- Principales informations
- Getting Started
- Agent
- API
- Tracing
- Conteneurs
- Dashboards
- Database Monitoring
- Datadog
- Site Datadog
- DevSecOps
- Incident Management
- Intégrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profileur
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Surveillance Synthetic
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- Développeurs
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Application mobile
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Alertes
- Watchdog
- Métriques
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Conteneurs
- Processes
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Termes et concepts de l'APM
- Sending Traces to Datadog
- APM Metrics Collection
- Trace Pipeline Configuration
- Connect Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilité des services
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Suivi des erreurs
- Sécurité des données
- Guides
- Dépannage
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Exploring Database Schemas
- Exploring Recommendations
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM et Session Replay
- Surveillance Synthetic
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- Securité
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- CloudPrem
- Administration
Connecter votre compte AWS à Cloudcraft
La connexion de vos comptes AWS à Cloudcraft vous permet de visualiser votre infrastructure, en représentant au sein d’un diagramme d’architecture système, par rétro-ingénierie, les relations entre les services de votre environnement en direct. En plus de générer automatiquement des diagrammes, Cloudcraft crée aussi un modèle de budget et affiche pour vos composants importés des données de statut en direct au sein de vos diagrammes. Vous pouvez connecter autant de comptes AWS que vous le souhaitez à Cloudcraft.
Remarque : pour les organisations AWS, vous devez ajouter manuellement le rôle Cloudcraft à chaque compte individuel de l’organisation.
Cet article décrit la marche à suivre pour connecter votre compte AWS à Cloudcraft.
Les utilisateurs Datadog peuvent contourner ce processus en connectant leur compte Datadog à Cloudcraft. Pour en savoir plus, consultez l'intégration Datadog.
Prérequis
- Un utilisateur Cloudcraft avec le rôle Propriétaire ou Administrateur.
- Un abonnement actif à Cloudcraft Pro.
- Un compte AWS disposant de l’autorisation nécessaire pour créer des rôles IAM.
Fonctionnement de la synchronisation d’AWS en direct
Cloudcraft utilise un rôle intercompte pour accéder en toute sécurité à votre environnement AWS. Par conséquent, vous devez créer un rôle en lecture seule spécifique à Cloudcraft dans votre compte AWS. Ce rôle peut être révoqué à tout moment.
Si vous ne pouvez pas créer de rôle en lecture seule avec un accès à l’ensemble des composants, ou si cela enfreint la politique de votre entreprise, vous pouvez également mettre en place une politique d’accès minimal plus stricte, en n’accordant un accès en lecture seule qu’aux ressources que vous souhaitez utiliser avec Cloudcraft. Cela restreint encore plus le volume de données auxquelles le rôle a accès.
Cloudcraft ne conserve aucune des données en direct de votre environnement AWS. En revanche, Cloudcraft stocke les ARN, qui sont des identifiants uniques pour les ressources AWS. Cela permet à l’application d’associer les données en direct aux composants au moment de l’exécution.
Les données de votre environnement AWS sont transmises en temps réel à votre navigateur par l’intermédiaire de l’environnement AWS de Cloudcraft, à l’aide d’un accès basé sur les rôles, et sont stockées côté client uniquement lors de l’utilisation de l’application. Lorsque vous fermez l’application, les données en temps réel sont supprimées.
Sans accès en lecture à votre compte, certaines fonctionnalités Cloudcraft ne sont pas disponibles, comme la suppression d’une instance EC2 à la fois dans le diagramme et dans votre compte. Cette approche est néanmoins moins risquée.
Cloudcraft met en œuvre des processus et des contrôles de sécurité rigoureux dans le cadre du programme de conformité SOC2. Pour en savoir plus sur le programme et les contrôles de sécurité de Cloudcraft, consultez la page relative à la sécurité de Cloudcraft (en anglais).
Gérer des comptes AWS
Ajouter un compte
- Dans Cloudcraft, accédez à User > AWS accounts.
- En bas de la fenêtre modale, cliquez sur Add AWS Account.
- La page suivante fournit des instructions détaillées. Cliquez sur Open the AWS IAM Console to the Create Role Page pour configurer le rôle IAM en lecture seule dans AWS.
Si vous ne parvenez pas à accéder à la page Create Role, il se peut que vous ne disposiez pas de l'autorisation AdministrativeAccess ou des autorisations IAM requises pour créer un rôle IAM. Dans ce cas, contactez l'administrateur de votre compte AWS et demandez-lui d'effectuer les étapes suivantes.
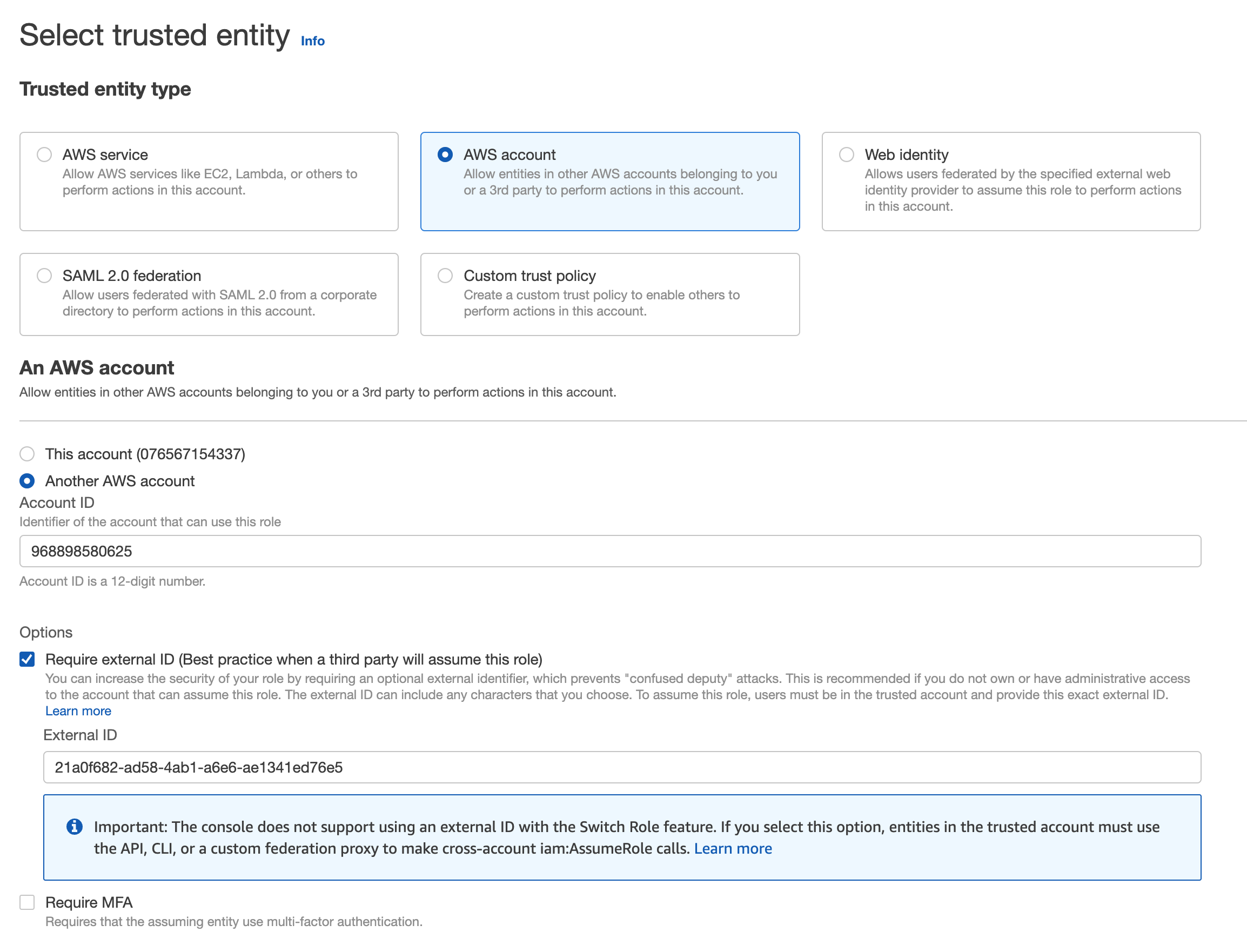
- Sur la page Create role d’AWS, vérifiez que l’option Require MFA est décochée, puis cliquez sur Next.
L'option Require MFA doit être désactivée, car elle n'est pas applicable à un accès d'un système à un autre sans intervention humaine. L’accès est sécurisé en étant restreint au compte AWS Cloudcraft.
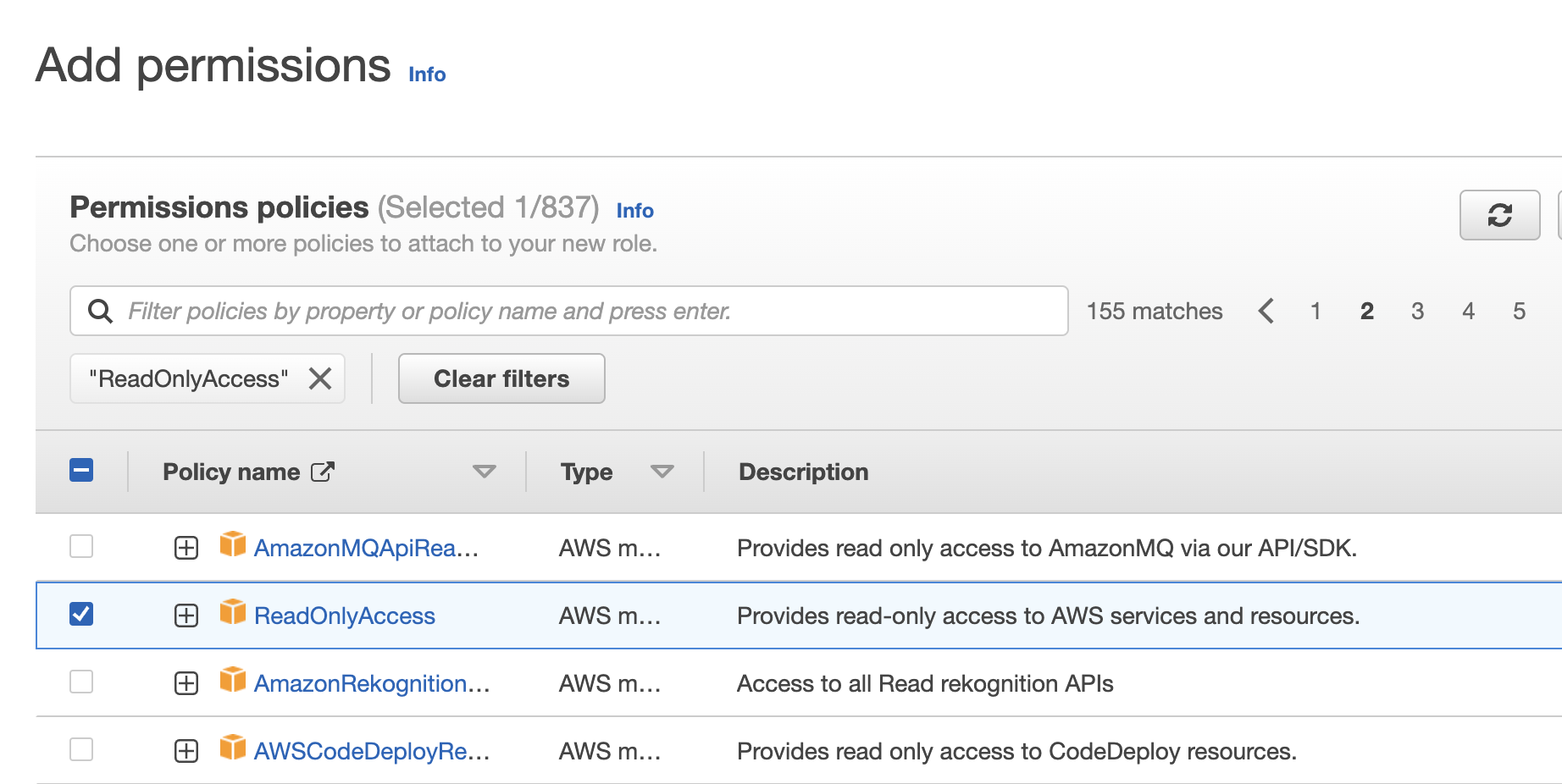
- Ajoutez ensuite des stratégies d’autorisation à votre rôle. Saisissez ReadOnlyAccess dans le champ de recherche et appuyez sur Entrée pour filtrer les politiques par nom.
- Sélectionnez la stratégie ReadOnlyAccess afin de fournir un accès en lecture seule aux services et ressources AWS, puis cliquez sur Next.
- Saisissez un nom et une description pour le rôle IAM. Vous pouvez également ajouter des tags pour organiser, suivre ou contrôler l’accès pour le rôle. L’ajout de tags au rôle n’est pas requis. Pour en savoir plus sur les meilleures pratiques de tagging des ressources AWS, consultez le livre blanc dédié (en anglais).
- Cliquez sur Create role.
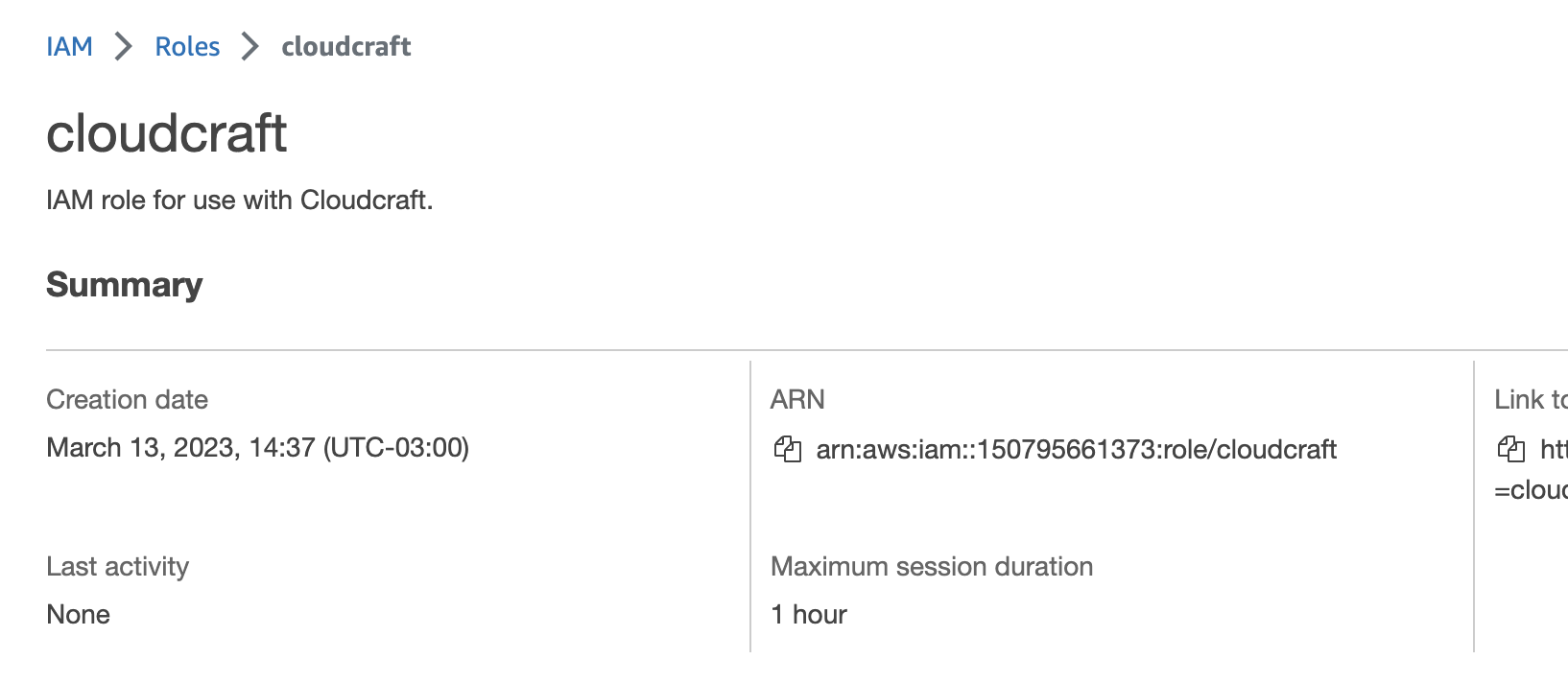
- Sélectionnez le rôle
cloudcraftdepuis la liste des rôles. Sur la page Summary, copiez l’ARN du rôle.
- Accédez à Cloudcraft, collez l’ARN dans le champ Role ARN, puis saisissez un nom pour votre compte.
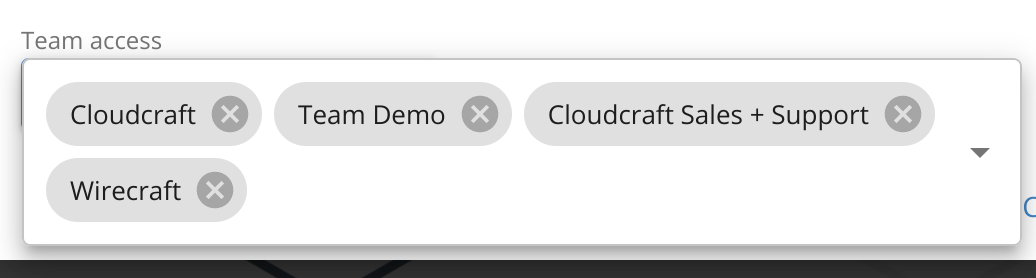
- Pour configurer l’accès des équipes, cliquez sur le bouton bleu sous Team access, puis sélectionnez les équipes auxquelles vous souhaitez accorder un accès au compte AWS. Cette étape est facultative.
- Cliquez sur Save Account.
Modifier un compte
Pour modifier un compte, cliquez sur l’icône grise en forme de crayon à gauche du compte pertinent. Vous pouvez modifier les détails du compte, comme le nom, l’ARN et l’accès des équipes.
Une fois vos modifications terminées, cliquez sur Save Account.
Supprimer un compte
Pour supprimer un compte, cliquez sur l’icône en forme de corbeille à droite du compte pertinent, puis cliquez sur Remove.