- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- AI Guard
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Juniper SRX Firewall
Supported OS
Integration version1.2.0



Juniper SRX Firewall - Overview
Juniper SRX Firewall - Session Logs
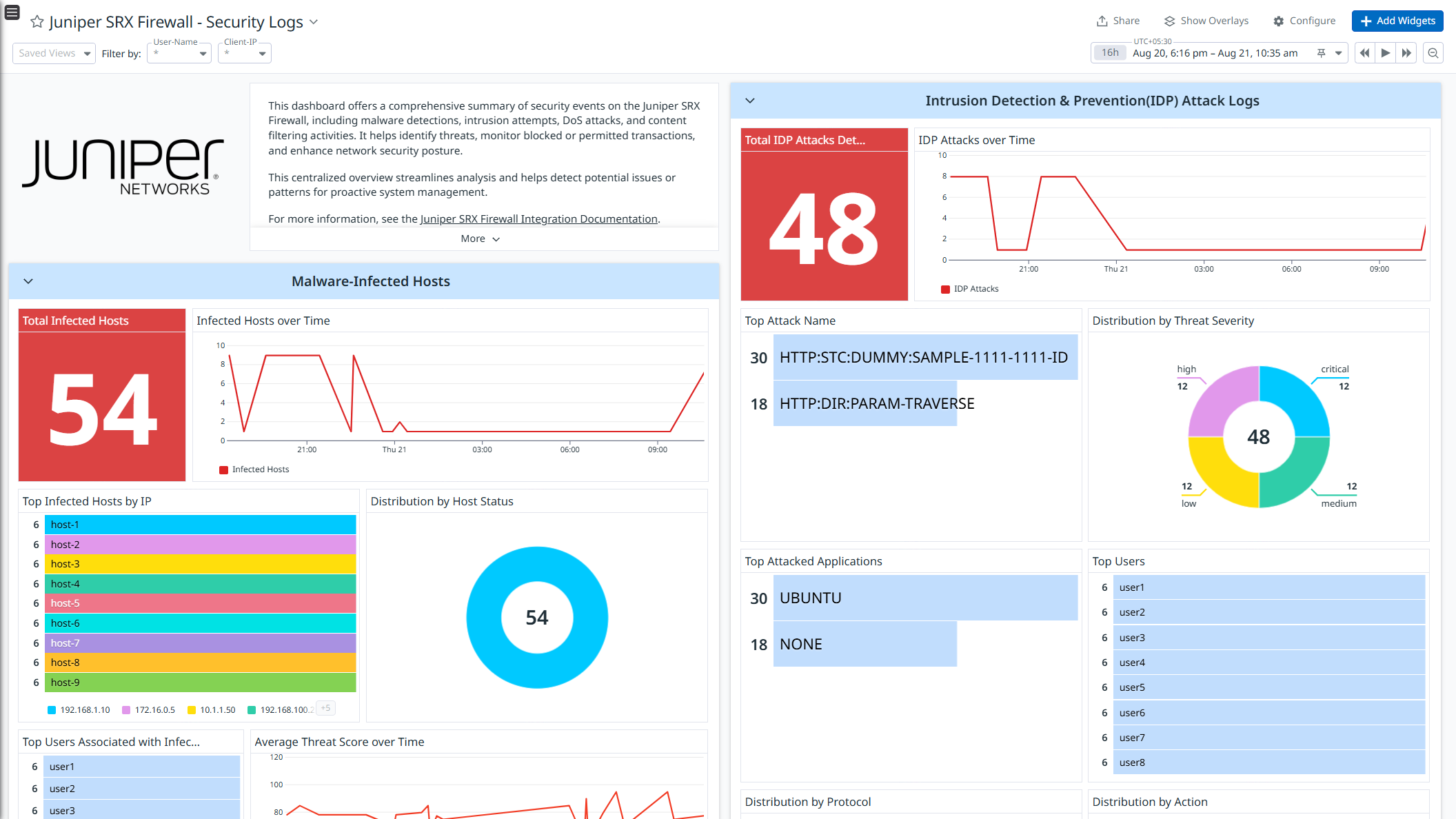
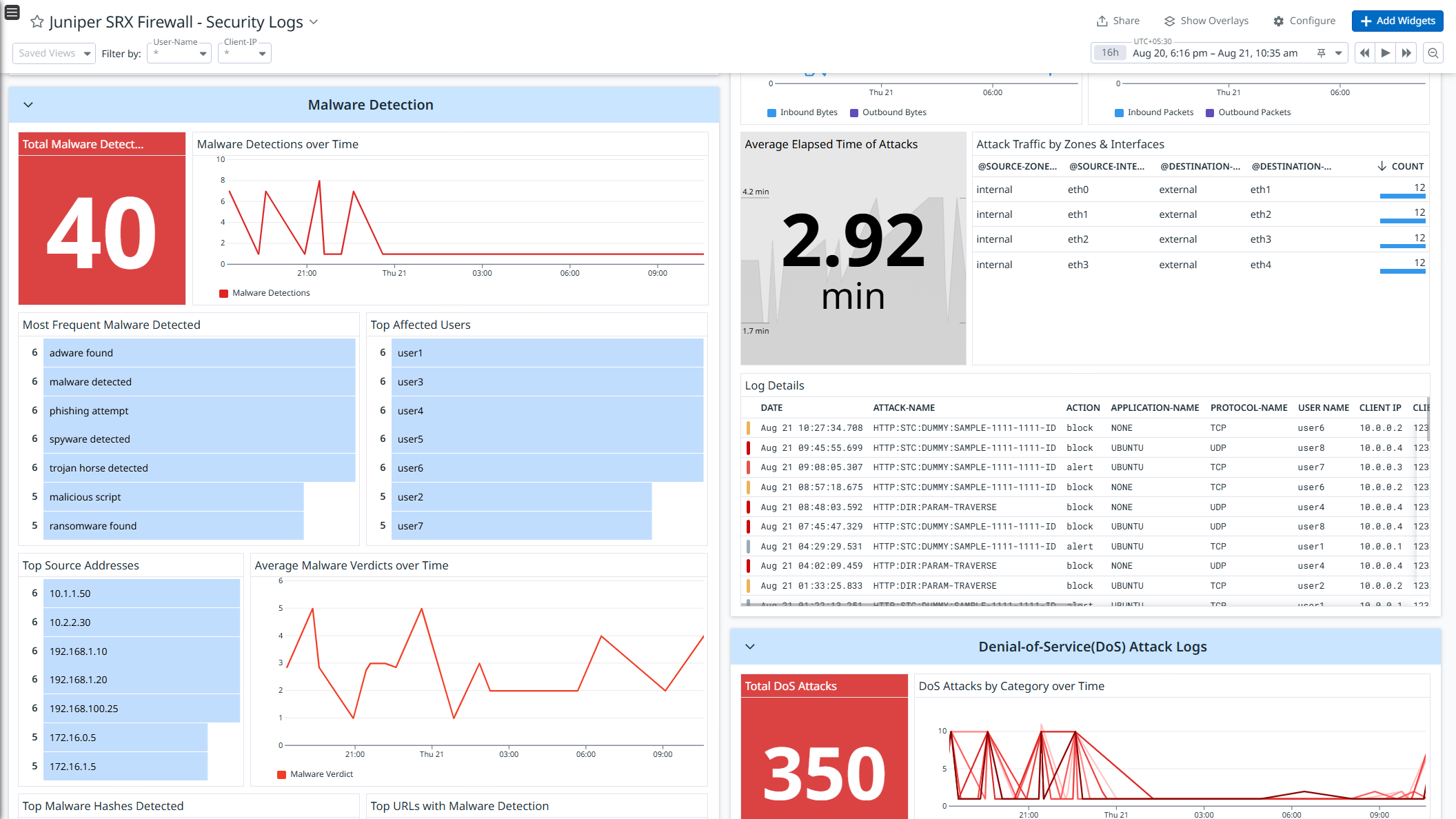
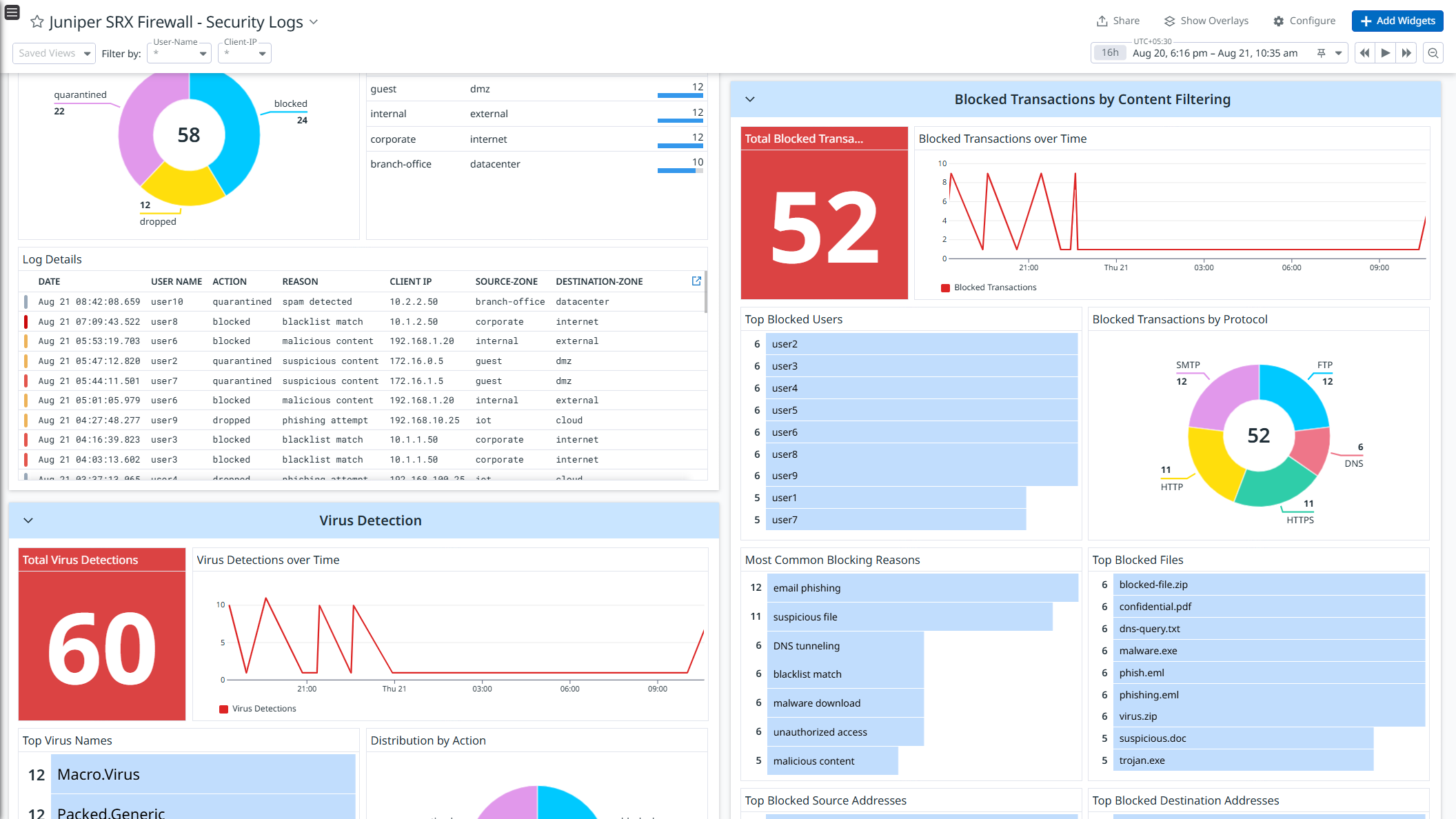
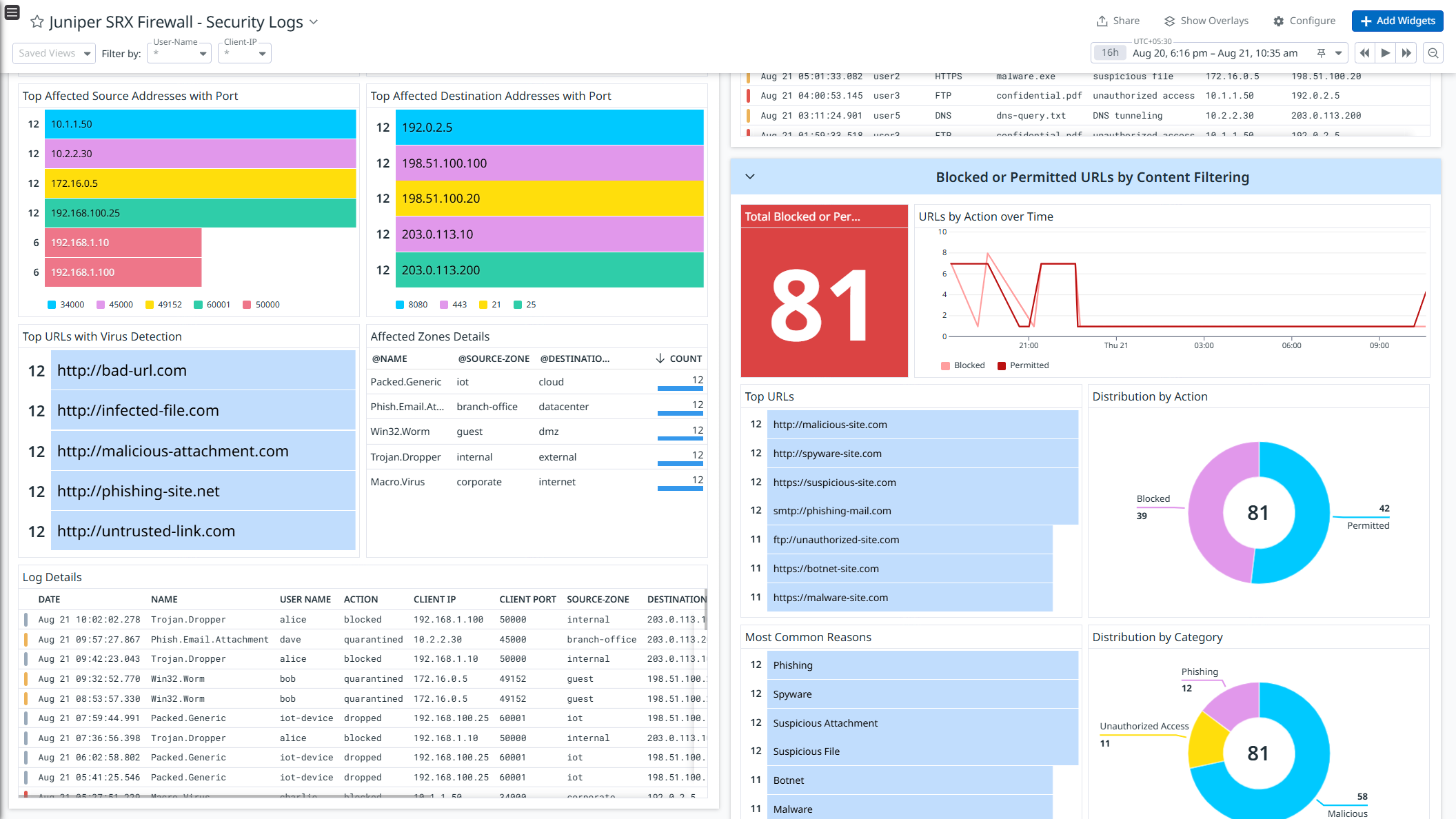
Juniper SRX Firewall - Security Logs
Juniper SRX Firewall - Security Logs
Juniper SRX Firewall - Security Logs
Juniper SRX Firewall - Security Logs
Juniper SRX Firewall - Authentication Logs
Overview
Juniper SRX Firewall secures your network edge, data center, and cloud applications by detecting and mitigating intrusions, malware, and other threats.
This integration parses the following log types:
- Session Logs: Track network traffic and session activities, including initiated and denied sessions, application-related traffic, and dropped packets.
- Security Logs: Monitor security events such as malware detections, intrusion attempts, DoS attacks, and content filtering activities.
- Authentication Logs: Capture authentication activities, including successful and failed login attempts.
Get detailed visibility into these logs with out-of-the-box dashboards, and strengthen security with prebuilt Cloud SIEM detection rules for proactive threat monitoring and response.
Minimum Agent version: 7.67.0
Setup
Installation
To install the Juniper SRX Firewall integration, run the following Agent installation command in your terminal. For more information, see the Integration Management documentation.
Note: This step is not necessary for Agent version >= 7.64.0.
sudo -u dd-agent -- datadog-agent integration install datadog-juniper_srx_firewall==1.0.0
Configuration
Configure log collection
Log collection is disabled by default in the Datadog Agent. Enable it in
datadog.yaml:logs_enabled: trueAdd the following configuration block to your
juniper_srx_firewall.d/conf.yamlfile to start collecting logs. See the sampleconf.yamlfor available configuration options.logs: - type: udp port: <PORT> source: juniper-srx-firewall service: juniper-srx-firewallNote:
PORT: Specify the UDP port that Datadog will listen on (default: 514).- Do not change the
serviceandsourcevalues, as they are integral to proper log pipeline processing.
Configure syslog message forwarding from Juniper SRX Firewall
Log in to the Juniper SRX Firewall CLI.
Enter configuration mode:
configureTo send logs to the Datadog Agent, execute the following commands:
set system syslog host <IP-ADDRESS> any any set system syslog host <IP-ADDRESS> port <PORT> set system syslog host <IP-ADDRESS> structured-data briefNote:
- Replace
<IP-ADDRESS>with the Datadog Agent’s IP address. - Replace
<PORT>with the same port configured in Log Collection.
- Replace
Verify if
Security Loggingis enabled:show security log modeIf enabled, the output will display either
mode stream;ormode event-stream;If
Security Loggingis enabled, configure log streaming:set security log stream <NAME> format sd-syslog set security log stream <NAME> category all set security log stream <NAME> host <IP-ADDRESS> set security log stream <NAME> host port <PORT> set security log transport protocol udpApply and exit the configuration:
commit exit
Validation
Run the Agent’s status subcommand and look for juniper_srx_firewall under the Checks section.
Data Collected
Log
| Format | Event Types |
|---|---|
| Structured-Data(RFC 5424) | Session Logs, Security Logs, Authentication Logs |
Metrics
The Juniper SRX Firewall integration does not include any metrics.
Events
The Juniper SRX Firewall integration does not include any events.
Service Checks
The Juniper SRX Firewall integration does not include any service checks.
Troubleshooting
Permission denied while port binding
If you see a Permission denied error while port binding in the Agent logs:
Binding to a port number under 1024 requires elevated permissions. Grant access to the port using the
setcapcommand:sudo setcap CAP_NET_BIND_SERVICE=+ep /opt/datadog-agent/bin/agent/agentVerify the setup is correct by running the
getcapcommand:sudo getcap /opt/datadog-agent/bin/agent/agentWith the expected output:
/opt/datadog-agent/bin/agent/agent = cap_net_bind_service+epNote: Re-run this
setcapcommand every time you upgrade the Agent.
Data is not being collected
Ensure firewall settings allow traffic through the configured port.
Port already in use
On systems running Syslog, the Agent may fail to bind to port 514 and display the following error:
Can't start UDP forwarder on port 514: listen udp :514: bind: address already in use
This error occurs because Syslog uses port 514 by default.
To resolve:
- Disable Syslog, OR
- Configure the Agent to listen on a different, available port.
For further assistance, contact Datadog support.
