- 重要な情報
- はじめに
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- Administrator's Guide
- API
- Partners
- DDSQL Reference
- モバイルアプリケーション
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- アプリ内
- ダッシュボード
- ノートブック
- DDSQL Editor
- Reference Tables
- Sheets
- Watchdog
- アラート設定
- メトリクス
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- インフラストラクチャー
- Cloudcraft
- Resource Catalog
- ユニバーサル サービス モニタリング
- Hosts
- コンテナ
- Processes
- サーバーレス
- ネットワークモニタリング
- Cloud Cost
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM & セッションリプレイ
- Synthetic モニタリング
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- Code Security
- クラウド セキュリティ マネジメント
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- CloudPrem
- 管理
OCI Configuration Guide for Cloud SIEM
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
Overview
Cloud SIEM applies detection rules to all processed logs in Datadog to detect threats such as targeted attacks, communication with threat intel-listed IPs, or insecure resource modifications. Detected threats are surfaced as Security Signals in the Security Signals Explorer for triage.
This guide walks you through the following steps to start detecting threats with your OCI Audit logs:
Set up Datadog’s OCI integration
Set up Datadog’s OCI integration using either the QuickStart (recommended) or the Terraform method.
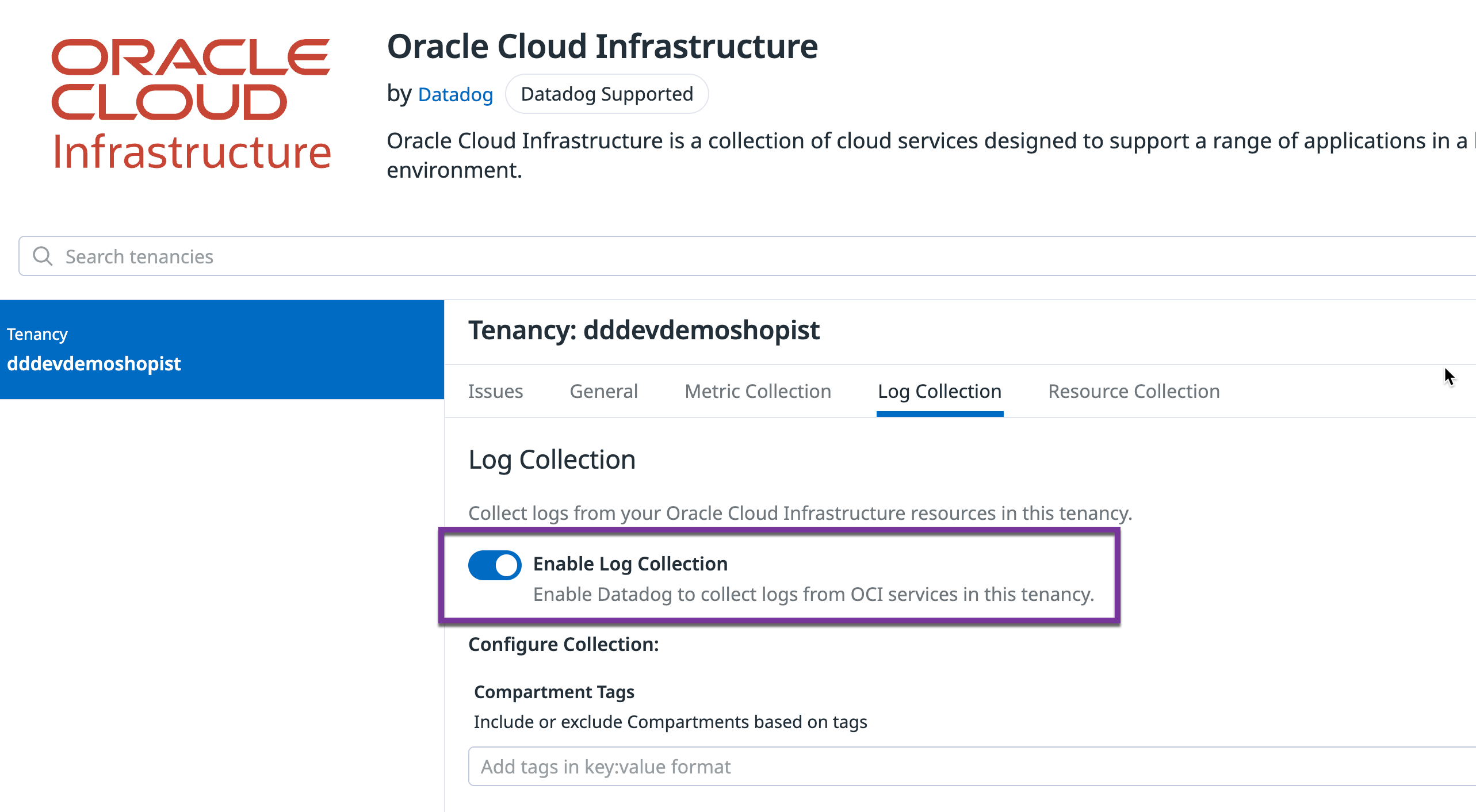
Enable log collection
Ensure that log collection is enabled in the Datadog OCI integration tile:
Use Cloud SIEM to triage Security Signals
Cloud SIEM applies out-of-the-box detection rules to all processed logs, including your OCI Audit logs. When a threat is detected with a detection rule, a Security Signal is generated and can be viewed in the Security Signals Explorer.
- Go to the Cloud SIEM Signals Explorer to view and triage threats. See Investigate Security Signals for further details.
- See out-of-the-box detection rules that are applied to your logs.
- Create rules to detect threats that match your specific use case.