- Principales informations
- Getting Started
- Agent
- API
- Tracing
- Conteneurs
- Dashboards
- Database Monitoring
- Datadog
- Site Datadog
- DevSecOps
- Incident Management
- Intégrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profileur
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Surveillance Synthetic
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- Développeurs
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Application mobile
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Alertes
- Watchdog
- Métriques
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Conteneurs
- Processes
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Termes et concepts de l'APM
- Sending Traces to Datadog
- APM Metrics Collection
- Trace Pipeline Configuration
- Connect Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilité des services
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Suivi des erreurs
- Sécurité des données
- Guides
- Dépannage
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Exploring Database Schemas
- Exploring Recommendations
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM et Session Replay
- Surveillance Synthetic
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- Securité
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- CloudPrem
- Administration
Supply Chain Firewall
Supported OS
Intégration1.0.0
Supply Chain Firewall - Events
Supply Chain Firewall - Events
Cette page n'est pas encore disponible en français, sa traduction est en cours.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Overview
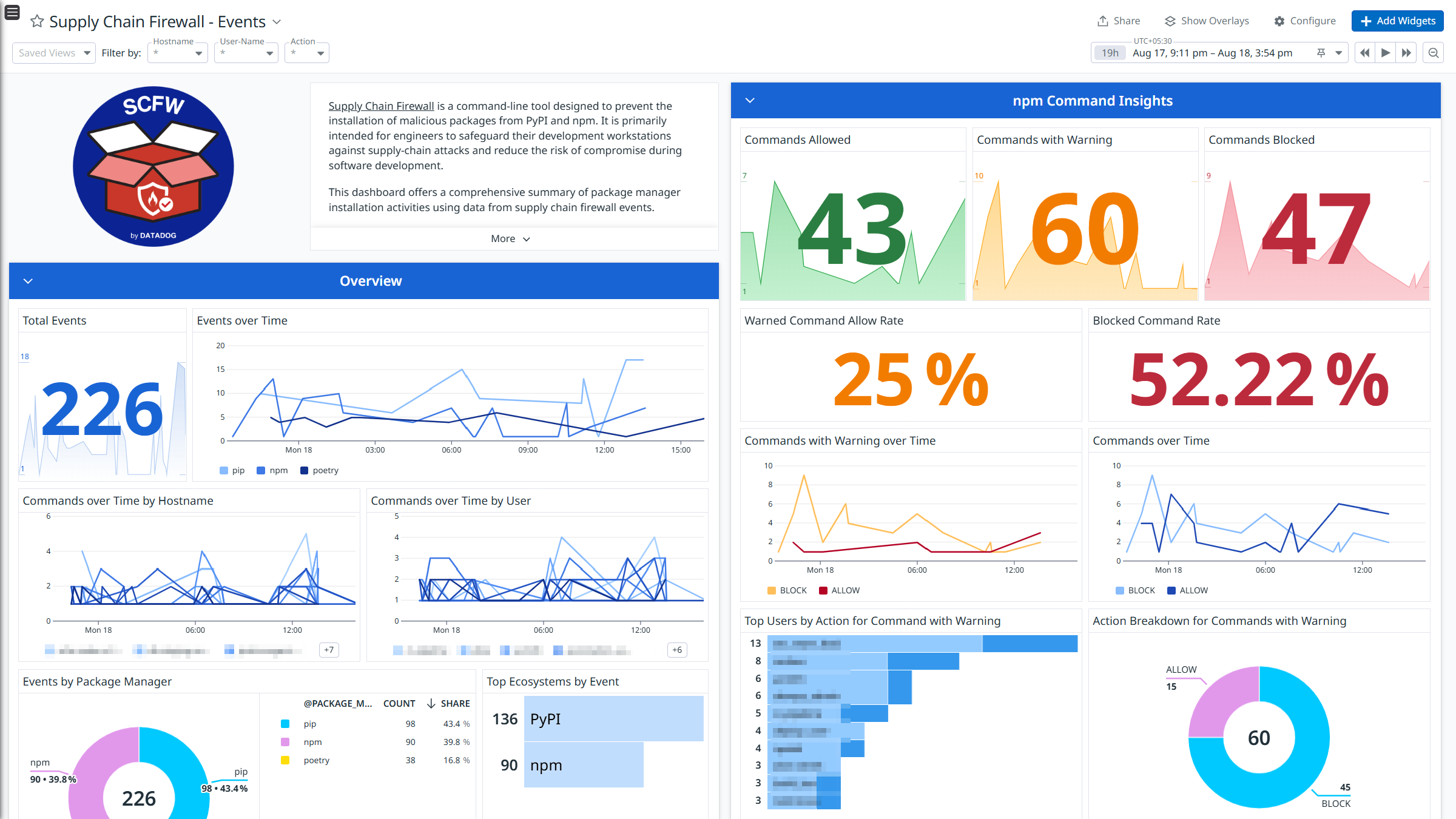
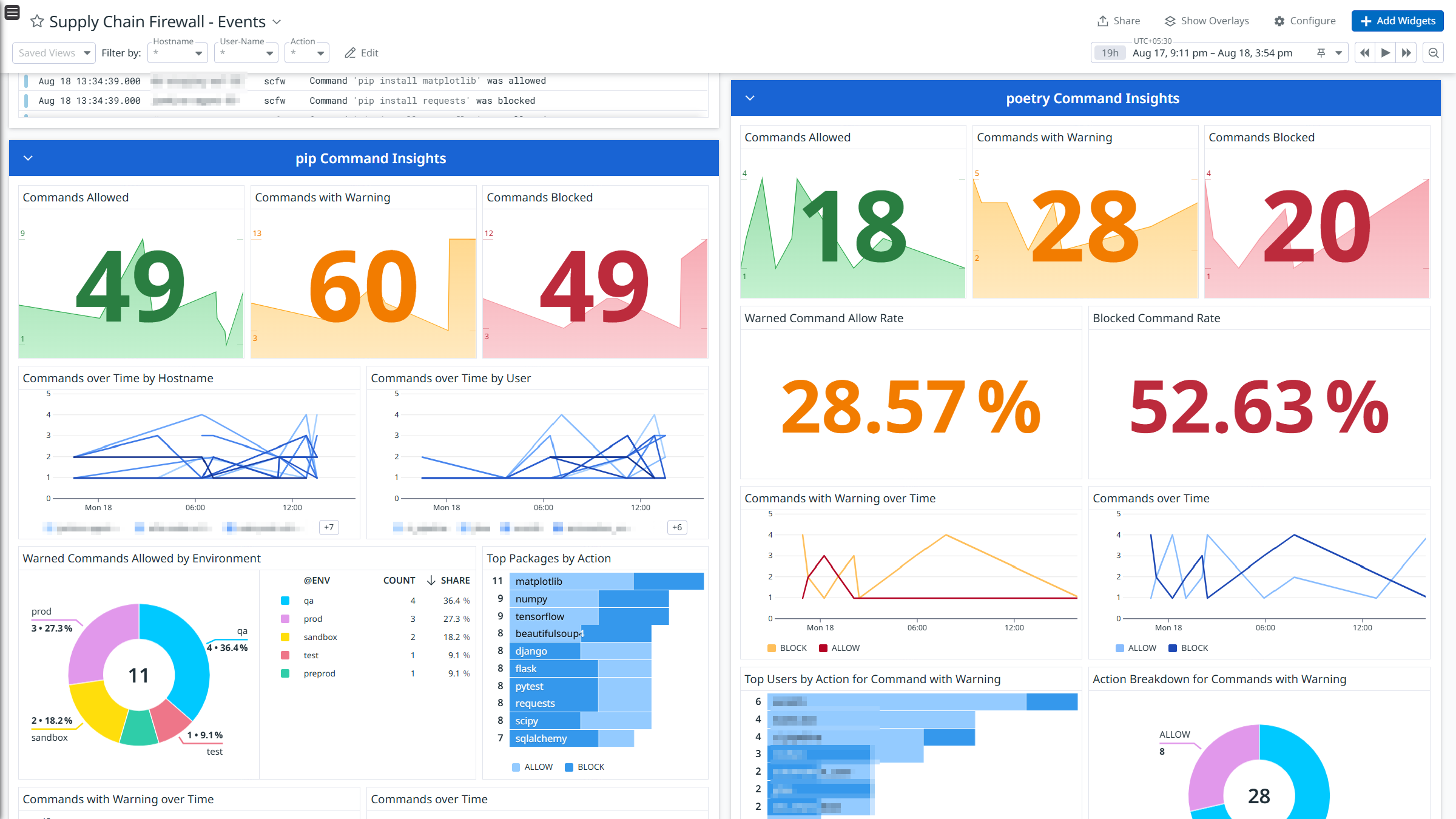
Supply Chain Firewall is a command-line tool designed to prevent the installation of malicious packages from PyPI and npm. It is primarily intended for engineers to safeguard their development workstations against supply-chain attacks and reduce the risk of compromise during software development.
Integrate Supply Chain Firewall with Datadog’s pre-built dashboard visualizations to gain insights into Package Manager logs. With Datadog’s built-in log pipelines, you can parse and enrich these logs to facilitate easy search and detailed insights. Additionally, the integration includes ready-to-use Cloud SIEM detection rules for enhanced monitoring and security.
Setup
Configuration
Execute the following command to start configuration for Supply Chain Firewall:
scfw configureFollow the setup prompts and configure the options as needed. During the log forwarding configuration, choose one of the options below to send logs to Datadog, based on your preferences:
Option 1: Sending Logs through the Datadog Agent
Configure log forwarding through the Datadog Agent:
[?] If you have the Datadog Agent installed locally, would you like to forward firewall logs to it? (y/N): y [?] Enter the local port where the Agent will receive logs (default: 10365): <PORT> [?] Select the desired log level for Datadog logging: > Log allowed and blocked commandsThis will automatically create the
scfw.d/conf.yamlfile in theconf.d/folder at the root of your Agent’s configuration directory, using the provided port for TCP log forwarding.Log collection is disabled by default in the Datadog Agent. Enable it by editing the
datadog.yamlfile:logs_enabled: trueRestart the agent to begin accepting firewall logs:
sudo systemctl restart datadog-agent
Option 2: Sending Logs through an API Key
- Configure log forwarding using the Datadog API key:
[?] If you have the Datadog Agent installed locally, would you like to forward firewall logs to it? (y/N): N [?] Would you like to enable sending firewall logs to Datadog using an API key? (y/N): y [?] Enter a Datadog API key: <DATADOG_API_KEY> [?] Select the desired log level for Datadog logging: > Log allowed and blocked commands - By default, the Datadog instance site is set to
us1. If your instance uses a different site, set theDD_SITEenvironment variable accordingly using the appropriateSite Parameterfrom the Datadog site documentation.
- Configure log forwarding using the Datadog API key:
After setup, update your current shell environment:
For Bash:
source ~/.bashrcFor Zsh:
source ~/.zshrc
Validation
If you selected Option 1 to forward logs through the Datadog Agent, run the Agent’s status subcommand and look for scfw under the Logs Agent section.
Data Collected
Logs
The Supply Chain Firewall integration collects and forwards Package Manager logs to Datadog.
Metrics
The Supply Chain Firewall integration does not include any metrics.
Events
The Supply Chain Firewall integration does not include any events.
Troubleshooting
Need help? Contact Datadog support.
