- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
Cloudcraft で使用するカスタム IAM ポリシーを作成する
Cloudcraft は、_読み取り専用_の IAM ロールを使用して AWS アカウントをスキャンし、コンポーネント間のサービス関係をリバースエンジニアリングして、アーキテクチャのダイアグラムを自動生成します。
すべてを設定する最も簡単な方法は、アプリケーション内の指示に従うことです。これにより、数回のクリックでロールが作成され、権限が設定されます。このロールにはデフォルトで AWS 管理の ReadOnlyAccess IAM ポリシーが割り当てられます。
もし、特定のサービスや API を除外するなど、より正確に権限を制御する必要がある場合、カスタム Cloudcraft IAM ポリシーを使用することでそれが可能になります。
カスタム IAM ポリシーを使用する場合、新しいサービスや機能が Cloudcraft に追加されるたびに手動で更新する必要があります。アプリ内で Limited AWS access という通知が表示された場合、以下から最新バージョンのカスタム IAM ポリシーに更新してみてください。
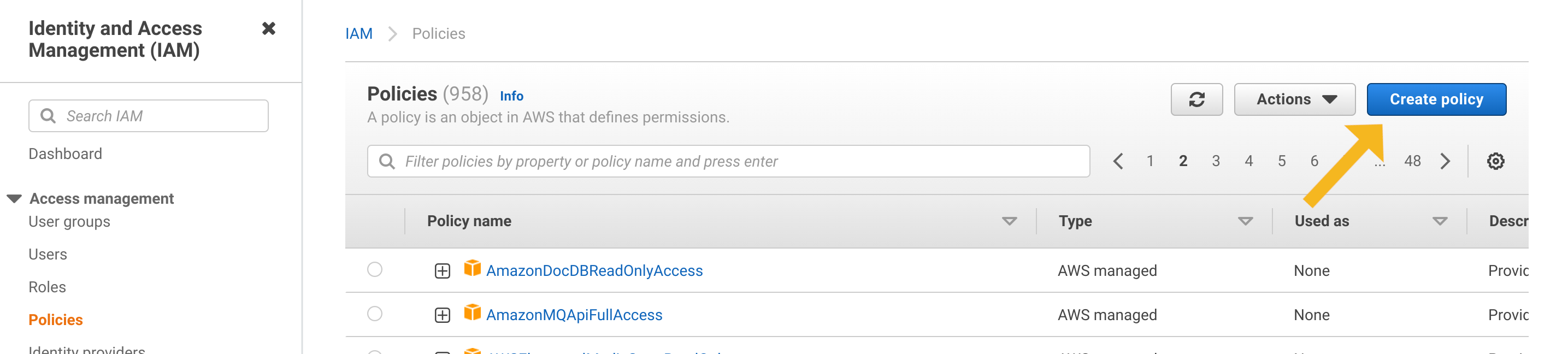
カスタム IAM ポリシーの作成
まず、IAM ポリシーコンソールを開き、Create Policy ボタンをクリックします。
JSON タブに切り替え、以下のリンクされたポリシーのいずれかの内容をコピーします。
また、独自の要件に合わせてポリシーをカスタマイズすることもできます。
- Cloudcraft custom IAM policy: このポリシーはデフォルトの
ReadOnlyAccessポリシーよりも厳格です。このポリシーには、Cloudcraft が使用する個々のサービスと読み取り専用の権限のみが含まれています。Cloudcraft が完全に新しいサービスのサポートを追加する際には、通常このポリシーを更新する必要があります。 - Cloudcraft minimal IAM policy: これは最も厳格な形式のポリシーです。このポリシーには、Cloudcraft の完全な機能のための個別の読み取り専用権限がそれぞれ列挙されています。このポリシーは、新しいサービスのサポートが追加されたときや既存のサービスが改善されたときなど、より頻繁に更新する必要があります。
- 上記のいずれかのポリシーをベースにして、独自のカスタマイズを行うことができます。たとえば、個々のサービスや権限を削除することが可能です。Cloudcraft がサービスにアクセスできない場合、そのサービスは結果として生成されるダイアグラムから除外されます。
画面の下部にある Review policy ボタンをクリックし、名前と説明を入力します。Cloudcraft は、整理と監査を容易にするために、以下の値を使用することを推奨しています。
- Policy Name: Cloudcraft
- Policy Description: Cloudcraft のカスタムポリシーです。
次に、Create policy をクリックしてポリシーを作成します。AWS コンソールはポリシーページにリダイレクトします。
最後に、新しく作成したポリシーを Cloudcraft IAM ロールに適用します。まだロールを作成していない場合は、アプリケーション内の指示に従ってください。