- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profiler
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Cloud Cost
- Application Performance
- APM
- APM Terms and Concepts
- Application Instrumentation
- APM Metrics Collection
- Trace Pipeline Configuration
- Correlate Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origins for Spans
- Service Observability
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Error Tracking
- Data Security
- Guides
- Troubleshooting
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Signals Explorer
Due to changes in how notification rules are configured, cloud configuration and infrastructure configuration signals will be deprecated in the second half of 2025.
Overview
In addition to reviewing and fixing cloud misconfigurations directly in the Misconfigurations Findings page, you can set notifications for failed misconfigurations, and configure signals to correlate and triage misconfigurations in the same place as real-time threats that are generated by Cloud SIEM and Workload Protection.
Reduce alert fatigue with security posture signals
Signals are security alerts that Datadog generates and displays in the Signals Explorer. Security posture signals trigger when Datadog generates evaluation:fail misconfigurations for a cloud or infrastructure configuration rule.
A selection of rules that have a ‘high’ or ‘critical’ severity level are enabled to generate signals by default. For lower severity compliance rules, select the Trigger a security signal toggle to begin generating signals. You can also use this toggle to disable compliance rules from generating signals at any point in time.
In order to consume misconfigurations in logical groupings and mitigate the potential for alert fatigue, you have full flexibility to change how signals are triggered for each individual resource, such as every time a resource fails a rule in a new cloud account or each time a resource is misconfigured in a service. You can also trigger by any Datadog facet. Regardless of which grouping logic you choose for signal generation, opening a signal always displays the up-to-date list of misconfigurations that are failing for this rule.
Click on any security posture signal to open a side panel for more details:
The top portion of the misconfigurations side panel displays key information about where the misconfiguration(s) are occurring: on an individual resource, a service, or an entire cloud account.
Below is the message for the rule, including a description of misconfiguration and instructions for how to remediate the issue.
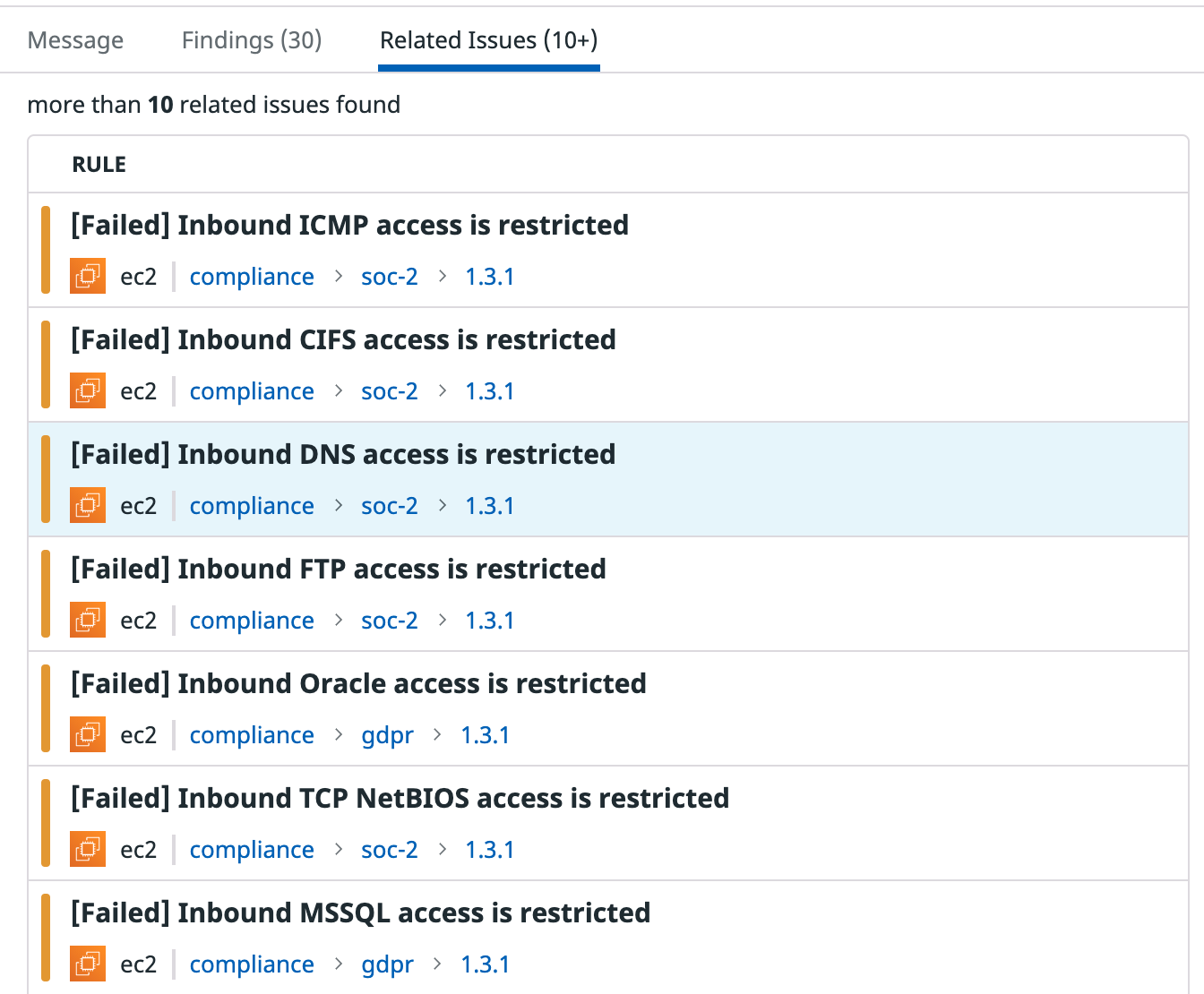
The next tab in the bottom section of the side panel displays all misconfigurations that are triggering this signal. This list always shows the current state of your infrastructure, meaning if you fixed 3 of 10 misconfigured security groups since the signal first triggered, Datadog will display 7 failed security groups rather than display misconfigurations that no longer are in violation.
Note: If using a grouping other than resource ID, the signal triggers the first time a misconfiguration meets the grouping criteria, and is not re-triggered each time a new resource in this same grouping (for example, the same service or account) fail this rule. This is done intentionally so as to avoid re-triggering signals each time a new cloud resource fails a rule. If you would like to receive an alert each time a cloud resource fails a rule, change the group by in the rule to @resource_type.
The related issues tab shows other compliance rules that have triggered signals on the same logic grouping—the same resource, service, or cloud account—and resource type (for example, security group).
At the top of the side panel, you can configure the rule or send a notification to your colleagues by email, Slack, Microsoft Teams, PagerDuty, ServiceNow, Jira, webhooks, and more.
Further reading
Additional helpful documentation, links, and articles: