- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Extend Datadog
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Developer Integrations
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- AI Guard
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Setting and Querying User and Account Information in Traces
Overview
Getting visibility into users and accounts in APM helps you understand which users are affected by performance issues or errors. User and account information is displayed in the APM Investigator and Error Tracking issues.
By tagging traces with user and account identifiers, you can:
- Track which users are impacted by backend errors or latency issues.
- Analyze performance split by user or account segments.
- Monitor user-specific behaviors across your distributed systems.
Tag user and account information in spans
From RUM
If you’re already collecting Real User Monitoring data, you can propagate user and account information from browser or mobile applications to your backend traces:
Set user and account information using the
datadogRum.setUser()anddatadogRum.setAccount()APIs in your browser application.Enable trace propagation by configuring
allowedTracingUrlsin your RUM SDK initialization. See Connect RUM and Traces for detailed setup instructions. Additionally, setpropagateTraceBaggagetotrue, to automatically propagate user and account context in the baggage to backend traces alongside the trace context.
The user and account information is automatically remapped in the backend to the usr.id and account.id standard attributes, making it consistent across all your traces. Standard attributes allow you to filter and search your trace data consistently across all your services.
From APM SDKs
For backend services or applications without RUM, you can tag spans directly using APM SDKs:
Use the span tagging API (
set_tag,SetTag, orsetTagdepending on your language) to addusr.idandaccount.idattributes to your spans.To propagate user and account information across service boundaries, use trace context propagation with baggage.
Example (Python):
from ddtrace import tracer
# Tag the span with user and account information
span = tracer.current_root_span()
span.set_tag("usr.id", "user_123")
span.set_tag("account.id", "account_456")
# Set baggage to propagate across service boundaries
span.context.set_baggage_item("user.id", "user_123")
span.context.set_baggage_item("account.id", "account_456")
Note: When propagating user and account information through baggage, this information is only tagged on service entry spans. This means the usr.id and account.id attributes appear on the first span of each service in your distributed trace.
Query trace data with user and account information
Tagging spans with user and account IDs enables powerful analysis, giving you visibility into how backend errors and latency affect end-users.
Enrich your trace analysis by querying span data with attributes from Product Analytics User and Account Profiles. To express interest in this upcoming capability, reach out to Support.
Filter traces by user or account in the APM Trace Explorer
Query traces using the usr.id or account.id attributes:
- Search for all traces from a specific user or account:
@usr.id:user_123or@account.id:account_456. - Combine with other filters:
@usr.id:user_123 service:checkout status:error.
This allows you to investigate issues affecting specific users or accounts and understand their end-to-end experience across your distributed system.
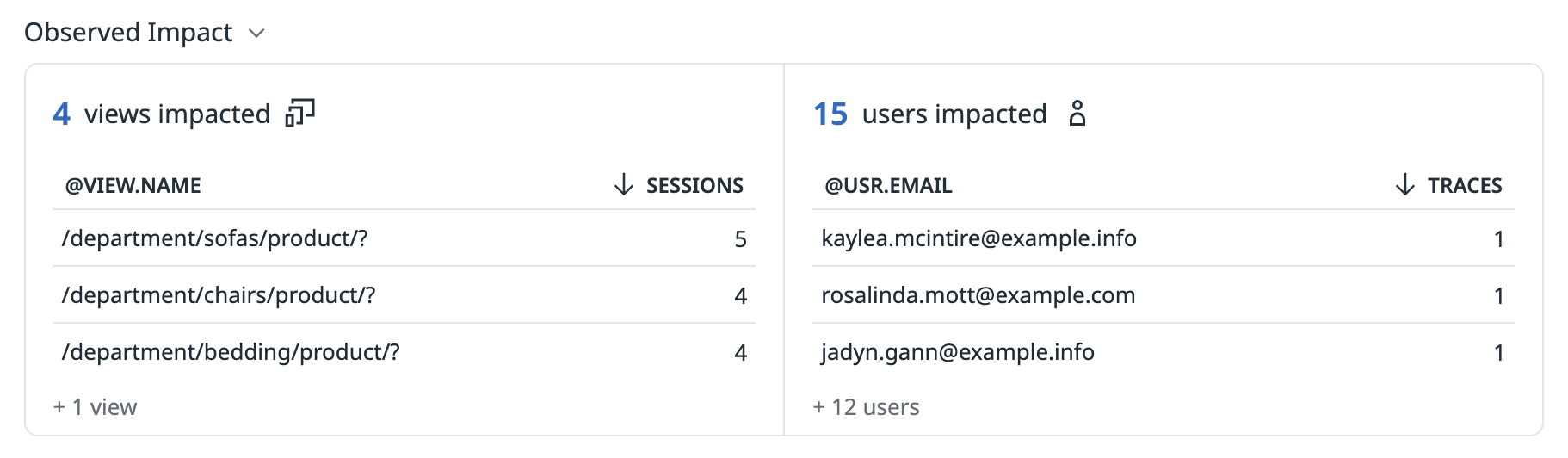
Identify which users or accounts are most affected by errors or latency
Analyze error patterns and latency issues across your user base to prioritize fixes based on business impact:
- Use Tag Analysis to identify which users or accounts are disproportionately affected by errors or high latency on backend services.
- Group queries by
usr.idoraccount.idto analyze error rates or latency percentiles by user or account. - View user and account impact directly in the APM Investigator and Error Tracking issues to understand the scope of production problems.
This helps you prioritize incident response based on the number of affected users or the importance of affected accounts.
Create monitors and alerts based on user or account segments
Set up APM monitors that alert you when specific user segments experience degraded performance:
- Create error rate monitors filtered by premium account tiers:
@account.id:premium_* status:error. - Alert on latency spikes for critical users:
@usr.id:vip_user_* @duration:>5s. - Monitor SLA compliance for enterprise accounts by setting monitors on specific account IDs.
This enables proactive monitoring and ensures you can respond quickly when high-value users or accounts experience issues.
Further reading
Additional helpful documentation, links, and articles: