- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Extend Datadog
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Setting Up ClickHouse
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Developer Integrations
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- AI Guard
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Destinations
This product is not supported for your selected Datadog site. ().
Overview
Use the Observability Pipelines Worker to send your processed logs and metrics (PREVIEW indicates an early access version of a major product or feature that you can opt into before its official release.Glossary) to different destinations. Most Observability Pipelines destinations send events in batches to the downstream integration. See Event batching for more information. Some Observability Pipelines destinations also have fields that support template syntax, so you can set these fields based on specific fields. See Template syntax for more information.
Select a destination in the left navigation menu to see more information about it.
Destinations
These are the available destinations:
- Amazon OpenSearch
- Amazon S3
- Amazon Security Lake
- Azure Storage
- Datadog CloudPrem
- CrowdStrike Next-Gen SIEM
- Datadog Logs
- Elasticsearch
- Google Cloud Storage
- Google Pub/Sub
- Google SecOps
- HTTP Client
- Kafka
- Microsoft Sentinel
- New Relic
- OpenSearch
- SentinelOne
- Socket
- Splunk HTTP Event Collector (HEC)
- Sumo Logic Hosted Collector
- Syslog
Template syntax
Logs are often stored in separate indexes based on log data, such as the service or environment the logs are coming from or another log attribute. In Observability Pipelines, you can use template syntax to route your logs to different indexes based on specific log fields.
When the Observability Pipelines Worker cannot resolve the field with the template syntax, the Worker defaults to a specified behavior for that destination. For example, if you are using the template {{application_id}} for the Amazon S3 destination’s Prefix field, but there isn’t an application_id field in the log, the Worker creates a folder called OP_UNRESOLVED_TEMPLATE_LOGS/ and publishes the logs there.
The following table lists the destinations and fields that support template syntax, and what happens when the Worker cannot resolve the field:
| Destination | Fields that support template syntax | Behavior when the field cannot be resolved |
|---|---|---|
| Amazon Opensearch | Index | The Worker writes logs to the datadog-op index. |
| Amazon S3 | Prefix | The Worker creates a folder named OP_UNRESOLVED_TEMPLATE_LOGS/ and writes the logs there. |
| Azure Blob | Prefix | The Worker creates a folder named OP_UNRESOLVED_TEMPLATE_LOGS/ and writes the logs there. |
| Elasticsearch | Index | The Worker writes logs to the datadog-op index. |
| Google Chronicle | Log type | Defaults to DATADOG log type. |
| Google Cloud | Prefix | The Worker creates a folder named OP_UNRESOLVED_TEMPLATE_LOGS/ and writes the logs there. |
| Opensearch | Index | The Worker writes logs to the datadog-op index. |
| Splunk HEC | Index Source type | The Worker sends the logs to the default index configured in Splunk. The Worker defaults to the httpevent sourcetype. |
Example
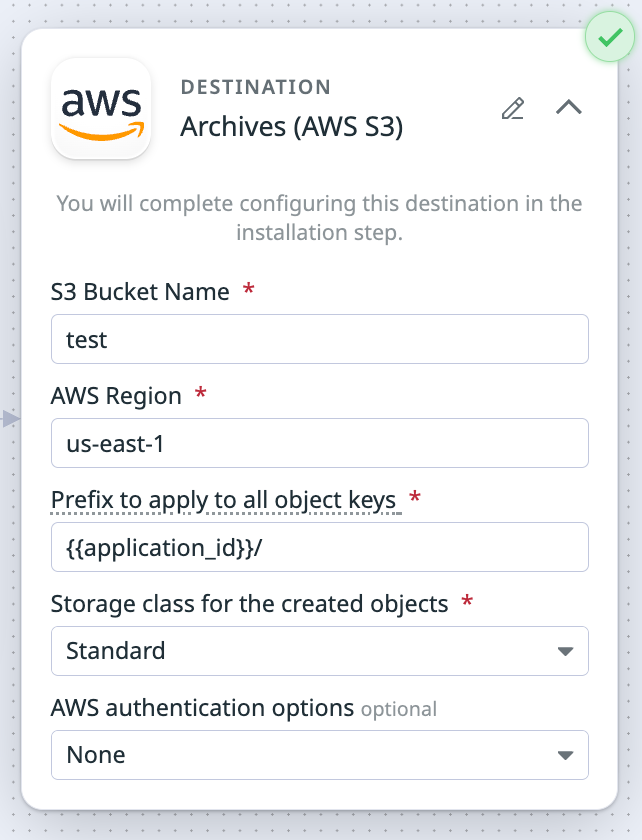
If you want to route logs based on the log’s application ID field (for example, application_id) to the Amazon S3 destination, use the event fields syntax in the Prefix to apply to all object keys field.
Syntax
Event fields
Use {{ <field_name> }} to access individual log event fields. For example:
{{ application_id }}
Strftime specifiers
Use strftime specifiers for the date and time. For example:
year=%Y/month=%m/day=%d
Escape characters
Prefix a character with \ to escape the character. This example escapes the event field syntax:
\{{ field_name }}
This example escapes the strftime specifiers:
year=\%Y/month=\%m/day=\%d/
Event batching
Observability Pipelines destinations send events in batches to the downstream integration. A batch of events is flushed when one of the following parameters is met:
- Maximum number of events
- Maximum number of bytes
- Timeout (seconds)
For example, if a destination’s parameters are:
- Maximum number of events = 2
- Maximum number of bytes = 100,000
- Timeout (seconds) = 5
And the destination receives 1 event in a 5-second window, it flushes the batch at the 5-second timeout.
If the destination receives 3 events within 2 seconds, it flushes a batch with 2 events and then flushes a second batch with the remaining event after 5 seconds. If the destination receives 1 event that is more than 100,000 bytes, it flushes this batch with the 1 event.
| Destination | Maximum Events | Maximum Bytes | Timeout (seconds) |
|---|---|---|---|
| Amazon OpenSearch | None | 10,000,000 | 1 |
| Amazon S3 (Datadog Log Archives) | None | 100,000,000 | 900 |
| Amazon Security Lake | None | 256,000,000 | 300 |
| Azure Storage (Datadog Log Archives) | None | 100,000,000 | 900 |
| CrowdStrike | None | 1,000,000 | 1 |
| Datadog Logs | 1,000 | 4,250,000 | 5 |
| Elasticsearch | None | 10,000,000 | 1 |
| Google Chronicle | None | 1,000,000 | 15 |
| Google Cloud Storage (Datadog Log Archives) | None | 100,000,000 | 900 |
| HTTP Client | 1000 | 1,000,000 | 1 |
| Microsoft Sentinel | None | 10,000,000 | 1 |
| New Relic | 100 | 1,000,000 | 1 |
| OpenSearch | None | 10,000,000 | 1 |
| SentinelOne | None | 1,000,000 | 1 |
| Socket* | N/A | N/A | N/A |
| Splunk HTTP Event Collector (HEC) | None | 1,000,000 | 1 |
| Sumo Logic Hosted Collecter | None | 10,000,000 | 1 |
| Syslog* | N/A | N/A | N/A |
*Destination does not batch events.