- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Coverage
Workload Protection Coverage provides a real-time view of security coverage across all your hosts. Use Coverage to assess protection posture, identify gaps, and take immediate action.
Key functionality
- Real-time visibility: Coverage updates every five minutes for accurate, current status.
- Granular filtering: Search by policy, rule, version, status, tactic, or technique.
- Direct drill-down: Drill down from a high-level map to a detailed asset or policy view.
- Actionable alerts: Highlight workloads in a warning or failed state so you can respond promptly.
- Coverage analytics: Track rule deployment health, stale agents, and configuration issues.
Key benefits
- Reduce blind spots by monitoring for unprotected workloads.
- Shorten detection and response times with direct remediation workflows.
- Maintain continuous compliance and policy alignment.
- Integrate posture checks into CI/CD and infrastructure reviews.
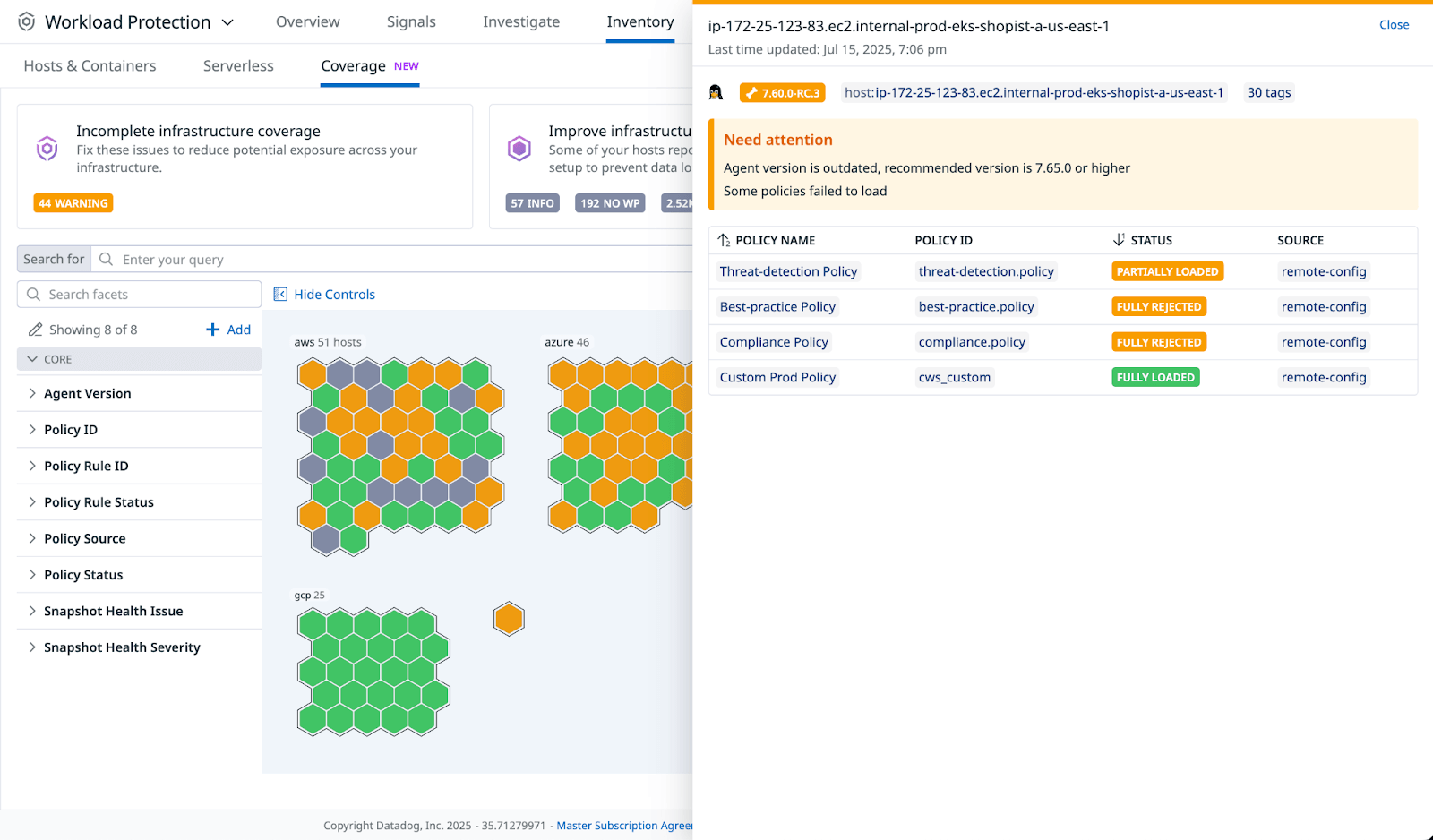
Policy statuses
Hosts are identified with the following colors:
- Green: all rules in the policies applied to the host have passed.
- Orange: one or more rules in the policies applied to the host are in error.
Click an orange hexagon to view a host with policy rules in error.
Policies are displayed with the following statuses:
- Fully Loaded: all of the policy’s rules pass.
- Partially Loaded: some of the policy’s rules fail.
- Fully Rejected: the entire policy is failing.
Use cases
Here are some ways to use Coverage to improve your workload security.
Detect and remediate policy deployment issues
From the Incomplete infrastructure coverage status card on the Coverage page, you can address policy deployment issues:
- In Incomplete infrastructure coverage, click Warning, and then select the policies in Security coverage needs attention. In the Coverage map, assets with policy deployment problems are displayed as orange hexagons.
- Review the list of deployed policies. Policies are highlighted with statuses such as Partially Loaded, Fully Rejected, and so on.
- In the policy details, do one of the following:
- Edit a policy.
- View a policy’s rule errors, and then edit them as needed.
- Redeploy and confirm the fix in the Coverage map.
Identify assets missing Workload Protection
From the Incomplete infrastructure coverage status card on the Coverage page, you can review assets without full Workload Protection (WP):
- In Improve infrastructure coverage, click NO WP. NO WP shows how many hosts are running the Datadog Agent without Workload Protection enabled.
- Click Inspect Hosts Without WP. Fleet Automation appears, allowing you to set up Workload Protection.
Identify assets missing key features
From the Incomplete infrastructure coverage status card on the Coverage page, you can find assets with gaps in protection.
- In Improve infrastructure coverage, click INFO to review the
outdated_agentflag. Theoutdated_agentflag means an outdated Agent version is running and might not support the latest Workload Protection features. - In Improve infrastructure coverage, click NO AGENT. NO AGENT shows how many hosts are not running the Datadog Agent, and therefore can’t be evaluated by Workload Protection.
- Click Inspect Hosts Without Agent. The Resource Catalog appears, allowing you to address hosts missing agents.
- Filter by Agent Version to detect outdated agents lacking recent security updates.
- Update the Agent to ensure complete coverage.
Search assets by MITRE ATT&CK techniques and tactics
From the Filter by tactics, techniques, and policy types status card on the Coverage page, built-in filters for Tactics, Techniques, and Policies show exactly which parts of the MITRE ATT&CK framework are covered.
To use these filters to strengthen detection and response alignment with proven MITRE ATT&CK framework threat models, do the following:
- Click Tactics to filter for high-priority tactics (for example,
TA004-privilege-escalation,TA004-persistence), to ensure those are protected across all hosts. - After the map updates for the tactic you selected, click Techniques and select a technique to identify gaps in technique coverage for critical systems.
- Click Policies and select a policy type to see the distribution of policies across the filtered infrastructure.
For information about the MITRE ATT&CK map available in SIEM or Workload Protection, see MITRE ATT&CK map.
Experiment with new rules
You can use Coverage to test and iterate on custom security rules:
- Write and deploy a new custom rule.
- In Coverage, search for the rule by rule ID, policy ID, or hostname.
- Confirm that the agent has loaded the rule successfully.
- If errors appear, review the details, fix the rule, and redeploy.
Workload coverage triage and remediation cycle
As an example of how to use Coverage to triage and remediate coverage issues, here is a sequence that starts by establishing a baseline, closing blind spots, and securing the most critical assets. It then verifies enforcement mechanisms, restores agent health, and aligns detection coverage with known adversary behaviors. Finally, it applies rule updates, confirms effectiveness, and records the state for audit and incident reference.
- Do a full environment view to establish baseline coverage status.
- Focus on assets that appear fully covered. Validate that their policies, rules, and agents are working as intended before addressing visible gaps. This uncovers silent failures in trusted systems that would otherwise be ignored.
- Identify all unprotected or partially protected workloads.
- Prioritize assets with the highest business impact and exposure.
- Verify policy deployment and enforcement on those assets.
- Check for outdated or unhealthy agents on all remaining workloads.
- Map current detection coverage to MITRE ATT&CK to find gaps in tactics and techniques.
- Deploy or update detection rules to close those gaps.
- Reassess coverage to confirm posture changes took effect.
- Log the final state for compliance and future comparison.
Further reading
Additional helpful documentation, links, and articles: