- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profiler
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Cloud Cost
- Application Performance
- APM
- APM Terms and Concepts
- Application Instrumentation
- APM Metrics Collection
- Trace Pipeline Configuration
- Correlate Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origins for Spans
- Service Observability
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Error Tracking
- Data Security
- Guides
- Troubleshooting
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
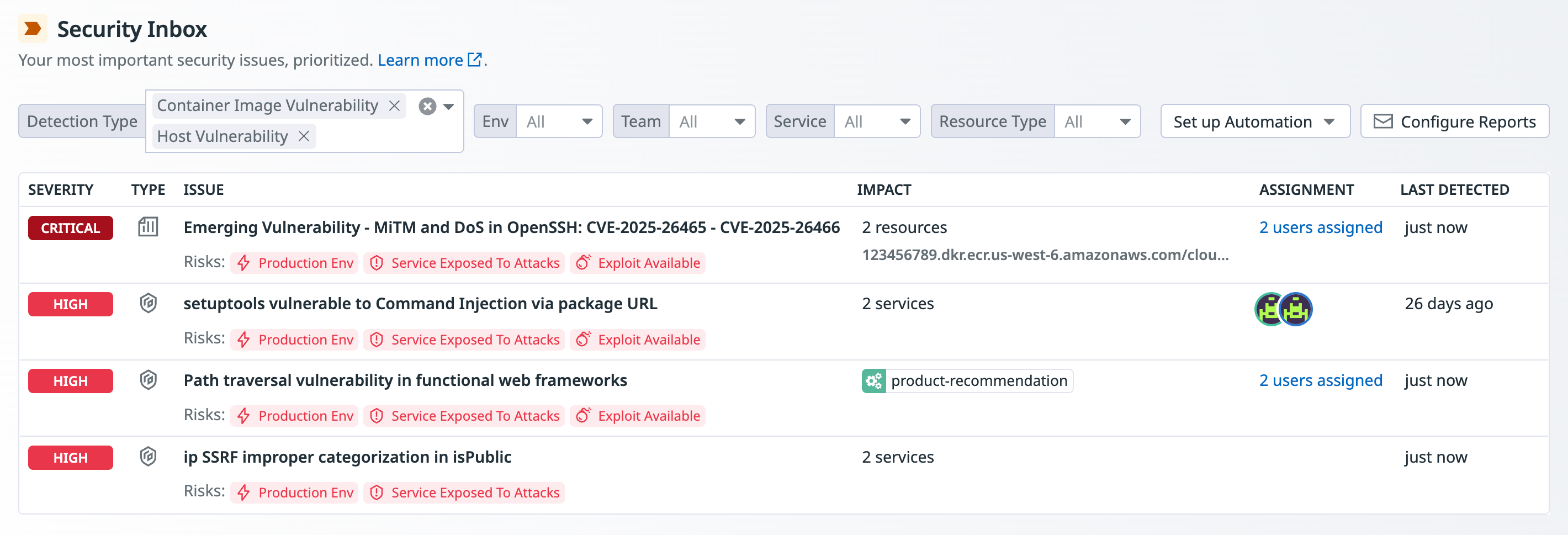
Security Inbox
Security Inbox provides a consolidated, actionable list of your most important security findings. It automatically contextualizes and correlates insights from Datadog security products across vulnerabilities, signals, misconfigurations, and identity risks into a unified, prioritized view of actions to take to strengthen your environment.
Types of findings in Security Inbox
The findings that appear in Security Inbox are generated from App and API Protection (AAP) and Cloud Security. By default, these include the following types of findings:
- A curated set of misconfigurations for Cloud Security Misconfigurations, compiled by Datadog Security Research.
- A curated set of identity risks for Cloud Security Identity Risks, compiled by Datadog Security Research.
- Application library vulnerabilities for Software Composition Analysis(SCA). All high and critical application library vulnerabilities on production services under attack appear in the inbox.
- Application code vulnerabilities for Code Security vulnerabilities. All high and critical application code vulnerabilities appear in the inbox.
- Emerging vulnerabilities, which are infrastructure vulnerabilities that have had CVEs published in the last 30 days and that have a Datadog severity score of Critical, or that the Datadog Security Research team has published. When Datadog rates a vulnerability as Critical, that means it’s an exploitable critical vulnerability that affects an internet-facing production resource.
- Attack Paths. An attack path outlines a series of interconnected misconfigurations, container image, host, and application vulnerabilities that malicious actors could leverage to gain unauthorized access, escalate privileges, or compromise sensitive data in your cloud environment. All attack paths are listed in Security Inbox by default.
Security Inbox also takes the following detected risks into consideration when determining which findings appear in the inbox:
- Public accessibility: Publicly exposed resources carry elevated risk, especially if they contain vulnerabilities or misconfigurations. To learn more, see How Datadog Determines if Resources are Publicly Accessible.
- Privileged access: Resources with privileged access carry elevated risk as they grant elevated permissions that can expand the attack surface.
- Under attack: Resources that are seeing suspicious security activity carry elevated risks. Resources are flagged as “Under Attack” if a security signal has been detected on the resource in the last 15 days.
- Exploit available: Vulnerabilities with public exploits available carry elevated risks. The availability of a public exploit is verified with different exploit databases, such as cisa.gov, exploit-db.com, and nvd.nist.gov.
- In production: Vulnerabilities in production environments carry elevated risks. The environment is computed from the
envandenvironmenttags.
How Security Inbox prioritization works
Security Inbox ranks issues by considering the severity of a finding first, followed by the number of correlated risks, and then the number of impacted resources and services.
- Severity (Critical, High, Medium, and Low): Severity is determined by the Datadog Security Scoring Framework for cloud misconfigurations and identity risks, and by CVSS 3.1 for vulnerabilities.
- Number of detected risks: When two findings have the same severity, the one with a greater number of detected risks is given higher priority.
- Number of impacted resources and services: If two findings share both the same severity and the same number of detected risks, the finding that impacts a greater number of resources and services is prioritized higher.
Note: The type of finding, detected risk, or impacted resource does not influence prioritization.
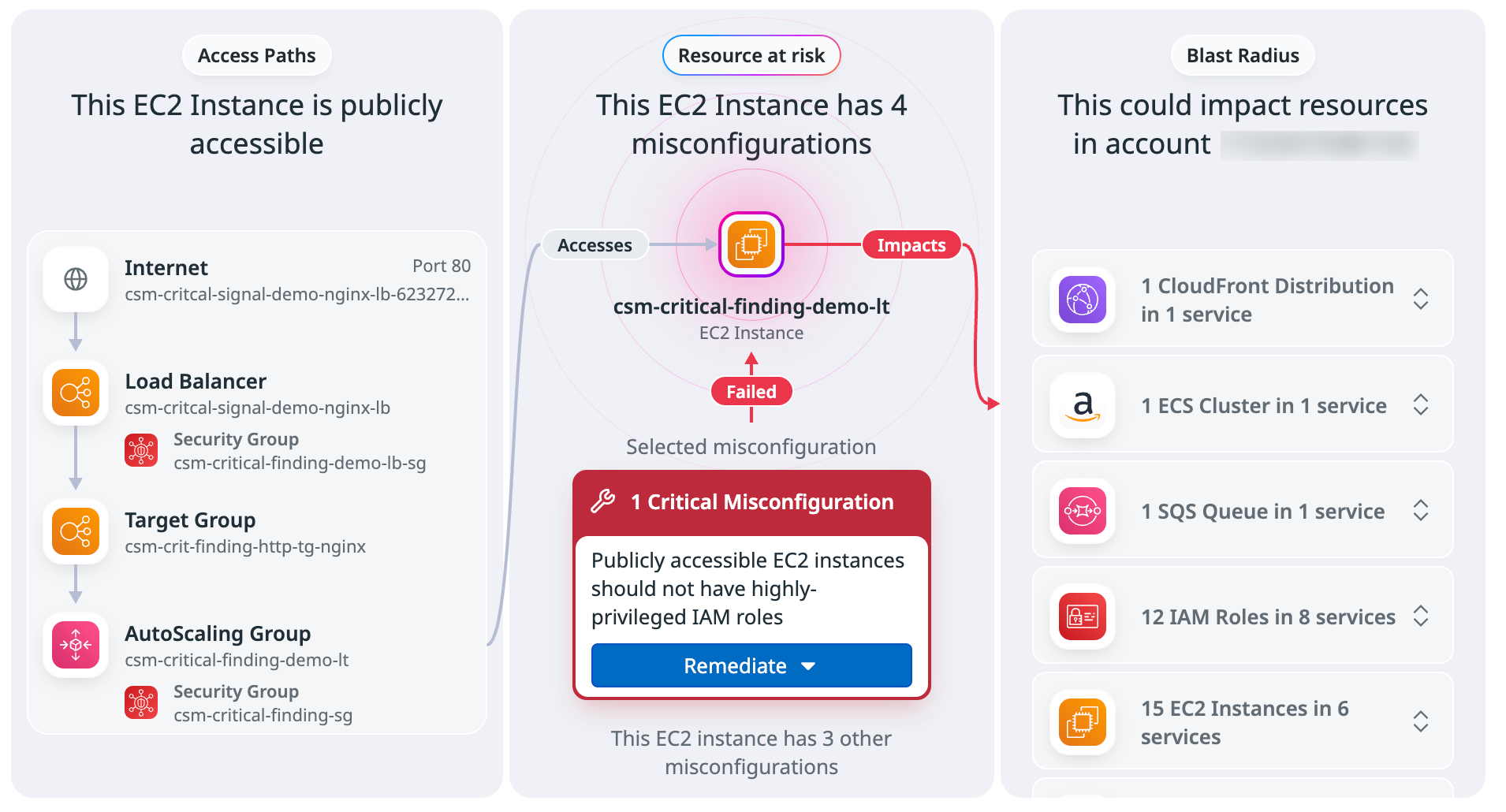
Use the security context map to identify and mitigate vulnerabilities
The security context map for Attack Paths provides a comprehensive view to help identify and address potential breach points. It effectively maps interconnected misconfigurations, permission gaps, and vulnerabilities that attackers might exploit.
Key features include:
- Risk assessment: The map enables security teams to assess the broader impact of vulnerabilities and misconfigurations. This includes evaluating whether security policies—such as access paths and permissions—need updating, and understanding the compliance implications of exposure, particularly when sensitive data is at risk within the blast radius.
- Actionable context for immediate response: The map includes service ownership information and other relevant context, allowing teams to make informed, real-time decisions. Teams can take action directly from the map by running integrated workflows, sharing security issue links, and accessing the AWS console view of resources for efficient remediation, all without switching tools.
Customize Security Inbox to highlight crucial issues
Automation Pipelines enables you to configure rules that customize your Security Inbox, allowing you to highlight issues that are critical to your organization. By setting up these automated rules, you can streamline the management of newly discovered vulnerabilities, enhancing triage and remediation efforts at scale. Leveraging both the Automation Pipelines and Add to Security Inbox rules, you can optimize your security operations in the following ways:
- Resurface issues not captured by default: Highlight issues that might be missed by default or custom detection rules, ensuring no critical issue is overlooked.
- Strengthen compliance and address key system concerns: Address concerns affecting regulatory compliance or important business systems, regardless of severity.
- Prioritize current risks: Focus on immediate threats, such as identity risks after an incident or industry-wide vulnerabilities.
For more information, see Automation Pipelines and Add to Security Inbox Rules.
Further Reading
Additional helpful documentation, links, and articles: