- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Okta SAML Identity Provider Configuration
In the site, you must manually configure the Datadog application in Okta using the legacy instructions. Ignore the instructions on this page about the preconfigured Datadog application in the Okta application catalog.
Overview
This page tells you how to set up the Datadog application in Okta.
Before proceeding, make sure that you are using the latest version of the Datadog application:
- In Okta, click Applications.
- Open the Datadog application.
- Select the General tab.
- Look for a field labeled SSO Base URL.
If you don’t see the SSO Base URL field, configure Okta using the legacy instructions.
Supported features
The Datadog Okta SAML integration supports the following:
- IdP-initiated SSO
- SP-initiated SSO
- JIT provisioning
For definitions of the terms above, see the Okta glossary.
Setup
Set up Okta as the SAML identity provider (IdP) for Datadog with the following instructions. The setup process requires you to alternate between your Okta and Datadog accounts.
Add the Datadog integration in Okta
- Log in to your Okta admin dashboard.
- In the left navigation, click Applications.
- Click Browse App Catalog.
- Use the search bar to search for “Datadog”.
- Select the Datadog app for SAML and SCIM.
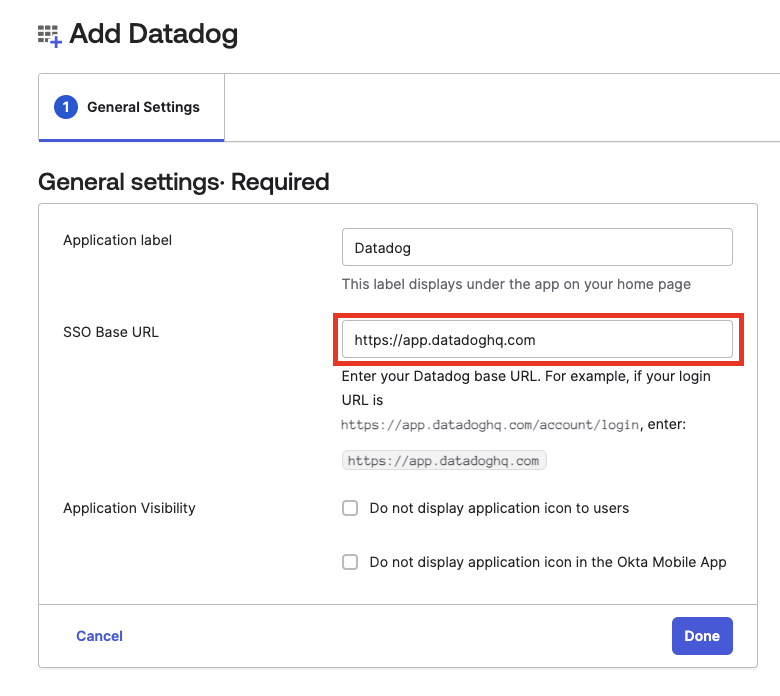
- Click Add Integration. The General Settings dialog appears.
- Populate the SSO Base URL field with your Datadog website URL.
- Click Done.
Note: The SSO Base URL field accepts custom subdomains if you are not using a standard Datadog website URL.
Next, download the metadata details to upload to Datadog:
- While in the settings dialog for the Datadog application in Okta, click the Sign on tab.
- Scroll down until you see the Metadata URL.
- Click Copy.
- Open a new browser tab and paste the metadata URL into the address bar.
- Use your browser to save the content of the metadata URL as an XML file.
Configure Datadog
Upload metadata details
- Navigate to Login Methods under Organization Settings.
- In the SAML component, click Configure or Update, depending on whether you have previously configured SAML. The SAML configuration page appears.
- Click Choose File, and select the metadata file you previously downloaded from Okta.
Activate IdP initiated login
For the Datadog application to function correctly, you must activate IdP initiated login.
After you activate IdP initiated login, users can log in to Datadog from Okta
To activate IdP initiated login, execute the following steps:
- Navigate to the SAML configuration page.
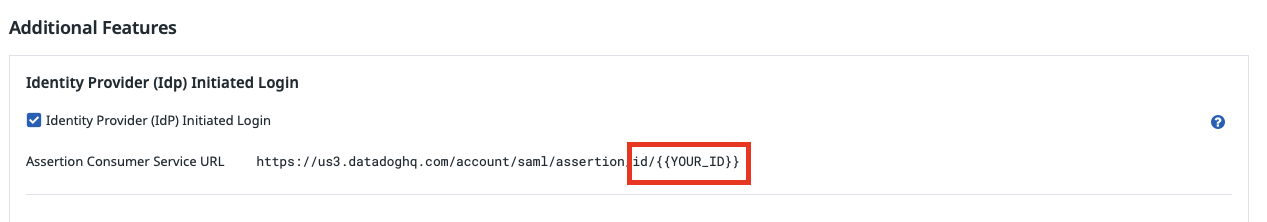
- Under Additional Features, click the checkbox for Identity Provider (IdP) Initiated Login. The component displays the Assertion Consumer Service URL.
- The content in the Assertion Consumer Service URL after
/saml/assertionis your company ID. Enter this value with the/id/prefix in Okta to finalize your configuration. - Click Save Changes.
Return to Okta for the next set of configuration steps.
Add the company ID in Okta
- Return to the Okta admin dashboard.
- Select the Sign on tab.
- Click Edit.
- Scroll down to the Advanced Sign-on Settings section.
- Paste your full company ID including the
/id/prefix into the Company ID field (/id/XXXXXX-XXXX-XXX-XXXX-XXXXXXX). - Click Save.
Service Provider (SP) initiated login
To log in to Datadog using service provider-initiated login (SP-initiated SSO), you need the single sign-on (SSO) URL. You can find your SSO URL in two ways: on the SAML configuration page, or through email.
SAML configuration page
The Datadog SAML configuration page displays the SSO URL next to the Single Sign-on URL heading.
- Navigate to the Datadog website URL for your organization.
- Select Using Single Sign-On?.
- Enter your email address, and click Next.
- Check your email for a message containing the SSO URL, listed as Login URL.
After you find your SSO URL from either method, bookmark it for future reference.
SAML role mapping
Follow the steps below to map Okta attributes to Datadog entities. This step is optional.
- Navigate to the Okta admin dashboard.
- Select the Sign on tab.
- Click Edit.
- Populate the Attributes with your group attribute statements.
- Set up your desired mappings in Datadog.
Further Reading
Additional helpful documentation, links, and articles: