- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- AI Guard
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Single Sign On With SAML
The Datadog for Government site only supports SAML login.
Overview
Configuring SAML (Security Assertion Markup Language) for your Datadog account lets you and all your teammates log in to Datadog using the credentials stored in your organization’s Active Directory, LDAP, or other identity store that has been configured with a SAML Identity Provider.
Notes:
- If you don’t have SAML enabled on your Datadog account, reach out to support to enable it.
- This documentation assumes that you already have a SAML Identity Provider (IdP). If you do not have a SAML IdP, there are several IdPs that have integrations with Datadog such as Active Directory, Auth0, Google, LastPass, Microsoft Entra ID, Okta, and SafeNet.
- SAML configuration requires Datadog Administrator access.
Configuring SAML
See Configuring Single Sign-On With SAML for instructions.
Using SAML
After SAML is configured in Datadog and your IdP is set up to accept requests from Datadog, users can log in.
SP-initiated login
SP-initiated, or Service Provider-initiated, means login initiated from Datadog. Users log in through the Single Sign-on URL shown in the status box at the top of the SAML Configuration page. Loading this URL initiates a SAML authentication against your IdP. Note: This URL only displays if SAML is enabled for your account and you are using SP-initiated login.
When a user logs in through SP-initiated SAML and the organization does not have a custom subdomain, Datadog requires additional security. Users receive a one-time email verification code that is required to log in.
IdP-initiated login
IdP-initiated, or Identity Provider-initiated, means login initiated from your app portal. Users log in by clicking on the app icon in your app portal, for example, in the Google App drawer or the Okta App Portal. Users of SP-initiated login may also be able to use IdP-initiated login, depending on your Identity Provider’s configuration.
Assertions and attributes
When a login occurs, a SAML Assertion containing user authorization is sent from the identity provider to Datadog.
Capabilities
- Datadog supports the HTTP-POST binding for SAML2:
urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST. - Datadog specifies
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddressfor the format of the NameIDPolicy in assertion requests.
Requirements
- Assertions must be signed.
- Assertions can be encrypted, but unencrypted assertions are accepted.
- Reference Datadog’s Service Provider metadata for more information. You must be signed in to Datadog to access the file.
Supported attributes
Attributes may be included in a SAML Assertion. Datadog looks for three attributes in an AttributeStatement:
- eduPersonPrincipalName: If specified, the eduPersonPrincipalName must correspond to the user’s Datadog username. The username is typically the user’s email address.
- sn: This is optional, and should be set to the user’s surname.
- givenName: This is optional, and should be set to the user’s first, or given name.
For the Microsoft Entra ID IdP, use the attribute `surname` instead of `sn` in the assertion.
Datadog expects that Attributes use the URI NameFormat urn:oasis:names:tc:SAML:2.0:attrname-format:uri or the Basic NameFormat urn:oasis:names:tc:SAML:2.0:attrname-format:basic. The name used for each attribute depends on the NameFormat that your IdP uses.
If your IdP is configured to use the URI NameFormat urn:oasis:names:tc:SAML:2.0:attrname-format:uri:
- eduPersonPrincipalName: The IdP should set
urn:oid:1.3.6.1.4.1.5923.1.1.1.6as the name of the attribute. - sn: The IdP should set
urn:oid:2.5.4.4as the name of the attribute. - givenName: The IdP should set
urn:oid:2.5.4.42as the name of the attribute.
If your IdP is configured to use the Basic NameFormat urn:oasis:names:tc:SAML:2.0:attrname-format:basic:
- eduPersonPrincipalName: The IdP should set
urn:mace:dir:attribute-def:eduPersonPrincipalNameas the name of the attribute. - sn: The IdP should set
urn:mace:dir:attribute-def:snas the name of the attribute. - givenName: The IdP should set
urn:mace:dir:attribute-def:givenNameas the name of the attribute.
If eduPersonPrincipalName exists in the AttributeStatement, the value of this attribute is used for the username. If eduPersonPrincipalName is not included in the AttributeStatement, the username is taken from the NameID in the Subject. The NameID must use the Format urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress.
If sn and givenName are provided, they are used to update the user’s name in their Datadog profile.
Additional features
To map attributes in your identity provider’s response to Datadog roles and teams, see SAML group mapping.
The following features can be enabled through the SAML Configuration dialog:
Note: You must have Admin permissions to see the SAML Configuration dialog.
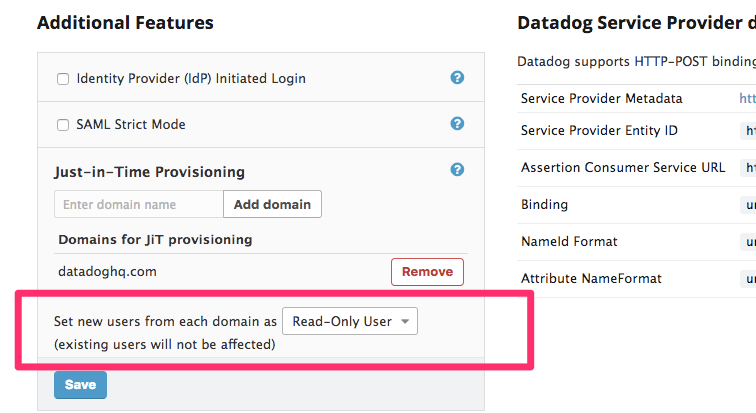
Just in time (JIT) provisioning
With JIT provisioning, a user is created within Datadog the first time they try to log in. This eliminates the need for administrators to manually create user accounts one at a time. The invitation email is not sent in this case.
Some organizations might not want to invite all of their users to Datadog. If you would like to make changes to how SAML works for your account, contact Datadog support. It is up to the organization to configure their IdP to not send assertions to Datadog if they don’t want a particular user to access Datadog.
Administrators can set the default role for new JIT users. The default role is Standard, but you can choose to add new JIT users as Read-Only, Administrators, or any custom role.
Important: If Role Mapping is enabled, it takes priority over the roles set during JIT provisioning. Without the proper Group Attribute statements, users might end up without roles and lose access to Datadog. To prevent users from being locked out after JIT provisioning, make sure to review your mapping definitions and check your assertions before enabling both Mappings and JIT.
IdP initiated login
When the Datadog URL is loaded, the browser is redirected to the customer IdP where the user enters their credentials, then the IdP redirects back to Datadog. Some IdPs have the ability to send an assertion directly to Datadog without first getting an AuthnRequest (IdP Initiated Login).
After enabling the IdP-initiated login feature and saving your configuration, you can download the latest version of the Service Provider (SP) metadata for your Identity Provider. Your new SP metadata contains a different, organization-specific AssertionConsumerService endpoint to send assertions to.
If you do not use the updated SP metadata, Datadog is not able to associate the assertion with your organization and displays an error page with a message that the SAML response is missing the “InResponseTo” attribute.
SAML strict
You can make your organization SAML Strict by disabling other login method types in the Login Methods UI. When this option is configured, all users must, by default, log in with SAML. An existing username and password, or Google OAuth login, does not work. This ensures that all users with access to Datadog must have valid credentials in your company’s identity provider or directory service to access your Datadog account. Org administrators can set per-user overrides to allow certain users to be SAML Strict exempt.
Self-updating Datadog SP metadata
Certain Identity Providers (such as Microsoft’s ADFS) can be configured to pull the latest SAML service provider metadata from Datadog. After you configure SAML in Datadog, you can get the metadata URL for your organization from the SAML Configuration page and use that with your Identity Provider to get the latest service provider metadata whenever changes are published.
Further Reading
Additional helpful documentation, links, and articles: