open the Configuration tab in the device side panel.
On the Configuration tab, you can filter what the configuration list displays:
- All: Shows both running and startup configurations
- Running: The active, live configuration running on the device
- Startup: The saved configuration that loads when the device boots
Time picker and retention
The time controls at the top of the page allow you to select which configuration history to view. You can extend this range to view older versions, up to the retention limit (1 year).
The timeline and configuration version list automatically update based on your selected time range.
Note: Configuration history begins when NCM is enabled for your account. Historical data prior to enablement is not available.
View a configuration at a point in time
Selecting a configuration event from the timeline or list opens a single configuration view showing the state of the device at that moment.
The single-configuration view displays:
- The complete configuration for the selected timestamp
- Device metadata including time and device identity
You can scroll through the configuration to investigate the device state during an incident, or adjust the time range to view configurations from different time periods.
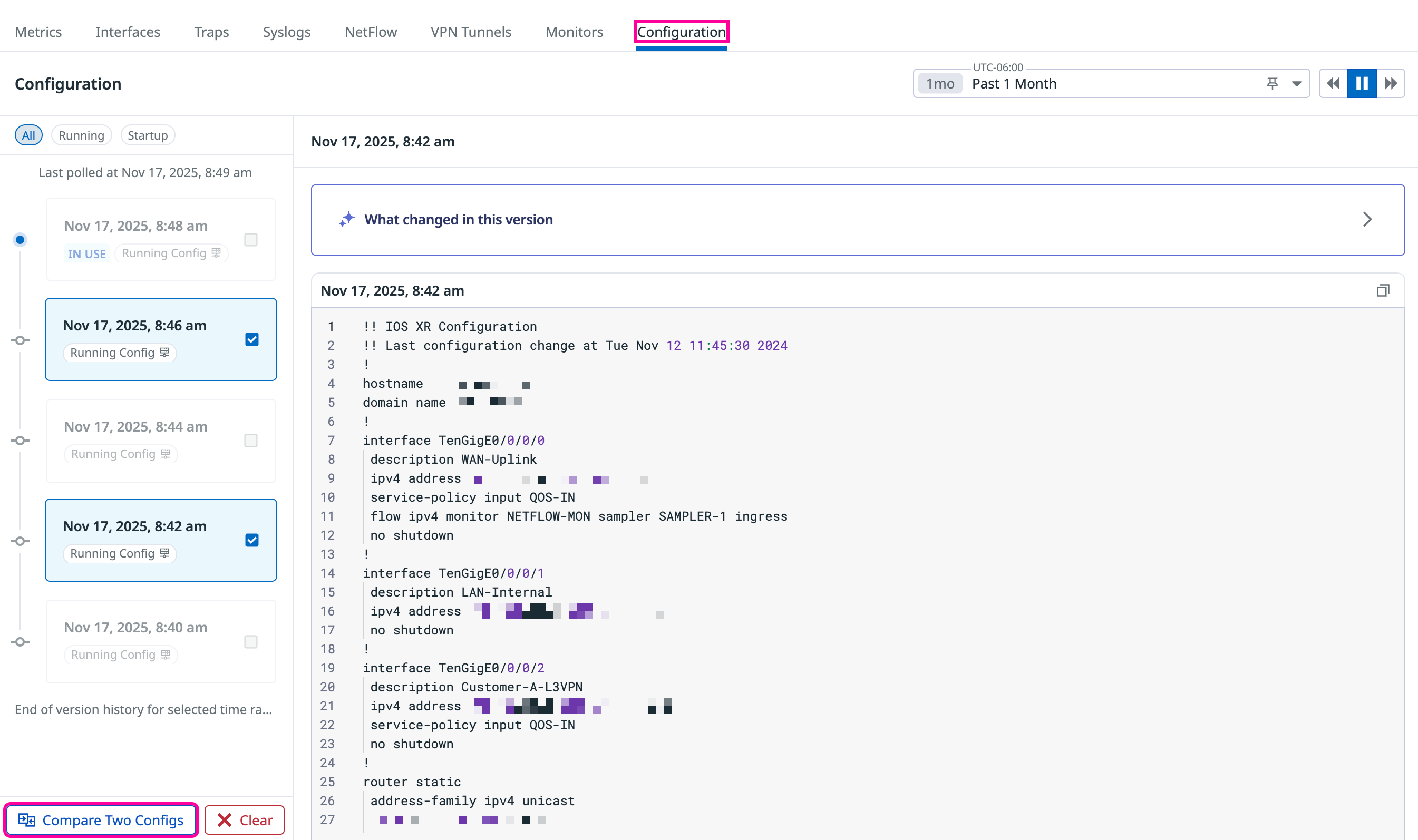
Compare configuration versions
To see what changed between configuration versions:
Select two configurations from the history list or timeline using the checkboxes.
Click Compare Two Configs to open the comparison view.
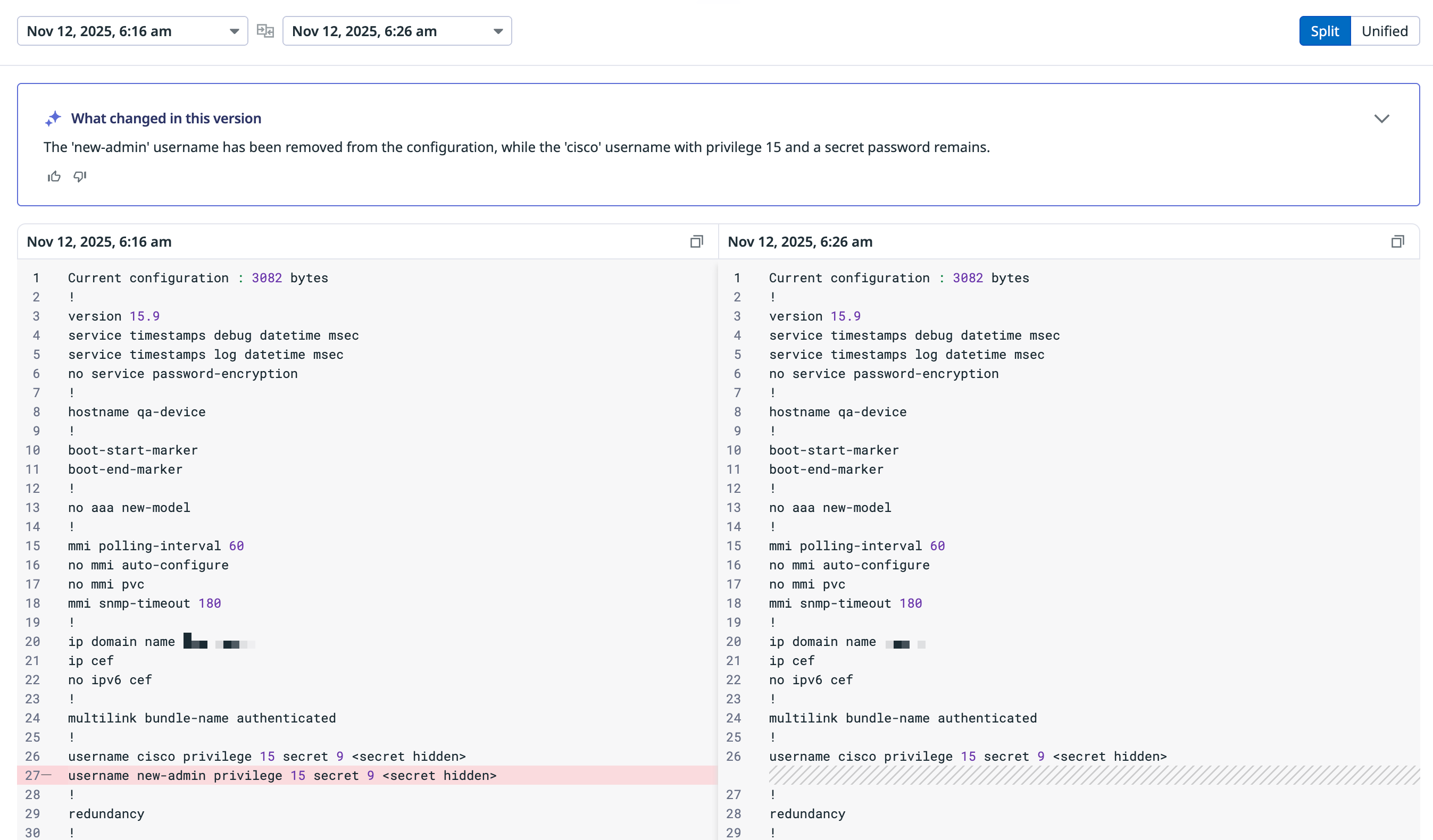
The comparison view shows both configurations side by side with inline diffs that highlight changed lines. You can switch between different configuration pairs without closing the comparison view.
AI summaries
Network Configuration Management includes an AI-powered summary panel that translates configuration changes into natural language explanations.
When you compare two configuration versions, the AI summary automatically:
- Describes changes in human-readable terms
- Highlights changes that may be relevant for incident investigation or risk analysis
Further Reading
お役に立つドキュメント、リンクや記事: