- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profiler
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Cloud Cost
- Application Performance
- APM
- APM Terms and Concepts
- Application Instrumentation
- APM Metrics Collection
- Trace Pipeline Configuration
- Correlate Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origins for Spans
- Service Observability
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Error Tracking
- Data Security
- Guides
- Troubleshooting
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Datadog Resource Catalog
This product is not supported for your selected Datadog site. ().
Overview
Datadog Resource Catalog is the central hub of all your infrastructure resources. It can help you manage resource compliance, investigate root causes for incidents, and close observability gaps on your infrastructure. With the Resource Catalog, you can understand key resource information such as metadata, ownership, configurations, relationship between assets, and active security risks for your resources.
Resource Catalog leverages Datadog cloud integrations and the Datadog Agent to gather data from cloud resources such as hosts, databases, and storage services.
Use Cases
Resource policies and reporting
- Gain visibility into the compliance of your infrastructure with regards to ownership, versioning, migrations, and so on.
- Facilitate good tagging practices to optimize cross-telemetry insights.
- Reduce application risks by identifying and fixing security vulnerabilities in the dependencies of your services.
- Provide engineering leadership with a high-level view of security practices across teams and cloud accounts.
- Export resources for record-keeping or auditing.
Troubleshoot incidents and performance issues
- Access telemetry, dashboards and other Datadog views with rich insights to understand the health and performance of your resources.
- Locate team and service owners of relevant resources to speed up incident recovery.
- View resource configuration changes to identify probable root causes.
Optimize observability
- Spot resources that can be better monitored by Datadog and bridge observability gaps.
- Ensure proper security coverage by identifying resources that are most prone to misconfigurations or are not actively reporting security misconfigurations.
Setup
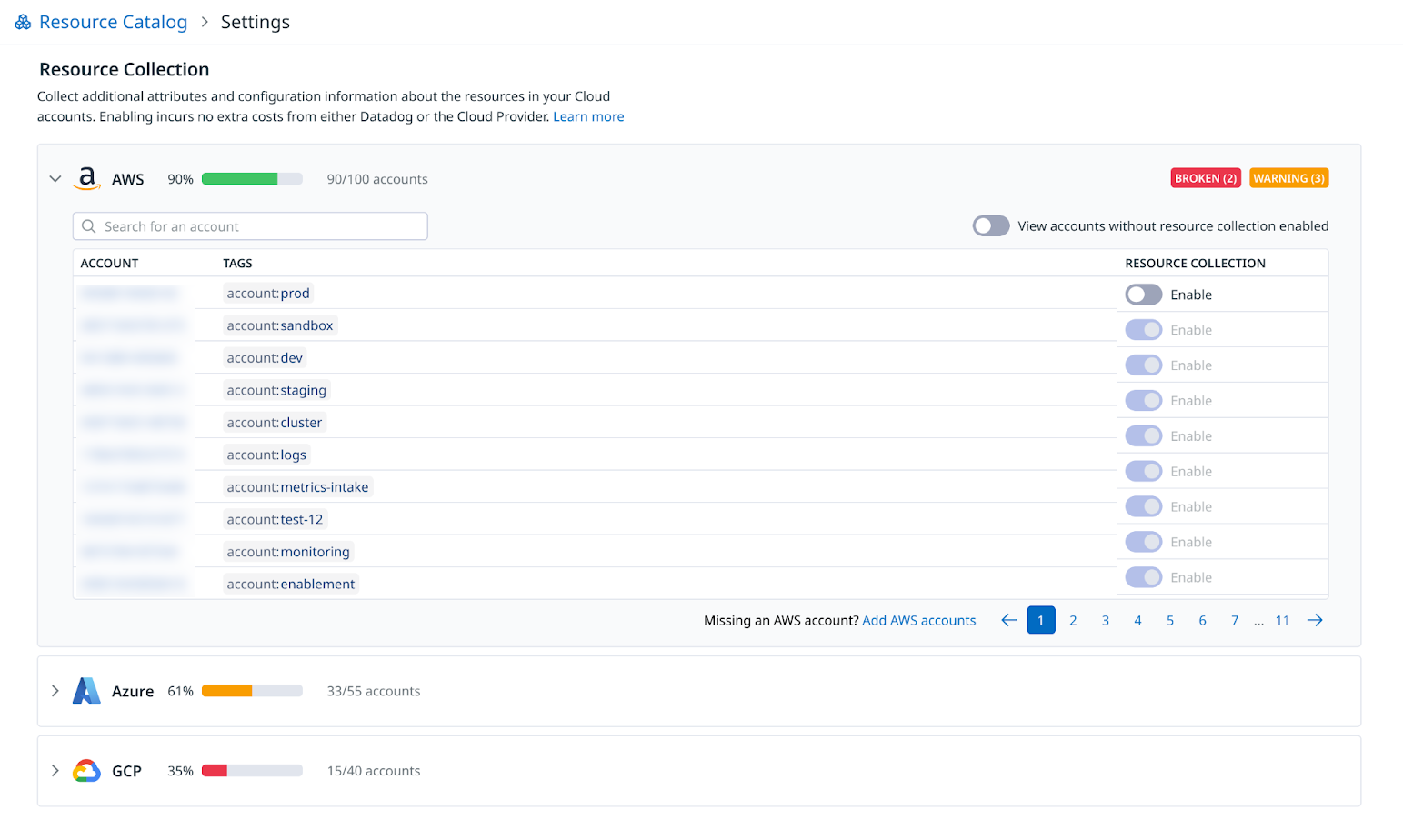
By default, when you navigate to the Resource Catalog, you are able to see Datadog Agent monitored hosts, as well as cloud resources crawled for other Datadog products such as CNM (Cloud Network Monitoring), and DBM (Database Monitoring). To view additional cloud resources in the Resource Catalog, toggle on extend resource collection from the Resource Catalog setup page.
Note: Extending resource collection does not incur additional costs. The Resource Catalog is a free product for Infrastructure Monitoring customers.
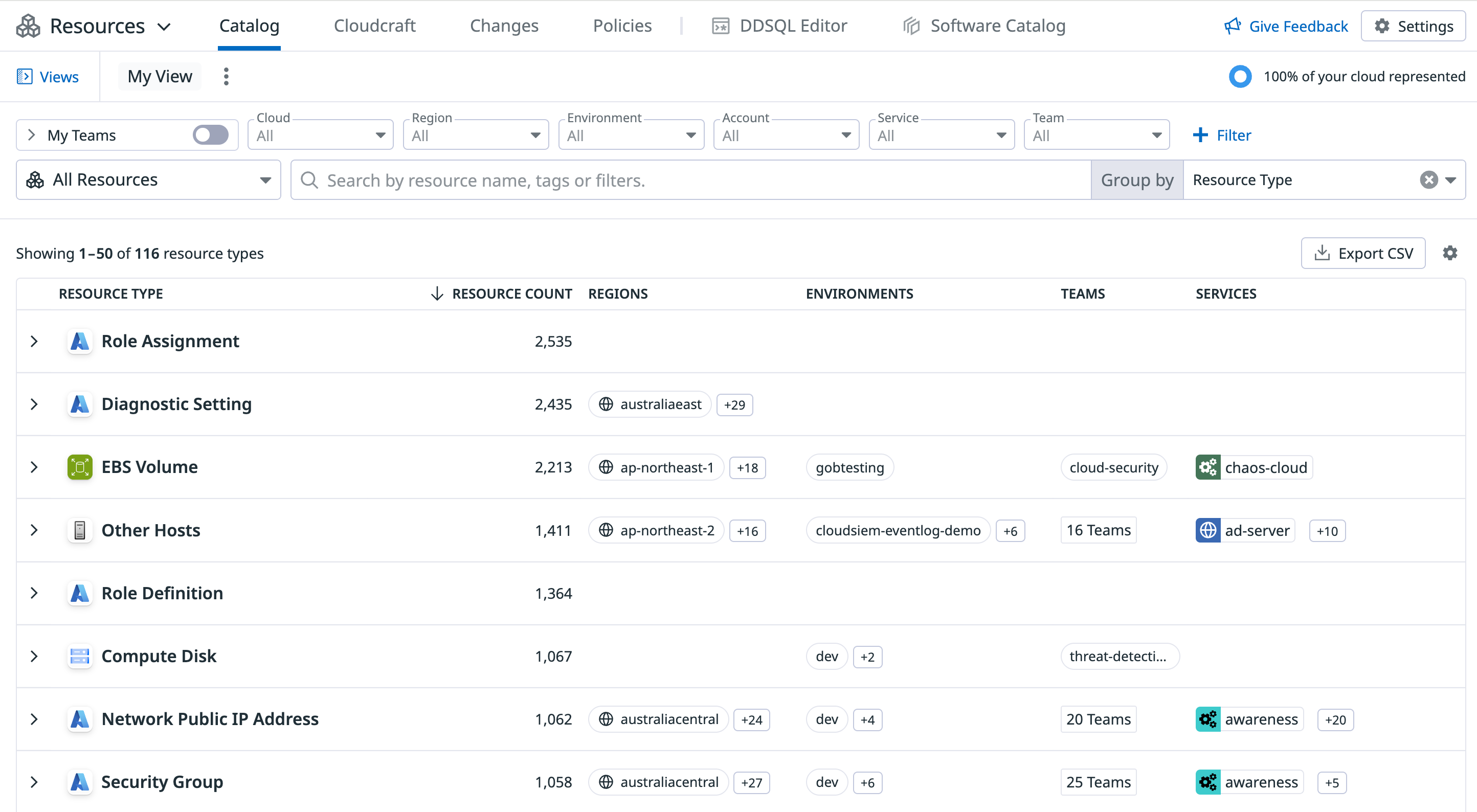
Browse the Resource Catalog
On the Resource Catalog page, explore the cloud resources in your Datadog organization. The catalog detects a resource either because it has an Agent installed on it, or because a cloud integration is configured on it.
Catalog tab
The Catalog tab shows context for a resource, including team ownership and related services. It helps you proactively identify and fill in missing ownership information before it’s needed in an incident. The Resource Catalog also shows resource attributes customized for each resource type. You can search resources by specific attributes such as the instance type for a host, or the version for a database.
Note: If you use Datadog Teams, select the Teams toggle on the left panel, then select the toggle for the teams to which you’re assigned to view only the resources assigned to those teams. In addition, you can export your Resource Catalog list as a CSV file from the top right corner of the list.
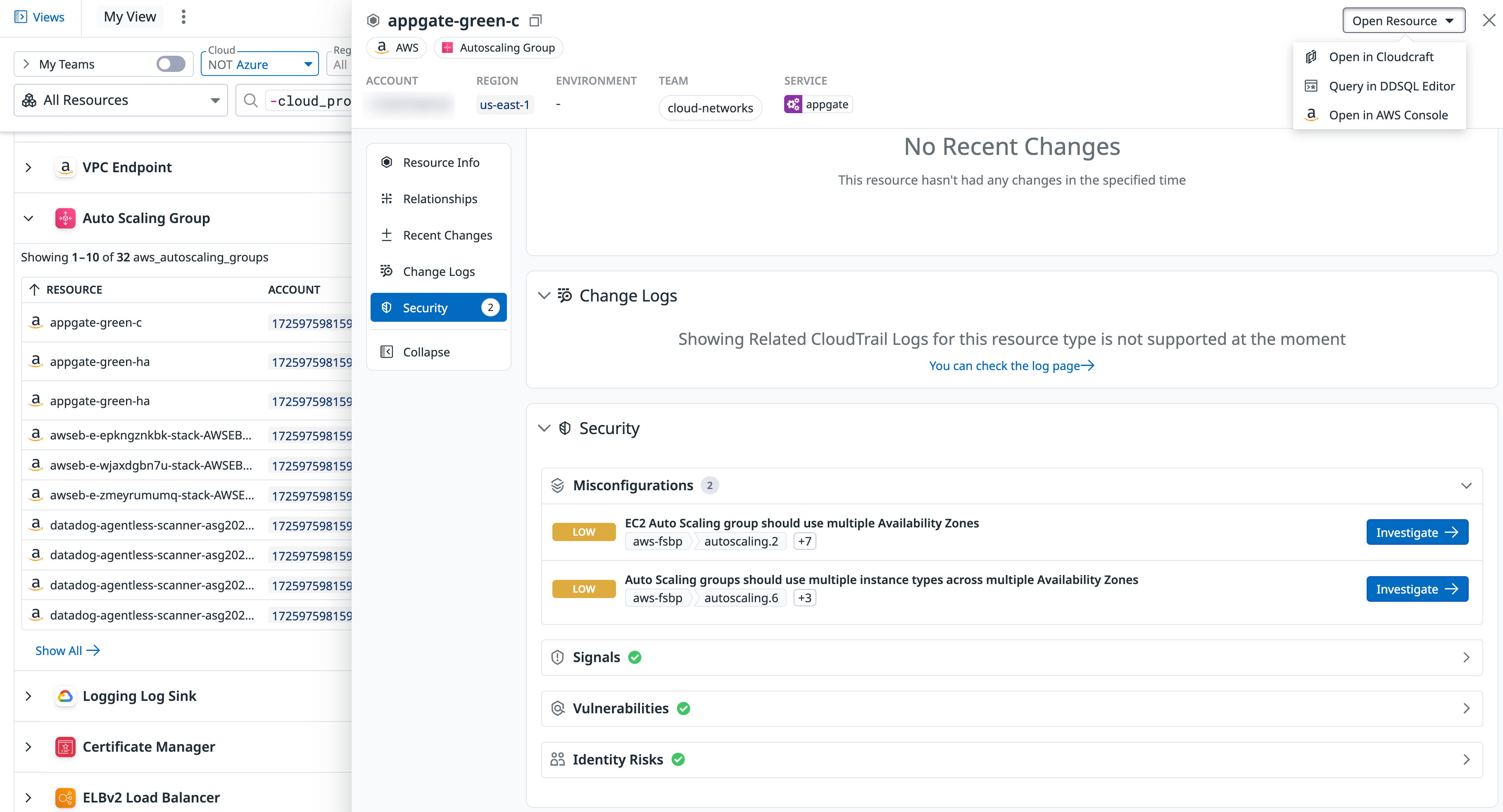
To access the relevant cloud console for any resource in your list, click on a resource to open a side panel. Then, click the Open Resource dropdown in the top right corner to be redirected.
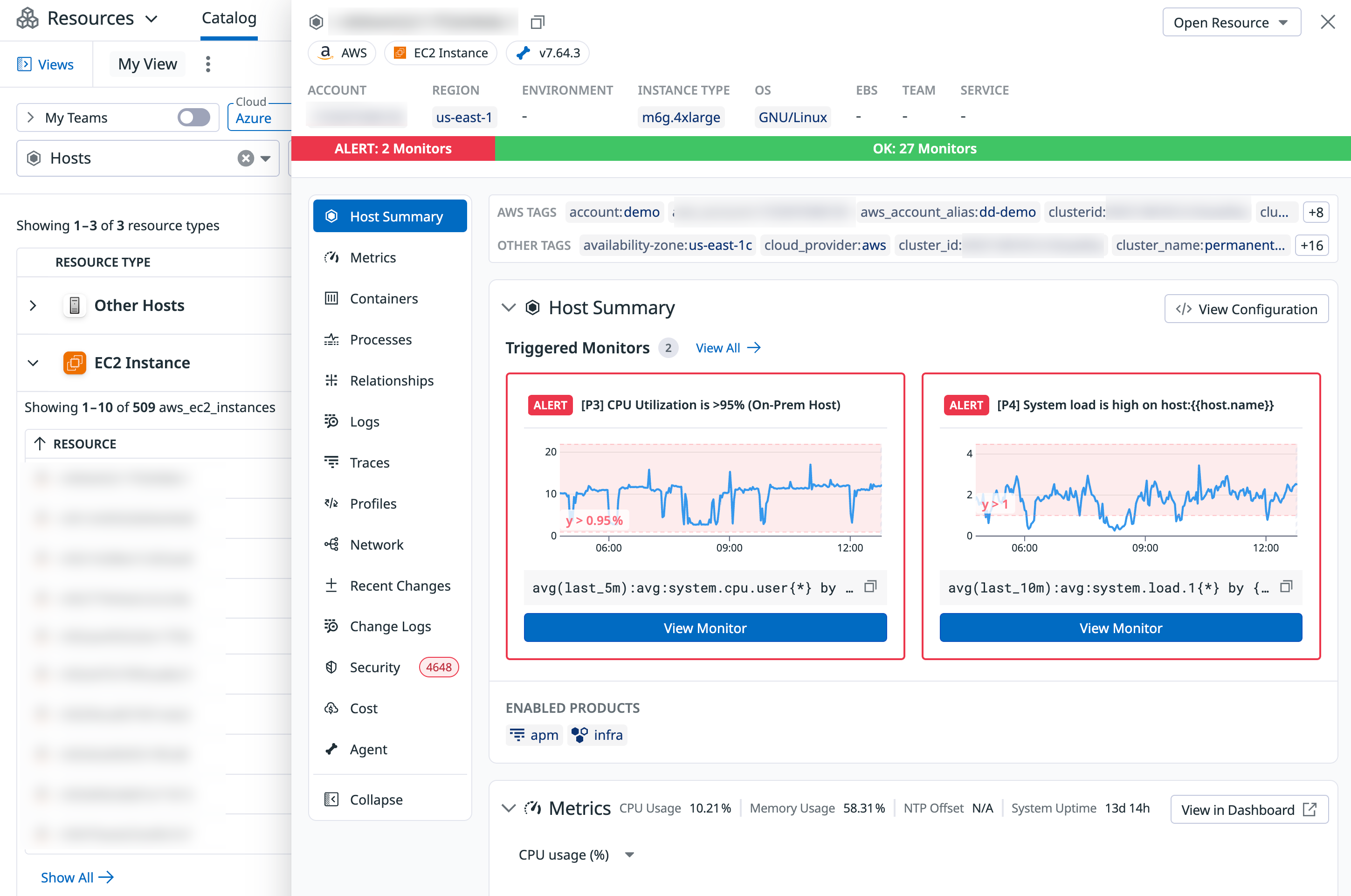
Investigate a host or resource
No secrets are displayed in this panel. Any displayed "secrets" are randomly generated strings that do not pose a security risk.
Clicking on a host opens a side panel with details including:
- Host information such as the name, account, OS, instance type, tags, and metadata associated with the resource
- Telemetry including metrics, logs, traces, processes, and so on
- Active monitor alerts and enabled monitors status on the host
- Agent configuration information
Clicking on any resource opens a side panel with details including:
- Resource information such as the resource type, name, account, and tags associated with the resource.
- Resource definition in JSON showing the full configuration of the asset.
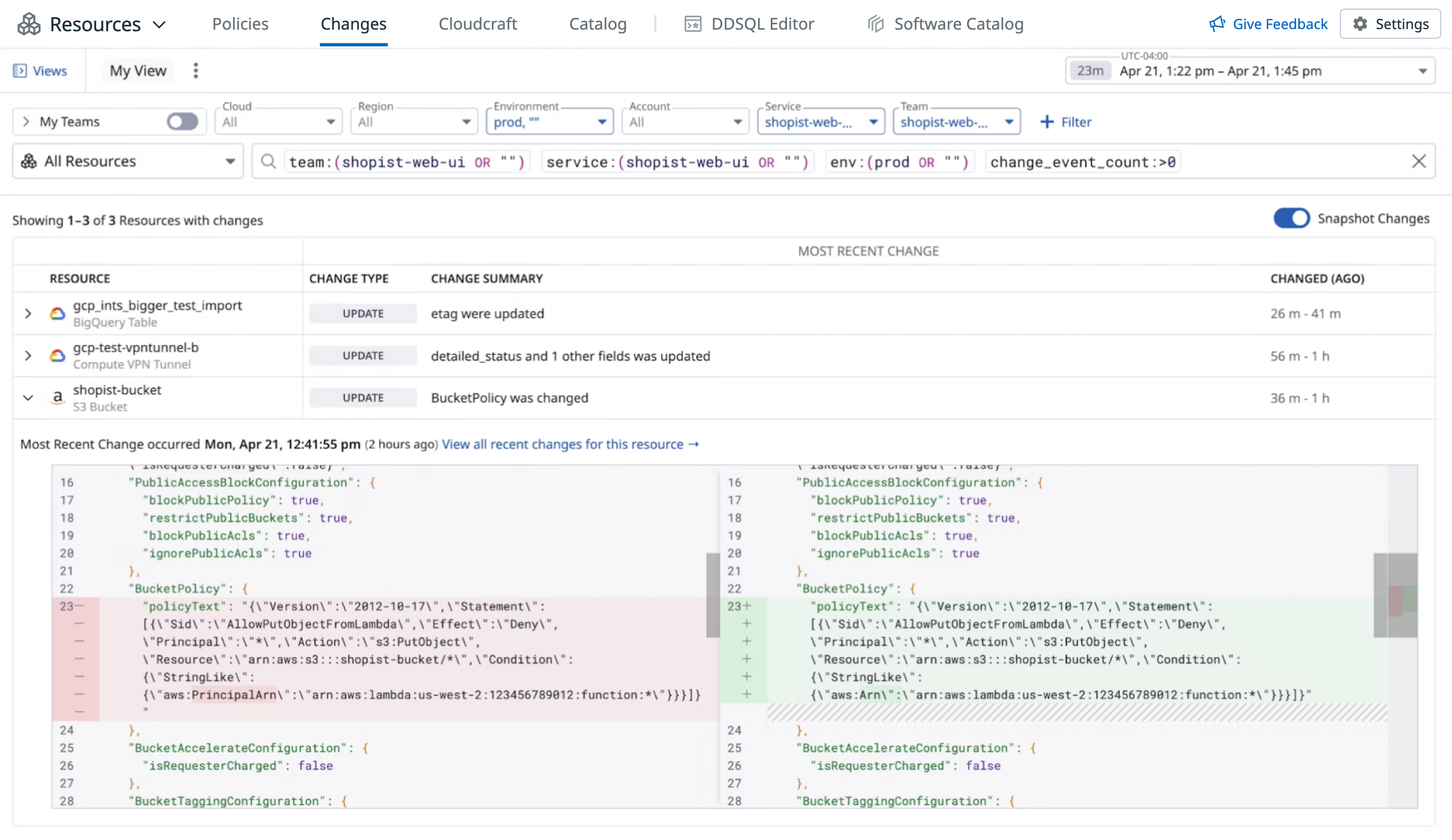
- Recent Changes showing a 7-day history of changes to the resource
- Relationship view showing interdependencies between resources
- Service and team ownership of the resource
- Security risks that the resource is exposed to, including misconfigurations, signals, identity risks, and vulnerabilities
Resource Changes (in Preview)
Join the Preview!
Resource Changes is in Preview. Click Request Access and complete the form to request access.
Request AccessResource Changes provides visibility and control over configuration changes to your cloud infrastructure. It helps you monitor modifications to resources, aiding in troubleshooting incidents and understanding the evolution of your environment.
For more information, see Resource Changes.
Further reading
Additional helpful documentation, links, and articles: