- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- AI Guard
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Microsoft Sysmon
Supported OS
Integration version1.2.0
Microsoft Sysmon - Overview 1
Microsoft Sysmon - Overview 2
Microsoft Sysmon - Overview 3
Microsoft Sysmon - Overview 4
Microsoft Sysmon - Overview 5
Microsoft Sysmon - Overview 6
Microsoft Sysmon - Overview 7
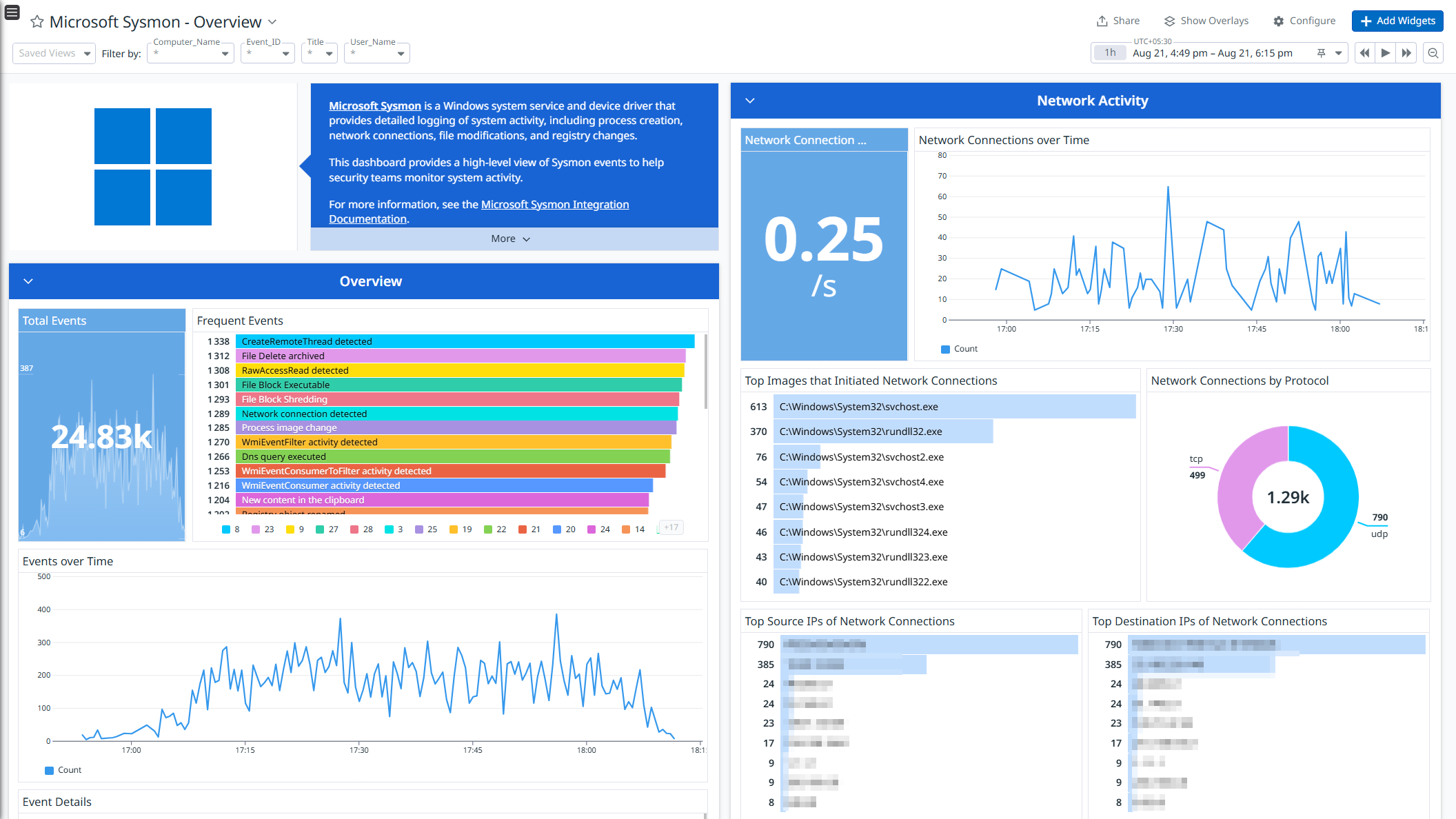
Overview
Microsoft Sysmon is a Windows system service and device driver that provides detailed logging of system activity, including process creation, network connections, file modifications, and registry changes.
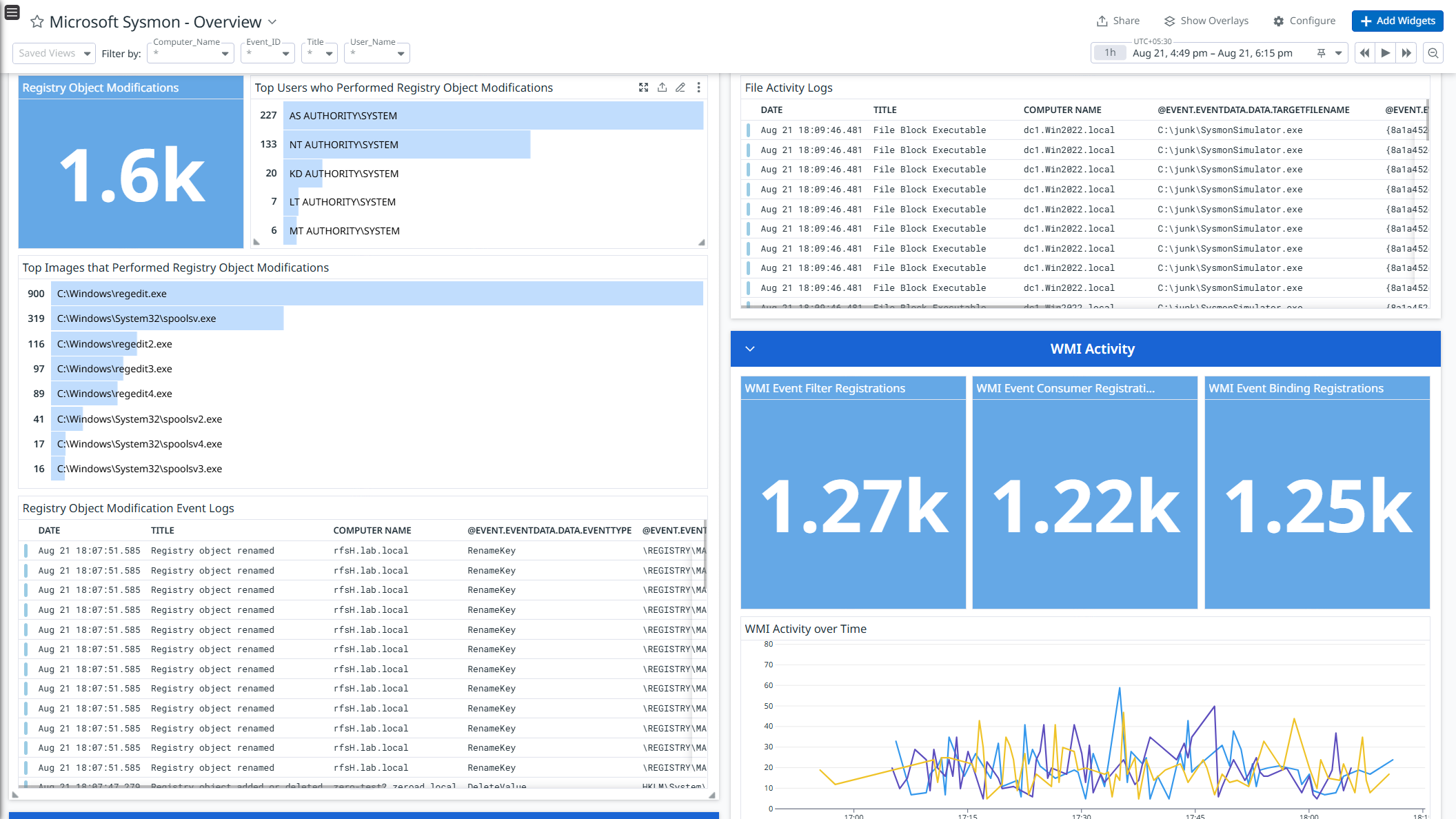
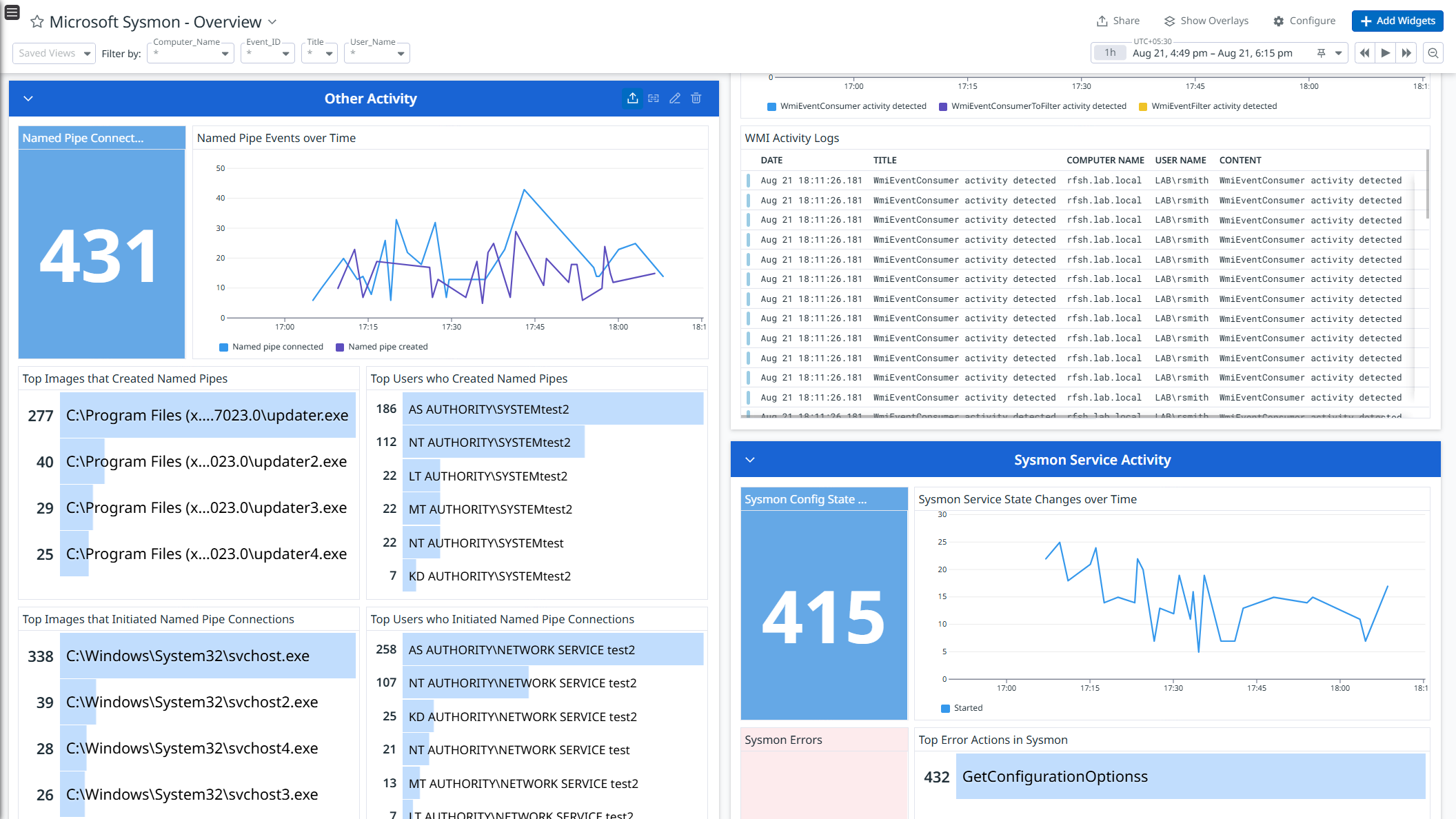
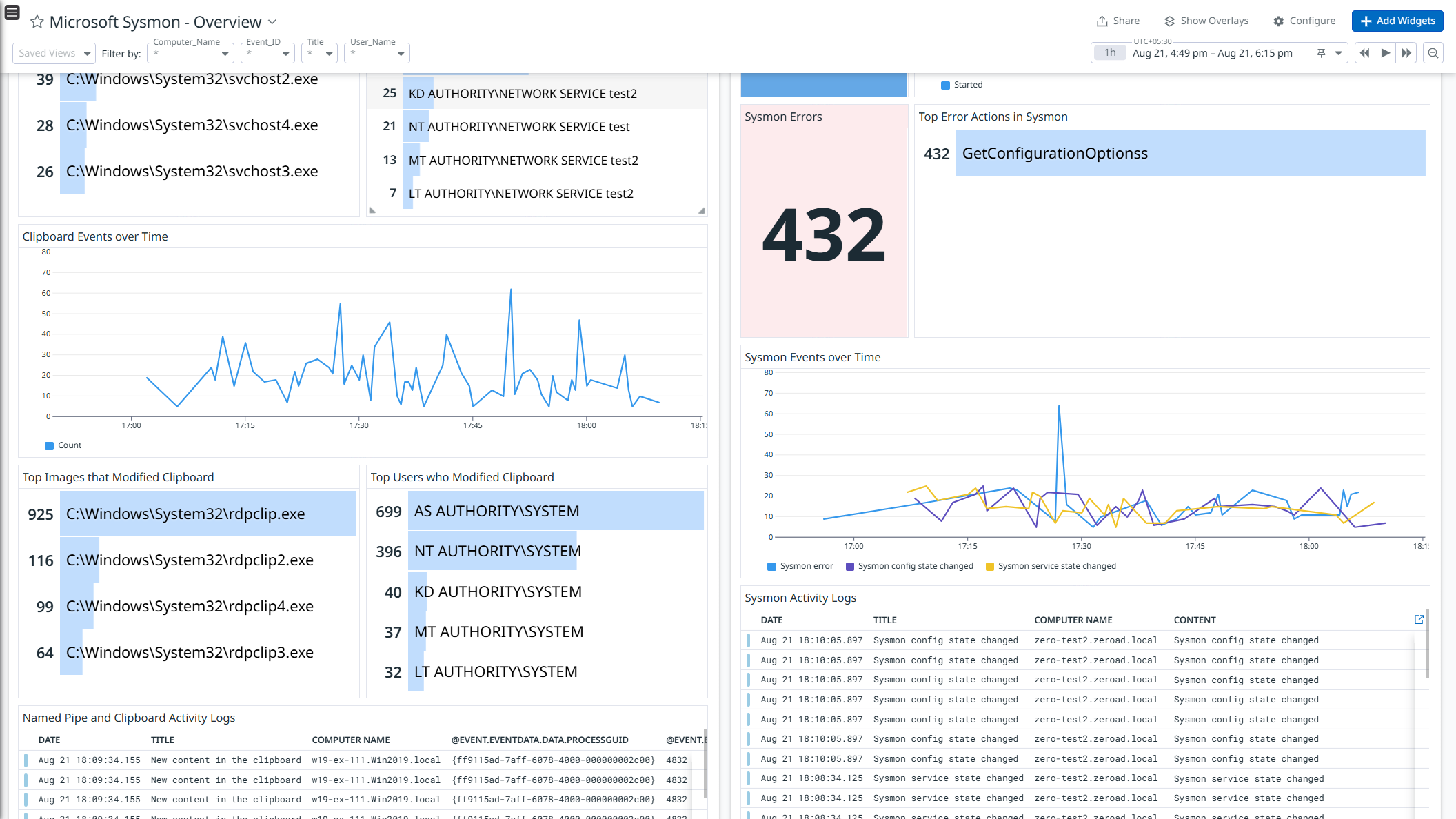
This integration enriches and ingests the Sysmon event logs. Use the pre-built dashboard to get a high-level view of the Sysmon events helping security teams monitor system activity.
Minimum Agent version: 7.67.0
Setup
Installation
To install the Microsoft Sysmon integration, run the following Agent installation command and the steps below. For more information, see the Integration Management documentation.
Note: This step is not necessary for Agent version >= 7.66.0.
Run powershell.exe as admin and execute the following command:
& "$env:ProgramFiles\Datadog\Datadog Agent\bin\agent.exe" integration install datadog-microsoft_sysmon==1.0.0
Configuration
Configure Log Collection
Collecting logs is disabled by default in the Datadog Agent. Enable it in the
datadog.yamlfile with:logs_enabled: trueAdd this configuration block to your
microsoft_sysmon.d/conf.yamlfile to start collecting your Microsoft Sysmon logs:logs: - type: windows_event channel_path: "Microsoft-Windows-Sysmon/Operational" source: microsoft-sysmon service: microsoft-sysmon sourcecategory: windowsevent
See the sample microsoft_sysmon.d/conf.yaml for available configuration options.
Configure Sysmon
Follow these steps to install Sysmon:
Download the zip file from the Sysmon download page. Extract its zip file content.
Create an XML file for configuring Sysmon. For example, if you want to monitor processes created by apps from AppData folders, the configuration file will look like content shown below. You can add more event filters under the
EventFilteringXML tag for other events in the same way.<Sysmon schemaversion="4.90"> <HashAlgorithms>md5,sha256</HashAlgorithms> <CheckRevocation/> <EventFiltering> <ProcessCreate onmatch="include"> <Image condition="contains">C:\Users\*\AppData\Local\Temp\</Image> <Image condition="contains">C:\Users\*\AppData\Roaming\</Image> </ProcessCreate> </EventFiltering> </Sysmon>Note: Sysmon is highly configurable using the XML configuration file, which allows you to:
- Control which events to monitor
- Filter events based on processes, paths, etc.
Enabling too many Sysmon event types can lead to excessive data ingestion. Community resources such as sysmon-modular and the SwiftOnSecurity Sysmon config provide recommended configurations, including examples of event inclusions and exclusions. These are intended as a starting point, and you can refer to them when tuning your own configuration.
Run the following command as admin from the extracted folder:
.\Sysmon -i [<configfile>]
For more details, please refer to the Sysmon docs.
Validation
Run the Agent’s status subcommand and look for microsoft_sysmon under the Checks section.
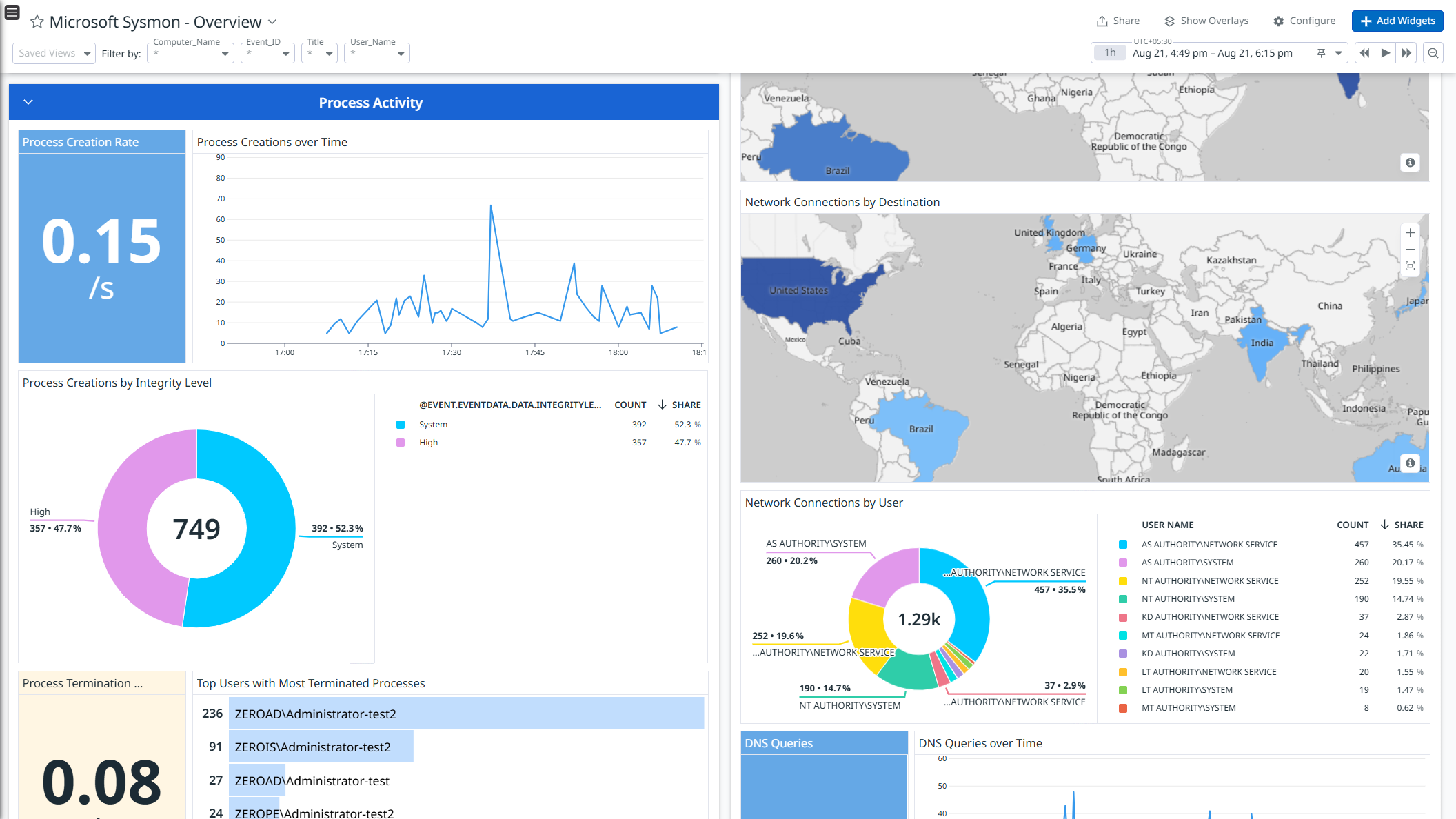
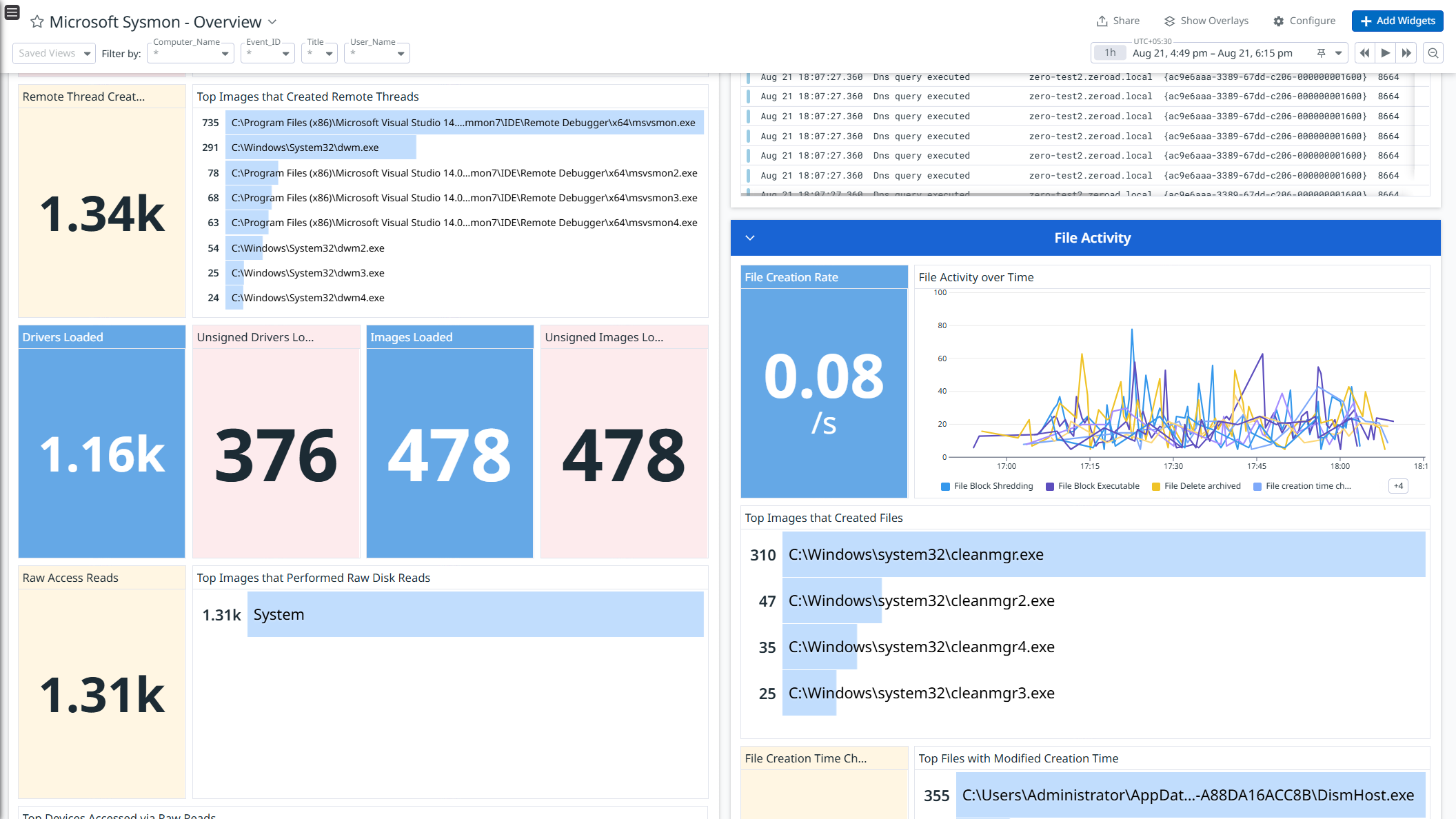
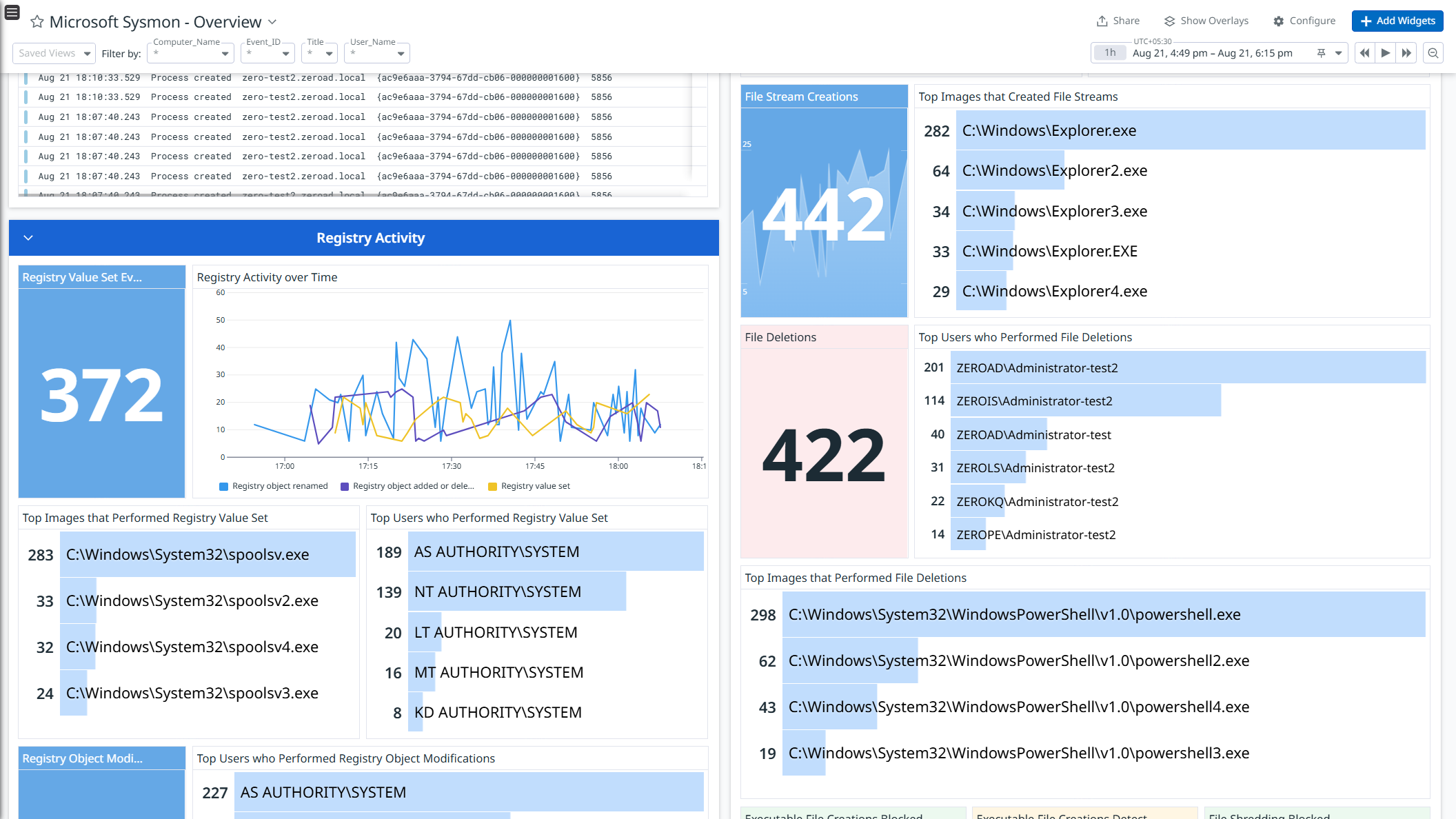
Data Collected
Logs
The Microsoft Sysmon integration collects the following Sysmon event logs:
- Process activity logs
- Network activity logs
- File activity logs
- Registry activity logs
- WMI activity logs
- Sysmon service activity logs
- Named Pipe and Clipboard activity logs
Metrics
The Microsoft Sysmon integration does not include any metrics.
Events
The Microsoft Sysmon integration does not include any events.
Service Checks
The Microsoft Sysmon integration does not include any service checks.
Support
Need help? Contact Datadog support.
