- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
抑制
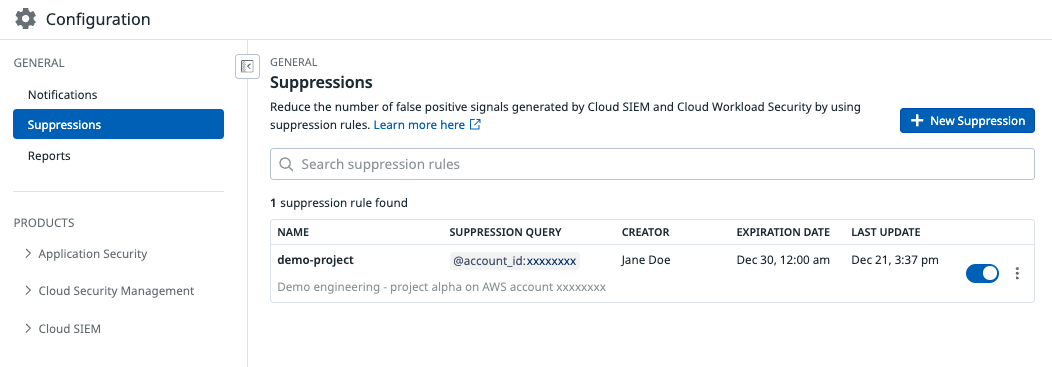
概要
抑制とは、シグナルを生成しない条件を明確に定めるもので、生成されるシグナルの精度と関連性の向上に寄与します。
抑制の設定方法
個別の検出ルール内に抑制クエリを設定することも、1 つ以上の検出ルールにまたがってシグナルを抑制するための抑制ルールを別途定義することもできます。
検出ルール
検出ルールを作成または変更する際に、抑制クエリを定義してシグナルの生成を防ぐことができます。たとえば、検出ルールがセキュリティ シグナルをトリガーする条件を決めるために、ルール クエリを追加できます。また、抑制クエリをカスタマイズして、特定の属性値に一致するシグナルを抑制することもできます。
抑制ルール
抑制ルールを使用すると、各検出ルールごとに個別の抑制条件を設定する代わりに、複数の検出ルールに共通の抑制条件を設定できます。たとえば、特定の IP を含むシグナルをすべて抑制する抑制ルールを設定できます。
抑制の設定
抑制リスト
抑制リストを使うと、複数の検出ルールにまたがる抑制を一元的かつ体系的に管理できます。
抑制ルールを作成
- Suppressions ページに移動します。
- + New Suppression をクリックします。
- 抑制クエリの名前を入力します。
- なぜこの抑制が適用されるのか、その背景を示す説明を追加します。
- 任意で、この抑制を無効化する有効期限日を設定します。
- この抑制を適用する検出ルールを選択します。複数の検出ルールを選択できます。
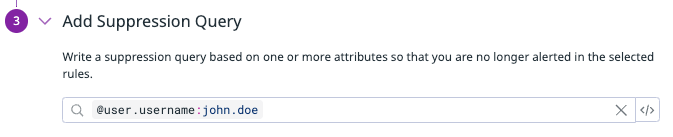
- Add Suppression Query セクションでは、抑制クエリを入力でき、条件に一致した場合にシグナルが生成されないようにできます。たとえば、ユーザー
john.doeがシグナルをトリガーしているものの、その行動が無害でこのユーザーからのシグナルを今後抑制したい場合は、ログ クエリ@user.username:john.doeを入力します。抑制ルールのクエリは、シグナル属性に基づいています。 - さらに、ログを分析対象から除外するための除外クエリを追加できます。 これらのクエリは、ログ属性に基づきます。注: 抑制は、以前はログ除外クエリに基づいていましたが、今後は抑制ルールの Add a suppression query ステップに含まれるようになりました。
編集権限の制限
By default, all users have view and edit access to suppressions. To use granular access controls to limit the roles that may edit a suppression rule:
- Click the vertical three-dot menu for the rule and select Permissions.
- Click Restrict Access. The dialog box updates to show that members of your organization have Viewer access by default. Use that dropdown menu to select one or more roles, teams, or users that may edit the suppression rule.
- Click Add.
- Click Save.
Note: To maintain your edit access to the rule, Datadog requires you to include at least one role that you are a member of before saving.
To restore access to a rule:
- Click the vertical three-dot menu for the rule and select Permissions.
- Click Restore Full Access.
- Click Save.
参考資料
お役に立つドキュメント、リンクや記事: