- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Pull Request Comments
This product is not supported for your selected Datadog site. ().
Overview
Code Security posts comments directly on pull requests (PRs) in your source code management (SCM) system when vulnerabilities are detected on enabled repositories. This help you see and fix issues in context before merging code. The comments are diff-aware, meaning they only flag new issues introduced on lines modified in the PR.
There are two types of PR comments:
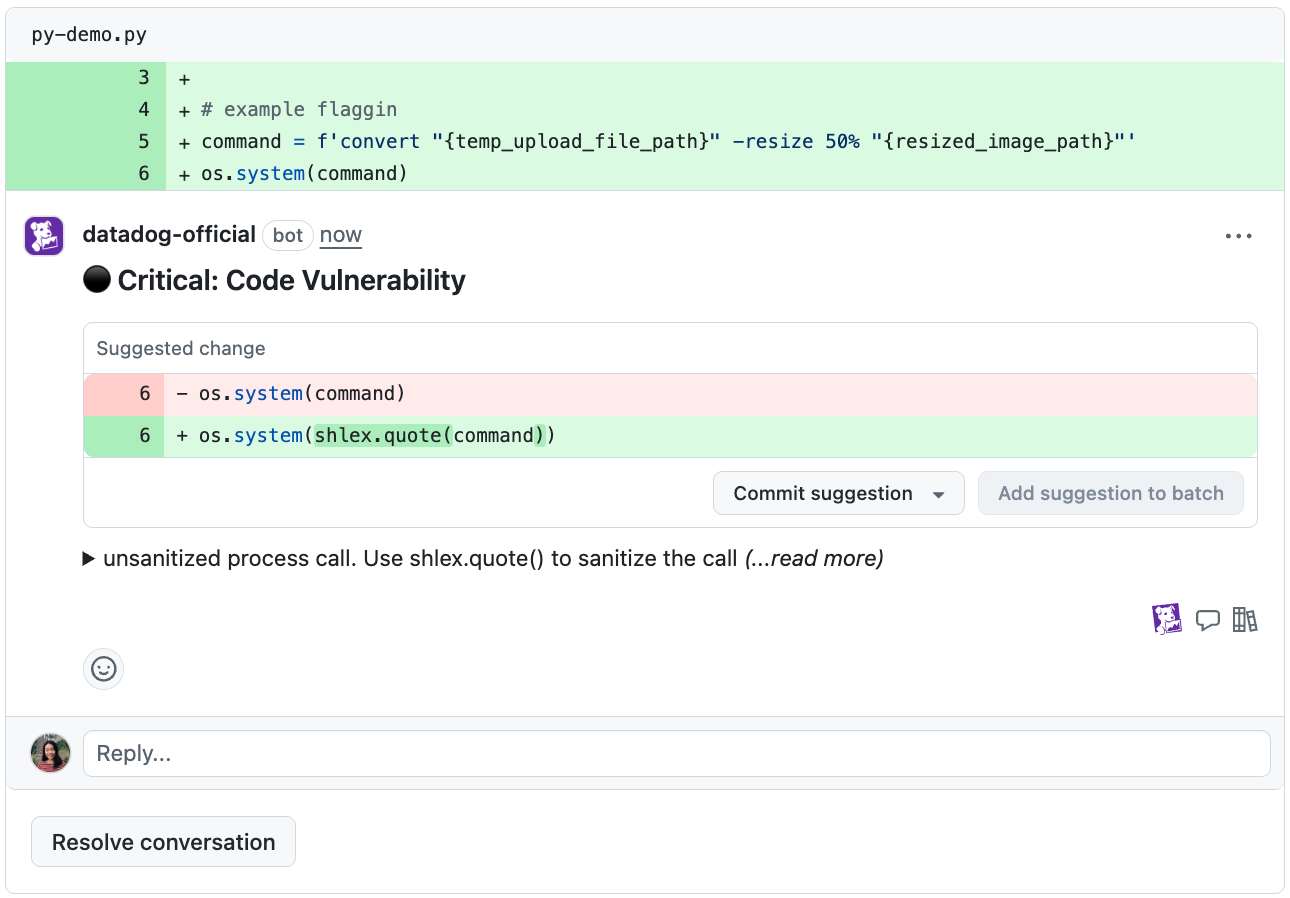
Inline comment: Flags an individual Code Security finding on specific lines of code and suggests a remediation (if available).
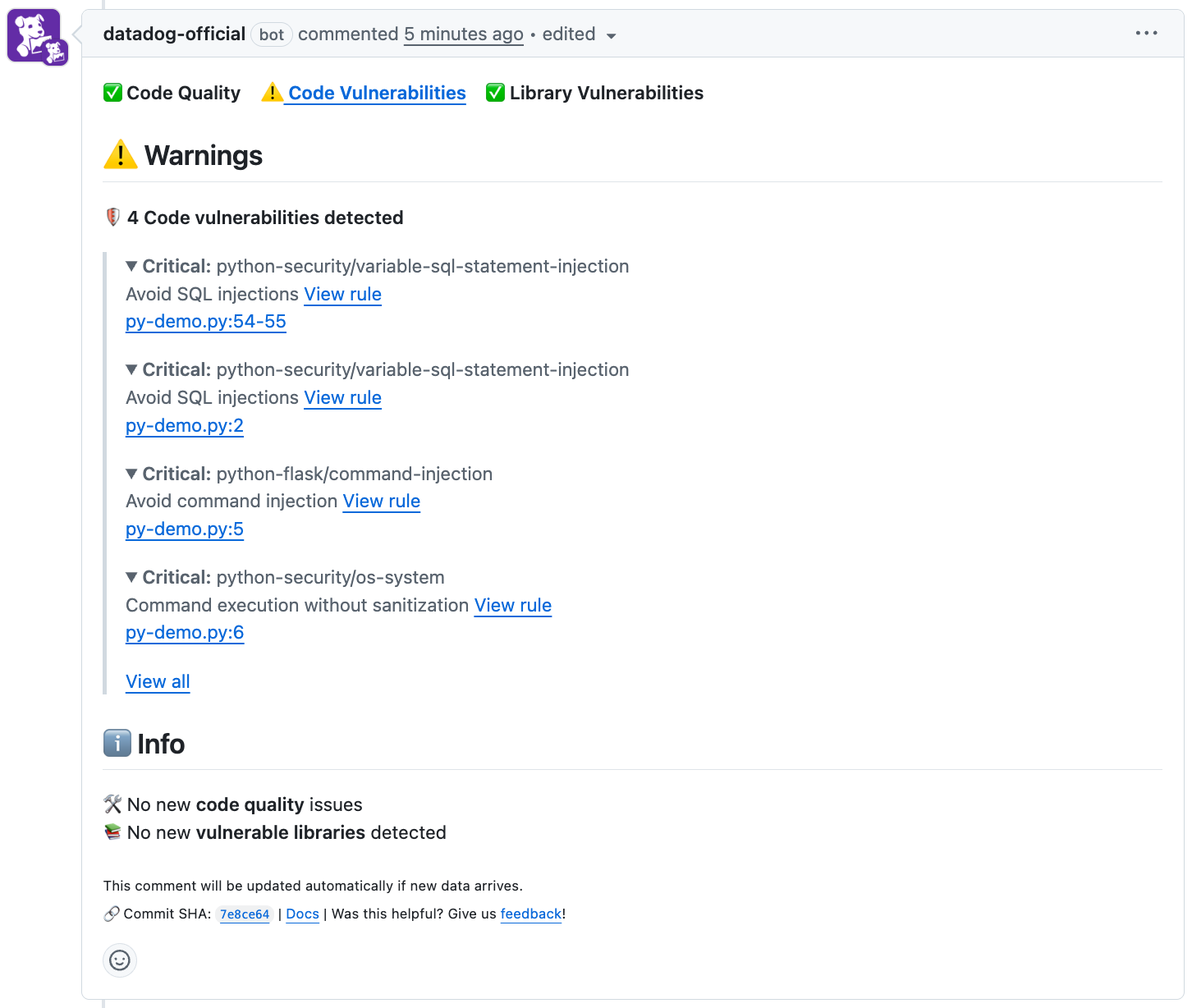
Summary comment: Combines all findings from Datadog into a single comment. This comment appears only if your PR contains issues requiring attention. After those findings are addressed, the comment is automatically edited to confirm that your PR is now clear.
You can configure PR comments at the organization or repository level in Repository Settings, with the following controls:
- Enabling/disabling PR comments by scan type (SAST, static SCA, Secrets, IaC)
- Setting severity thresholds for each scan type
- Excluding findings from test files or dev/test dependencies
Learn more about PR comments across Datadog.
Note: PR comments are not PR checks. To set up checks, see PR Gates.
Prerequisites
- You must have the Datadog source code integration for your provider enabled. PR comments are supported for GitHub, GitLab, and Azure DevOps repositories.
- Your repositories must have the relevant Code Security product(s) enabled. To enable Code Security in-app, navigate to the Code Security Settings page.
PR comments are not supported for pull requests in public repositories, or on pull requests targeting a destination branch in a different repository from the source branch (that is, forked repositories trying to merge into the main repository).
Set up pull request comments
Follow the steps below based on your source code management provider.
If you are using Datadog-hosted scanning, enable the toggle for your desired scan type (for example, Static Code Analysis (SAST)) after completing the GitHub setup steps.
If you are using GitHub Actions to run your scans, trigger the action on
push for comments to appear once the GitHub setup is complete.Connect your GitHub account(s) to Datadog
For setup instructions, read the Datadog GitHub source code integration documentation.
Create or update a GitHub App
If you already have a GitHub App connected to Datadog, update it. Otherwise, create a new GitHub App.
The permissions you grant to the GitHub App determine which GitHub integration features are available for setup.
Create and install a GitHub App
In Datadog, navigate to Integrations > GitHub Applications > Add New GitHub Application.
Fill out any required details, such as the GitHub organization name.
Under Select Features, check the Code Security: Pull Request Review Comments box.
Under Edit Permissions, verify that the Pull Requests permission is set to Read & Write.
Click Create App in GitHub.
Enter a name for your app, and submit it.
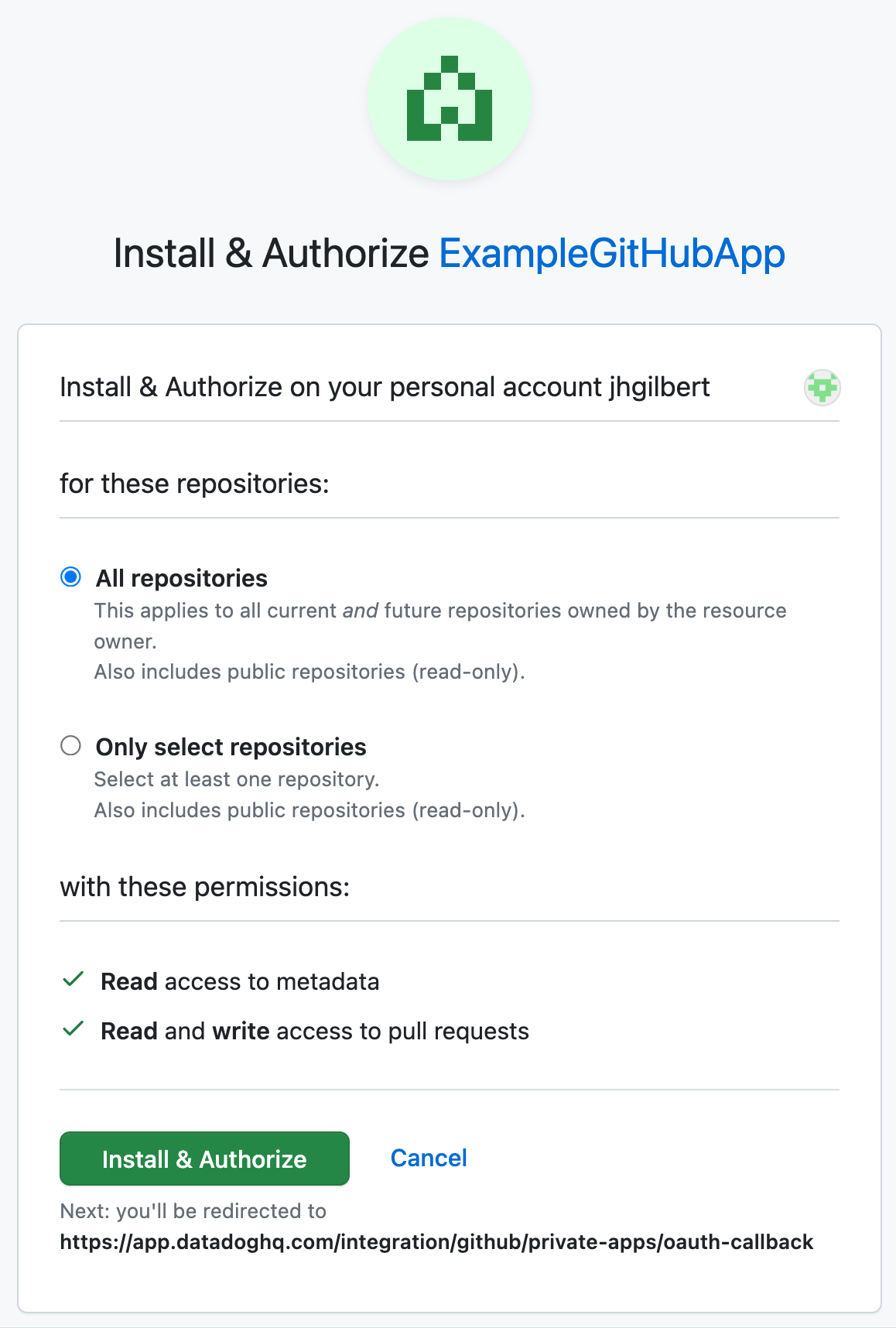
Click Install GitHub App.
Choose which repositories the app should be installed into, then click Install & Authorize.
Update an existing GitHub App
In Datadog, navigate to Integrations > GitHub Applications, and search for the GitHub App you want to use for Code Security.
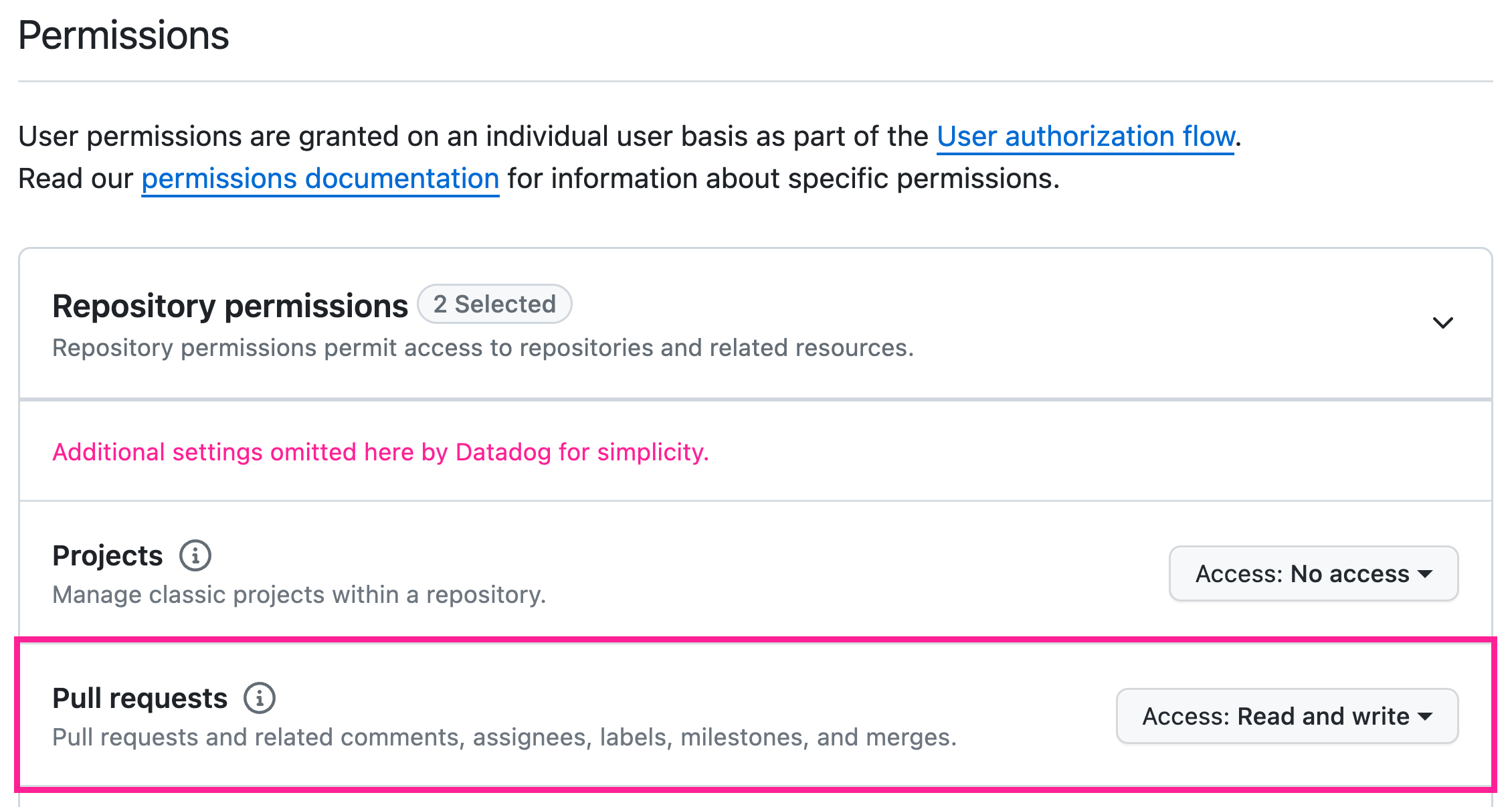
On the Features tab, look at the Code Security: Pull Request Comments section to determine whether your GitHub App needs additional permissions. If so, click Update permissions in GitHub to edit the app settings.
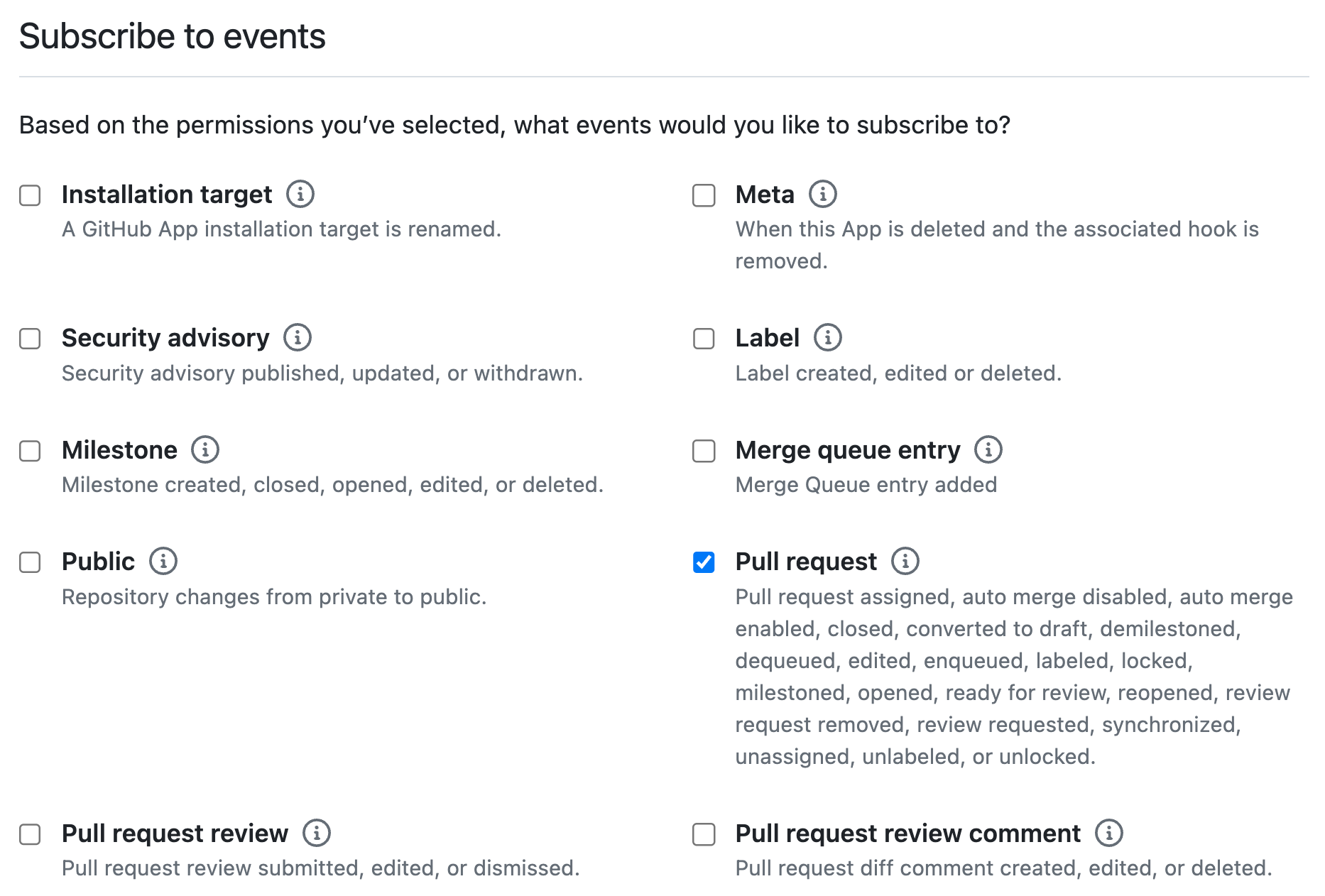
Under Repository permissions, set the Pull Requests access to Read and write.
Under the Subscribe to events heading, check the Pull request box.
See the GitLab Source Code setup instructions to connect GitLab repositories to Datadog.
See the [Azure source code setup instructions][9] to connect Azure DevOps repositories to Datadog.
Configuration options
Before enabling PR comments, ensure that at least one Code Security scan capability is enabled in the repository. Even if PR comments are configured at the organization level, they are only added in repositories where a supported scan type (for example, SAST, SCA, or IaC) is active. Repositories without any enabled scan types will not receive PR comments.
PR comments can be configured at the organization level or at the repository level:
- Organization level: Settings apply to all repositories in the organization that have at least one scan capability enabled.
- Repository level: Settings override the organization defaults for the selected repository.
When configuring PR comments, you can:
- Enable or disable comments for specific scan types (SAST, SCA, IaC).
- Set minimum severity thresholds to control when comments appear.
- Exclude comments for findings in test files or dev/test dependencies to avoid noise from low-priority issues.
Configure PR comments at the organization level
- In Datadog, navigate to Security > Code Security > Settings.
- In Repository Settings, click Global PR Comment Configuration.
- Configure the settings:
- Enable PR comments for all scan types and severities: Enable this to apply PR comments across all types and severities.
- Enable for Static Analysis (SAST): Toggle this option to enable PR comments for SAST. If enabled, specify a minimum severity threshold. Additionally, select Exclude PR comments if violations are detected in test files to prevent comments on issues found in test files.
- Enable for Software Composition Analysis (SCA): Toggle this option to enable PR comments for SCA. If enabled, specify a minimum severity threshold. Additionally, select Exclude PR comments if violations are detected in test or dev dependencies to prevent comments on issues found in dependencies existing only in development or test environments.
- Enable for Infrastructure-as-Code (IaC): Toggle this option to enable PR comments for IaC. If enabled, specify a minimum severity threshold.
- Click Save.
Configure PR comments at the repository level
- In Datadog, navigate to Security > Code Security > Settings.
- In Repository Settings, select a repository from the list.
- Configure the settings:
- Enable PR comments for all scan types and severities: Enable this to apply PR comments across all types and severities.
- Enable for Static Analysis (SAST): Toggle this option to enable PR comments for SAST. If enabled, specify a minimum severity threshold. Additionally, select Exclude PR comments if violations are detected in test files to prevent comments on issues found in test files.
- Enable for Software Composition Analysis (SCA): Toggle this option to enable PR comments for SCA. If enabled, specify a minimum severity threshold. Additionally, select Exclude PR comments if violations are detected in test or dev dependencies to prevent comments on issues found in dependencies existing only in development or test environments.
- Enable for Infrastructure-as-Code (IaC): Toggle this option to enable PR comments for IaC. If enabled, specify a minimum severity threshold.
- Block all comments in this repository: Enable this to disable all comments for this repository, overriding global settings.
- Click Save Configuration.