- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profiler
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Cloud Cost
- Application Performance
- APM
- APM Terms and Concepts
- Application Instrumentation
- APM Metrics Collection
- Trace Pipeline Configuration
- Correlate Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origins for Spans
- Service Observability
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Error Tracking
- Data Security
- Guides
- Troubleshooting
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
AWS Fargate Configuration Guide for Datadog Security
This guide walks you through configuring Cloud Security, Software Composition Analysis (SCA), Threat Detection and Protection (AAP), and Cloud SIEM on AWS Fargate.
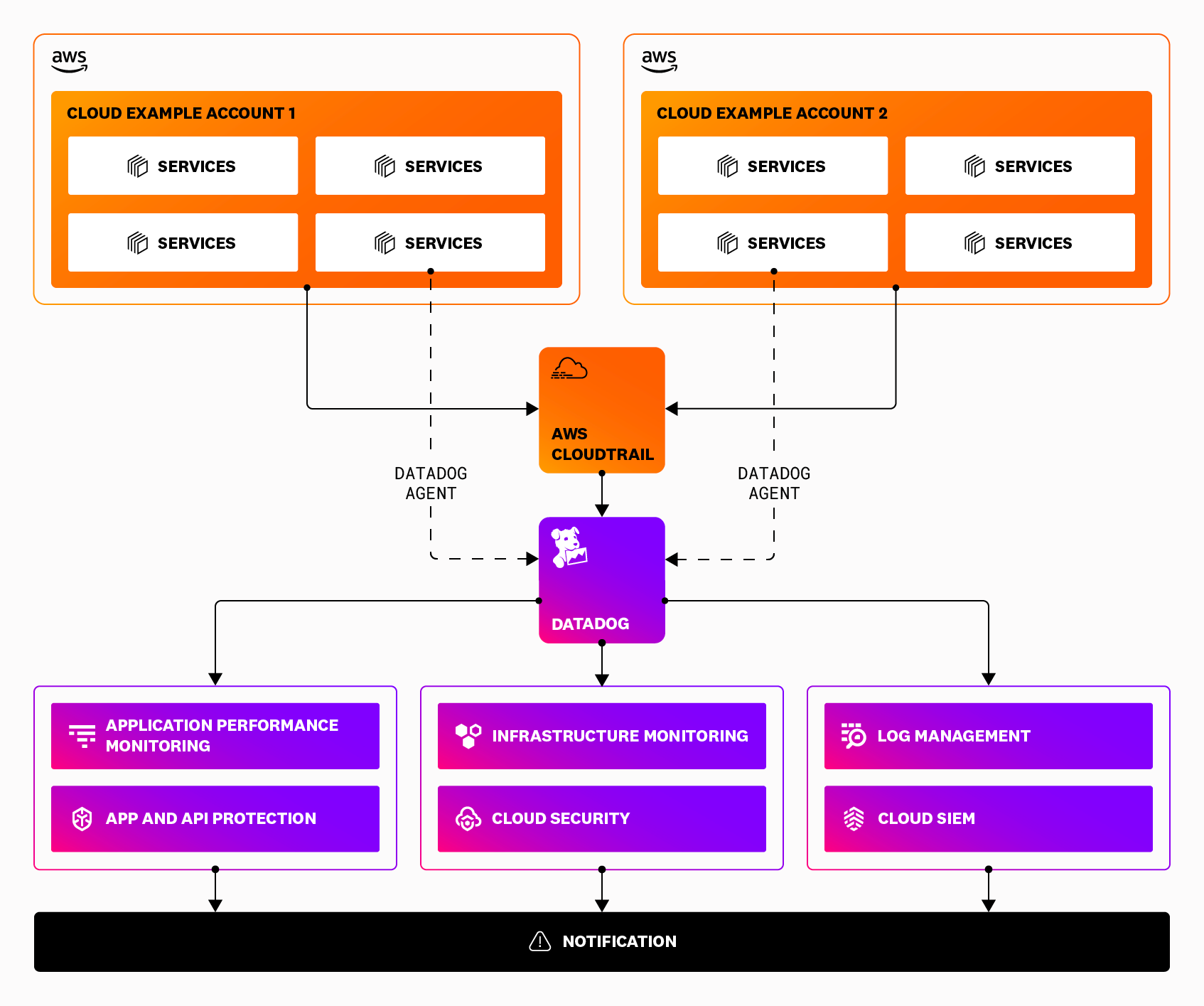
Full stack coverage for AWS Fargate
Datadog Security provides multiple layers of visibility for AWS Fargate. Use the products in combination with one another to gain full stack coverage, as shown in the following tables:
Fargate assets
| Asset | Observability | Vulnerabilities and Misconfiguration Remediation | Threat Detection and Response |
|---|---|---|---|
| Fargate Application | Application Performance Monitoring | Software Composition Analysis (SCA) and Code Security | AAP - Threat Detection and Protection |
| Fargate Infrastructure | Infrastructure Monitoring | Cloud Security | Workload Protection |
Fargate-related resources
| Asset | Observability | Vulnerabilities and Misconfiguration Remediation | Threat Detection and Response |
|---|---|---|---|
| AWS IAM roles and policies | Log Management | Cloud Security | Cloud SIEM |
| AWS databases | Log Management | Cloud Security | Cloud SIEM |
| AWS S3 buckets | Log Management | Cloud Security | Cloud SIEM |
Cloud Security
Prerequisites
- The Datadog AWS integration is installed and configured for your AWS accounts
- Access to AWS Management Console
- AWS Fargate ECS or EKS workloads
For additional performance and reliability insights, Datadog recommends enabling Infrastructure Monitoring with Cloud Security.
Images
cws-instrumentation-init:public.ecr.aws/datadog/cws-instrumentation:latestdatadog-agent:public.ecr.aws/datadog/agent:latest
Installation
AWS Console
- Sign in to AWS Management Console.
- Navigate to the ECS section.
- On the left menu, select Task Definitions, and then select Create new Task Definition with JSON. Alternatively, choose an existing Fargate task definition.
- To create a new task definition, use the JSON definition, or the AWS CLI method.
- Click Create to create the task definition.
AWS CLI
- Download datadog-agent-cws-ecs-fargate.json.
datadog-agent-cws-ecs-fargate.json
{
"family": "<YOUR_TASK_NAME>",
"cpu": "256",
"memory": "512",
"networkMode": "awsvpc",
"pidMode": "task",
"requiresCompatibilities": [
"FARGATE"
],
"containerDefinitions": [
{
"name": "cws-instrumentation-init",
"image": "public.ecr.aws/datadog/cws-instrumentation:latest",
"essential": false,
"user": "0",
"command": [
"/cws-instrumentation",
"setup",
"--cws-volume-mount",
"/cws-instrumentation-volume"
],
"mountPoints": [
{
"sourceVolume": "cws-instrumentation-volume",
"containerPath": "/cws-instrumentation-volume",
"readOnly": false
}
]
},
{
"name": "datadog-agent",
"image": "public.ecr.aws/datadog/agent:latest",
"essential": true,
"environment": [
{
"name": "DD_API_KEY",
"value": "<DD_API_KEY>"
},
{
"name": "DD_SITE",
"value": "datadoghq.com"
},
{
"name": "ECS_FARGATE",
"value": "true"
},
{
"name": "DD_RUNTIME_SECURITY_CONFIG_ENABLED",
"value": "true"
},
{
"name": "DD_RUNTIME_SECURITY_CONFIG_EBPFLESS_ENABLED",
"value": "true"
}
],
"healthCheck": {
"command": [
"CMD-SHELL",
"/probe.sh"
],
"interval": 30,
"timeout": 5,
"retries": 2,
"startPeriod": 60
}
},
{
"name": "<YOUR_APP_NAME>",
"image": "<YOUR_APP_IMAGE>",
"entryPoint": [
"/cws-instrumentation-volume/cws-instrumentation",
"trace",
"--",
"<ENTRYPOINT>"
],
"mountPoints": [
{
"sourceVolume": "cws-instrumentation-volume",
"containerPath": "/cws-instrumentation-volume",
"readOnly": true
}
],
"linuxParameters": {
"capabilities": {
"add": [
"SYS_PTRACE"
]
}
},
"dependsOn": [
{
"containerName": "datadog-agent",
"condition": "HEALTHY"
},
{
"containerName": "cws-instrumentation-init",
"condition": "SUCCESS"
}
]
}
],
"volumes": [
{
"name": "cws-instrumentation-volume"
}
]
}Update the following items in the JSON file:
TASK_NAMEDD_API_KEYDD_SITEYOUR_APP_NAMEYOUR_APP_IMAGEENTRYPOINT
You can use the following command to find the entry point of your workload:
docker inspect <YOUR_APP_IMAGE> -f '{{json .Config.Entrypoint}}'or
docker inspect <YOUR_APP_IMAGE> -f '{{json .Config.Cmd}}'Note: The environment variable
ECS_FARGATEis already set to “true”.Add your other application containers to the task definition. For details on collecting integration metrics, see Integration Setup for ECS Fargate.
Run the following command to register the ECS task definition:
aws ecs register-task-definition --cli-input-json file://<PATH_TO_FILE>/datadog-agent-ecs-fargate.jsonDatadog Cloud Security
- In Datadog, navigate to Cloud Security > Setup > Cloud Integrations > AWS.
- Enable Vulnerability Management by deploying the Datadog Agentless scanner on your AWS accounts hosting your Amazon ECR.
To collect data from your AWS Fargate pods, you must run the Agent as a sidecar of your application pod and set up Role-Based Access Control (RBAC) rules.
If the Agent is running as a sidecar, it can only communicate with containers on the same pod. Run an Agent for every pod you wish to monitor.
Set up RBAC rules
Use the following Agent RBAC deployment instruction before deploying the Agent as a sidecar.
Deploy the Agent as a sidecar
The following manifest represents the minimum configuration required to deploy your application with the Datadog Agent as a sidecar with Workload Protection enabled:
apiVersion: apps/v1
kind: Deployment
metadata:
name: "<APPLICATION_NAME>"
namespace: default
spec:
replicas: 1
selector:
matchLabels:
app: "<APPLICATION_NAME>"
template:
metadata:
labels:
app: "<APPLICATION_NAME>"
name: "<POD_NAME>"
spec:
initContainers:
- name: cws-instrumentation-init
image: public.ecr.aws/datadog/cws-instrumentation:latest
command:
- "/cws-instrumentation"
- "setup"
- "--cws-volume-mount"
- "/cws-instrumentation-volume"
volumeMounts:
- name: cws-instrumentation-volume
mountPath: "/cws-instrumentation-volume"
securityContext:
runAsUser: 0
containers:
- name: "<YOUR_APP_NAME>"
image: "<YOUR_APP_IMAGE>"
command:
- "/cws-instrumentation-volume/cws-instrumentation"
- "trace"
- "--"
- "<ENTRYPOINT>"
volumeMounts:
- name: cws-instrumentation-volume
mountPath: "/cws-instrumentation-volume"
readOnly: true
- name: datadog-agent
image: public.ecr.aws/datadog/agent:latest
env:
- name: DD_API_KEY
value: "<DD_API_KEY>"
- name: DD_RUNTIME_SECURITY_CONFIG_ENABLED
value: "true"
- name: DD_RUNTIME_SECURITY_CONFIG_EBPFLESS_ENABLED
value: "true"
- name: DD_EKS_FARGATE
value: "true"
- name: DD_CLUSTER_NAME
value: "<CLUSTER_NAME>"
- name: DD_KUBERNETES_KUBELET_NODENAME
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: spec.nodeName
volumes:
- name: cws-instrumentation-volume
serviceAccountName: datadog-agent
shareProcessNamespace: true
Verify that the Agent is sending events to Cloud Security
When you enable Cloud Security on AWS Fargate ECS or EKS, the Agent sends an agent event to Datadog to confirm that the default ruleset has been successfully deployed. To view the agent event, navigate to the Agent Events page in Datadog and search for @agent.rule_id:ruleset_loaded.
You can also verify the Agent is sending events to Cloud Security by manually triggering an AWS Fargate security signal.
In the task definition, replace the “workload” container with the following:
"name": "cws-signal-test",
"image": "ubuntu:latest",
"entryPoint": [
"/cws-instrumentation-volume/cws-instrumentation",
"trace",
"--verbose",
"--",
"/usr/bin/bash",
"-c",
"apt update;apt install -y curl; while true; do curl https://google.com; sleep 5; done"
],App and API Protection
Prerequisites
- The Datadog Agent is installed and configured for your application’s operating system or container, cloud, or virtual environment
- Datadog APM is configured for your application or service
For additional performance and reliability insights, Datadog recommends enabling Application Performance Monitoring with App and API Protection.
Installation
Software Composition Analysis (SCA)
Software Composition Analysis (SCA) works in Fargate. Follow the installation steps for applications that run in traditional hosts.
Threat Detection and Protection
For step-by-step instructions, see the following articles:
Code Security
For step-by-step instructions, see the following articles:
Cloud SIEM
Prerequisites
- Log ingestion is configured to collect logs from your sources.
Installation
For step-by-step instructions, see AWS Configuration Guide for Cloud SIEM.
Enable AWS CloudTrail logging
Enable AWS CloudTrail logging so that logs are sent to a S3 bucket. If you already have this setup, skip to Send AWS CloudTrail logs to Datadog.
- Click Create trail on the CloudTrail dashboard.
- Enter a name for your trail.
- Create a new S3 bucket or use an existing S3 bucket to store the CloudTrail logs.
- Create a new AWS KMS key or use an existing AWS KMS key, then click Next.
- Leave the event type with the default management read and write events, or choose additional event types you want to send to Datadog, then click Next.
- Review and click Create trail.
Send AWS CloudTrail logs to Datadog
Set up a trigger on your Datadog Forwarder Lambda function to send CloudTrail logs stored in the S3 bucket to Datadog for monitoring.
- Go to the Datadog Forwarder Lambda that was created during the AWS integration set up.
- Click Add trigger.
- Select S3 for the trigger.
- Select the S3 bucket you are using to collect AWS CloudTrail logs.
- For Event type, select All object create events.
- Click Add.
- See CloudTrail logs in Datadog’s Log Explorer.
See Log Explorer for more information on how to search and filter, group, and visualize your logs.
Further Reading
Additional helpful documentation, links, and articles: