- Esenciales
- Empezando
- Agent
- API
- Rastreo de APM
- Contenedores
- Dashboards
- Monitorización de bases de datos
- Datadog
- Sitio web de Datadog
- DevSecOps
- Gestión de incidencias
- Integraciones
- Internal Developer Portal
- Logs
- Monitores
- OpenTelemetry
- Generador de perfiles
- Session Replay
- Security
- Serverless para Lambda AWS
- Software Delivery
- Monitorización Synthetic
- Etiquetas (tags)
- Workflow Automation
- Centro de aprendizaje
- Compatibilidad
- Glosario
- Atributos estándar
- Guías
- Agent
- Arquitectura
- IoT
- Plataformas compatibles
- Recopilación de logs
- Configuración
- Automatización de flotas
- Solucionar problemas
- Detección de nombres de host en contenedores
- Modo de depuración
- Flare del Agent
- Estado del check del Agent
- Problemas de NTP
- Problemas de permisos
- Problemas de integraciones
- Problemas del sitio
- Problemas de Autodiscovery
- Problemas de contenedores de Windows
- Configuración del tiempo de ejecución del Agent
- Consumo elevado de memoria o CPU
- Guías
- Seguridad de datos
- Integraciones
- Desarrolladores
- Autorización
- DogStatsD
- Checks personalizados
- Integraciones
- Build an Integration with Datadog
- Crear una integración basada en el Agent
- Crear una integración API
- Crear un pipeline de logs
- Referencia de activos de integración
- Crear una oferta de mercado
- Crear un dashboard de integración
- Create a Monitor Template
- Crear una regla de detección Cloud SIEM
- Instalar la herramienta de desarrollo de integraciones del Agente
- Checks de servicio
- Complementos de IDE
- Comunidad
- Guías
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Aplicación móvil de Datadog
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- En la aplicación
- Dashboards
- Notebooks
- Editor DDSQL
- Reference Tables
- Hojas
- Monitores y alertas
- Watchdog
- Métricas
- Bits AI
- Internal Developer Portal
- Error Tracking
- Explorador
- Estados de problemas
- Detección de regresión
- Suspected Causes
- Error Grouping
- Bits AI Dev Agent
- Monitores
- Issue Correlation
- Identificar confirmaciones sospechosas
- Auto Assign
- Issue Team Ownership
- Rastrear errores del navegador y móviles
- Rastrear errores de backend
- Manage Data Collection
- Solucionar problemas
- Guides
- Change Tracking
- Gestión de servicios
- Objetivos de nivel de servicio (SLOs)
- Gestión de incidentes
- De guardia
- Status Pages
- Gestión de eventos
- Gestión de casos
- Actions & Remediations
- Infraestructura
- Cloudcraft
- Catálogo de recursos
- Universal Service Monitoring
- Hosts
- Contenedores
- Processes
- Serverless
- Monitorización de red
- Cloud Cost
- Rendimiento de las aplicaciones
- APM
- Términos y conceptos de APM
- Instrumentación de aplicación
- Recopilación de métricas de APM
- Configuración de pipelines de trazas
- Correlacionar trazas (traces) y otros datos de telemetría
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilidad del servicio
- Endpoint Observability
- Instrumentación dinámica
- Live Debugger
- Error Tracking
- Seguridad de los datos
- Guías
- Solucionar problemas
- Límites de tasa del Agent
- Métricas de APM del Agent
- Uso de recursos del Agent
- Logs correlacionados
- Stacks tecnológicos de llamada en profundidad PHP 5
- Herramienta de diagnóstico de .NET
- Cuantificación de APM
- Go Compile-Time Instrumentation
- Logs de inicio del rastreador
- Logs de depuración del rastreador
- Errores de conexión
- Continuous Profiler
- Database Monitoring
- Gastos generales de integración del Agent
- Arquitecturas de configuración
- Configuración de Postgres
- Configuración de MySQL
- Configuración de SQL Server
- Configuración de Oracle
- Configuración de MongoDB
- Setting Up Amazon DocumentDB
- Conexión de DBM y trazas
- Datos recopilados
- Explorar hosts de bases de datos
- Explorar métricas de consultas
- Explorar ejemplos de consulta
- Exploring Database Schemas
- Exploring Recommendations
- Solucionar problemas
- Guías
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Experiencia digital
- Real User Monitoring
- Pruebas y monitorización de Synthetics
- Continuous Testing
- Análisis de productos
- Entrega de software
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Configuración
- Network Settings
- Tests en contenedores
- Repositories
- Explorador
- Monitores
- Test Health
- Flaky Test Management
- Working with Flaky Tests
- Test Impact Analysis
- Flujos de trabajo de desarrolladores
- Cobertura de código
- Instrumentar tests de navegador con RUM
- Instrumentar tests de Swift con RUM
- Correlacionar logs y tests
- Guías
- Solucionar problemas
- Code Coverage
- Quality Gates
- Métricas de DORA
- Feature Flags
- Seguridad
- Información general de seguridad
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- Observabilidad de la IA
- Log Management
- Observability Pipelines
- Gestión de logs
- CloudPrem
- Administración
- Gestión de cuentas
- Seguridad de los datos
- Ayuda
Symantec Endpoint Protection
Supported OS
Versión de la integración1.0.0






Symantec Endpoint Protection: información general
Symantec Endpoint Protection: análisis
Symantec Endpoint Protection: riesgos
Symantec Endpoint Protection: control de aplicaciones
Symantec Endpoint Protection: seguridad
Symantec Endpoint Protection: sistema
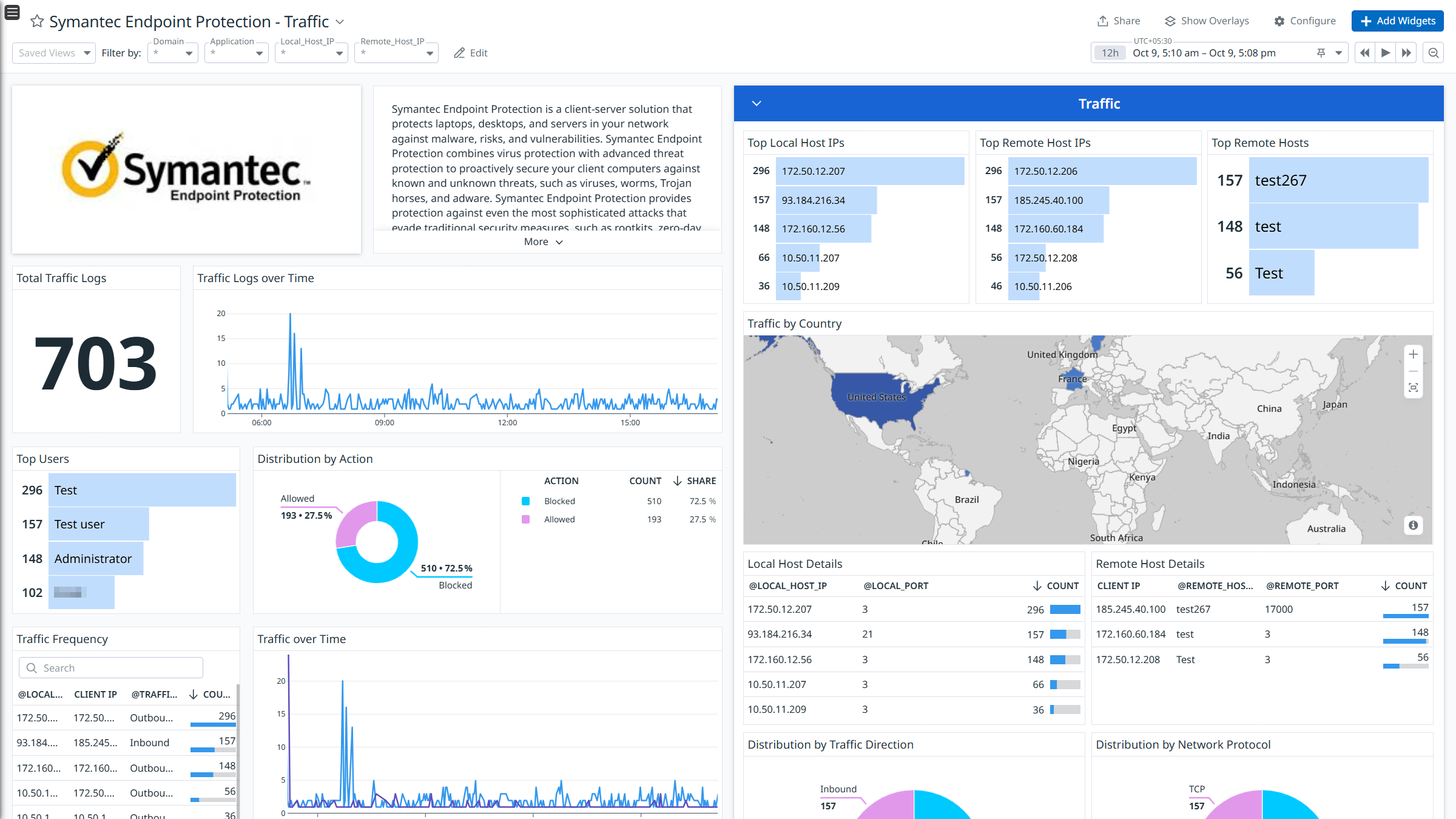
Symantec Endpoint Protection: tráfico
Información general
Symantec Endpoint Protection es una solución cliente-servidor que protege los equipos portátiles, los equipos de escritorio y los servidores de tu red contra malware, riesgos y vulnerabilidades. Symantec Endpoint Protection combina la protección antivirus con la protección avanzada frente a amenazas para proteger de forma proactiva los equipos cliente frente a amenazas conocidas y desconocidas, como virus, gusanos, troyanos y adware. Symantec Endpoint Protection ofrece protección incluso contra los ataques más sofisticados que evaden las medidas de seguridad tradicionales, como rootkits, ataques de día cero y spyware que muta.
Esta integración enriquece e ingiere los siguientes logs de Symantec Endpoint Protection:
- Logs de auditoría: registra los cambios en las políticas, tales como actualizaciones de políticas, asignaciones de políticas y más.
- Logs de riesgos: rastrea y registra los posibles riesgos de seguridad detectados en los endpoints, incluido el malware, las vulnerabilidades y las actividades sospechosas.
- Logs de análisis: registra los resultados de los análisis antivirus, incluido el malware detectado, la configuración del análisis y la información del usuario.
- Logs del sistema: registra todas las actividades administrativas, actividades de clientes, actividades de servidores y actividades de
client_server. - Logs de seguridad: registra los eventos relacionados con la seguridad, incluidos los ataques, el cumplimiento y el control de dispositivos.
- Logs de control de aplicaciones: registra eventos relacionados con el control de aplicaciones, como aplicaciones bloqueadas o permitidas.
- Logs de tráfico: registra el tráfico de red eventos, incluidas las conexiones entrantes y salientes, los protocolos y los puertos.
También puedes visualizar información detallada en los logs mencionados con los dashboards predefinidos. Una vez instalada la integración, puedes buscar dashboards escribiendo “symantec-endpoint-protection” en la lista de dashboards.
Configuración
Instalación
Para instalar la integración de Symantec Endpoint Protection, ejecuta el siguiente comando de instalación del Agent y los pasos que se indican a continuación. Para obtener más información, consulta la Documentación de gestión de la integración.
Nota: Este paso no es necesario para el Agent versión >= 7.52.0.
Comando de Linux:
sudo -u dd-agent -- datadog-agent integration install datadog-symantec_endpoint_protection==1.0.0
Configuración
Recopilación de logs
La recopilación de logs está desactivada por defecto en el Datadog Agent. Actívala en
datadog.yaml:logs_enabled: trueAñade este bloque de configuración a tu archivo
symantec_endpoint_protection.d/conf.yamlpara comenzar a recopilar tus logs de Symantec Endpoint Protection.Consulta el archivo de ejemplo symantec_endpoint_protection.d/conf.yaml para ver las opciones de configuración disponibles.
logs: - type: udp port: <PORT> service: symantec-endpoint-protection source: symantec-endpoint-protectionConfigura el reenvío de mensajes de Syslog desde Symantec Endpoint Protection Server:
- Inicia sesión en Symantec Endpoint Protection Server.
- Haz clic en Admin (Administrar).
- Haz clic en servers (servidores) en el panel administrative (administrativo).
- Selecciona los sites (sitios) para los que deseas reenviar logs.
- Haz clic en Configure external logging (Configurar logging externo).
- Activa la transmisión de logs a un servidor Syslog.
- Indica la syslog server IP (IP del servidor syslog).
- Selecciona el protocolo red como UDP.
- Indica el PORT (Puerto) al que deseas reenviar los logs.
Validación
Ejecuta el subcomando de estado del Agent y busca symantec_endpoint_protection en la sección Checks.
Datos recopilados
Logs
La integración de Symantec Endpoint Protection recopila datos de auditoría, riesgos, análisis, seguridad, tráfico, control de aplicaciones y logs del sistema.
Métricas
La integración de Symantec Endpoint Protection no incluye métricas.
Eventos
La integración de Symantec Endpoint Protection no incluye ningún evento.
Checks de servicio
La integración de Symantec Endpoint Protection no incluye ningún check de servicio.
Solucionar problemas
Permiso denegado durante la vinculación de puertos
Si ves un error de Permission denied (Permiso denegado) mientras vinculas puertos en logs del Agent, consulta las siguientes instrucciones:
La vinculación a un número de puerto inferior a 1024 requiere permisos elevados. Concede acceso al puerto mediante el comando
setcap:Concede acceso al puerto mediante el comando
setcap:sudo setcap CAP_NET_BIND_SERVICE=+ep /opt/datadog-agent/bin/agent/agentComprueba que la configuración es correcta mediante la ejecución del comando
getcap:sudo getcap /opt/datadog-agent/bin/agent/agentCon el resultado esperado:
/opt/datadog-agent/bin/agent/agent = cap_net_bind_service+epNota: Vuelve a ejecutar este comando
setcapcada vez que actualices el Agent.
No se recopilan datos
Asegúrate de que se evita el tráfico del puerto configurado si el firewall está activado.
Puerto ya utilizado
Si aparece el error Port <PORT-NO> Already in Use, consulta las siguientes instrucciones. El ejemplo siguiente es para PORT-NO = 514:
En los sistemas que utilizan Syslog, si el Agent escucha logs de Cisco Secure Firewall en el puerto 514, puede aparecer el siguiente error en los logs del Agent: Can't start UDP forwarder on port 514: listen udp :514: bind: address already in use.
Este error se produce porque, por defecto, Syslog escucha en el puerto 514. Para resolver este error, sigue uno de los pasos siguientes:
- Desactiva Syslog.
- Configura el Agent para escuchar en un puerto diferente disponible.
¿Necesitas ayuda? Ponte en contacto con el servicio de asistencia de Datadog.
