- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- AI Guard
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Getting Started with Azure
Overview
Datadog offers multiple configuration options for the Azure integration. This guide provides an overview of the various options available for getting started with Azure, with links to Azure resources and tutorials that address specific use cases.
Prerequisites
If you haven’t already, create a Datadog account.
Permissions required for integration setup
Permissions required for integration setup
In Azure
Your Microsoft Entra ID user needs the following permissions:
Permission to create an app registration
One of the following must be true for the user:
Users can register applicationshas been set toYes- The user has the Application Developer role
Admin roles within your subscriptions
Within the subscriptions you wish to monitor, you must have either:
- The Owner role
- Both the Contributor and User Access Admin roles
Permission to add and grant consent for Graph API permissions
The Privileged Role Administrator role contains the required permissions.
In Datadog
The Datadog Admin Role, or any other role with the azure_configurations_manage permission.
Cloud Cost Management and Log Archives require the app registration setup method. For Datadog accounts using the Azure Native integration, follow the setup steps on this page to create an app registration. If a subscription is connected through both methods, a redundancy warning appears in the Azure integration tile. This warning can be safely ignored for Cloud Cost Management and Log Archives.
Setup
Follow the instructions on this page to set up the Azure integration through an app registration, available for all Datadog sites.
Quickstart (recommended)
Quickstart (recommended)
Choose the Quickstart setup method if…
- You are setting up Datadog for the first time.
- You prefer a UI-based workflow and want to minimize the time it takes to create a service principal with the required monitoring permissions.
- You want to automate setup steps in scripts or CI/CD pipelines.
Instructions
- In the Azure integration tile, click + Add New App registration, then select Quickstart.
- Copy the setup script, and run it in the Azure Cloud shell.
- Return to the Datadog UI. You should see CONNECTED at the top right corner of the setup script.
- Select the subscriptions and management groups to collect data from.
- Optionally, click the metric collection toggle to disable all metric collection from Azure. You can also expand the Advanced Configuration dropdown to filter metrics by:
- Resource provider
- Tags
- Hosts
- App Service Plans
- Container Apps
You can also click to enable custom metric collection from Azure Application Insights, and disable the collection of usage metrics.
Optionally, click the resource collection toggle to disable the collection of configuration information from your Azure resources.
Enable log collection to set up and configure the services and diagnostic settings needed to forward logs to Datadog:
- If a log forwarder already exists in the tenant, it is modified to extend its scope. Any changed settings apply to existing as well as newly-selected subscriptions or management groups.
- If you’re creating a new log forwarder:
- Enter a resource group name to store the log forwarder control plane
- Select a control plane subscription for the log-forwarding orchestration (LFO).
- Select a region for the control plane.
Note: The resource group name, control plane subscription, and region fields only appear when creating a new log forwarder.
- Optionally, open Log filtering options to filter logs by tags, or apply filtering for specific information (such as PII) using regex.
See the Architecture section of the automated log forwarding guide for more information about this architecture.
Click Confirm to finish the setup.
Terraform
Terraform
Choose the Terraform setup method if…
- You manage infrastructure as code and want to keep the Datadog Azure integration under version control.
- You need to configure multiple tenants or subscriptions consistently with reusable provider blocks.
- You want a repeatable, auditable deployment process that fits into your Terraform-managed environment.
Instructions
Follow these steps to deploy the Datadog Azure integration through Terraform.
In the Azure integration tile, click + Add New App registration, then select Terraform.
Select the subscriptions and management groups to collect data from.
Optionally, click the metric collection toggle to disable all metric collection from Azure. You can also expand the Advanced Configuration dropdown to filter metrics by:
- Resource provider
- Tags
- Hosts
- App Service Plans
- Container Apps
You can also click to enable custom metric collection from Azure Application Insights, and disable the collection of usage metrics.
Optionally, click the resource collection toggle to disable the collection of configuration information from your Azure resources.
Configure log collection:
- If a log forwarder already exists in the tenant, extend its scope to include any new subscriptions or management groups.
- If you’re creating a new log forwarder:
- Enter a resource group name to store the log forwarder control plane.
- Select a control plane subscription for the log-forwarding orchestration (LFO).
- Select a region for the control plane.
See the Architecture section of the automated log forwarding guide for more information about this architecture.
Copy and run the command under Initialize and apply the Terraform.
- You already have an app registration configured with the Monitoring Reader role for Datadog to monitor the provided scope (subscriptions or management groups), and don’t want to create new resources.
Configure the Datadog Terraform provider to interact with the Datadog API through a Terraform configuration.
Set up your Terraform configuration file using the example below as a base template. Ensure to update the following parameters before you apply the changes:
tenant_name: Your Azure Active Directory ID.client_id: Your Azure application (client) ID.client_secret: Your Azure web application secret key.
See the Datadog Azure integration resource page in the Terraform registry for further example usage and the full list of optional parameters, as well as additional Datadog resources.
resource "datadog_integration_azure" "sandbox" {
tenant_name = "<AZURE_TENANT_NAME>"
client_id = "<AZURE_CLIENT_ID>"
client_secret = "<AZURE_CLIENT_SECRET_KEY>"
}- Run
terraform apply. Wait up to 10 minutes for data to start being collected, and then view the out-of-the-box Azure overview dashboard to see metrics sent by your Azure resources.
Managing multiple subscriptions or tenants
You can use multiple provider blocks with aliases to manage Terraform resources across multiple subscriptions or tenants. Read Provider Configuration for more information.
Monitor the integration status
After the integration is configured, Datadog begins running a continuous series of calls to Azure APIs to collect critical monitoring data from your Azure environment. Sometimes these calls return errors (for example, if the provided credentials have expired). These errors can inhibit or block Datadog’s ability to collect monitoring data.
When critical errors are encountered, the Azure integration generates events in the Datadog Events Explorer, and republishes them every five minutes. You can configure an Event Monitor to trigger when these events are detected and notify the appropriate team.
Datadog provides a monitor template to help you get started. To use the monitor template:
- In Datadog, go to Monitors and click the Browse Templates button.
- Search for and select the monitor template titled [Azure] Integration Errors.
- Make any desired modifications to the search query or alert conditions. By default, the monitor triggers whenever a new error is detected, and resolves when the error has not been detected for the past 15 minutes.
- Update the notification and re-notification messages as desired. Note that the events themselves contain pertinent information about the event and are included in the notification automatically. This includes detailed information about the scope, error response, and common steps to remediate.
- Configure notifications through your preferred channels (email, Slack, PagerDuty, or others) to make sure your team is alerted about issues affecting Azure data collection.
Use an existing app registration
Use an existing app registration
Choose the existing app registration setup method if..
- You already have an app registration configured with the Monitoring Reader role for Datadog to monitor the provided scope (subscriptions or management groups), and don’t want to create new resources.
If you need to set up an app registration for Datadog, see the Quickstart or Terraform setup methods.
Instructions
- In the Datadog Azure integration tile, select Add Existing.
- In the Tenant ID field, paste your Directory (tenant) ID.
- In the Client ID field, paste the application (client) ID.
- In the Client Secret Value field, paste the value of the app registration’s client secret.
- Optionally, click the Monitor Automuting toggle to disable monitor automuting.
- Optionally, click the metric collection toggle to disable all metric collection from Azure. You can also expand the Advanced Configuration dropdown to filter metrics by:
- Resource provider
- Tags
- Hosts
- App Service Plans
- Container Apps
You can also click to enable custom metric collection from Azure Application Insights, and disable the collection of usage metrics.
- Optionally, click the resource collection toggle to disable the collection of configuration information from your Azure resources.
- Click Create Configuration.
Metric collection
Datadog’s Azure integration is built to collect all metrics from Azure Monitor. The Integrations page shows a curated list of predefined sub-integrations that provide additional out-of-the-box dashboards and monitors for specific Azure services. Many of these integrations are installed by default when Datadog recognizes data coming in from your Azure account. However, Datadog can ingest metrics from any Azure Monitor-supported resource, even if it doesn’t have a dedicated sub-integration tile.
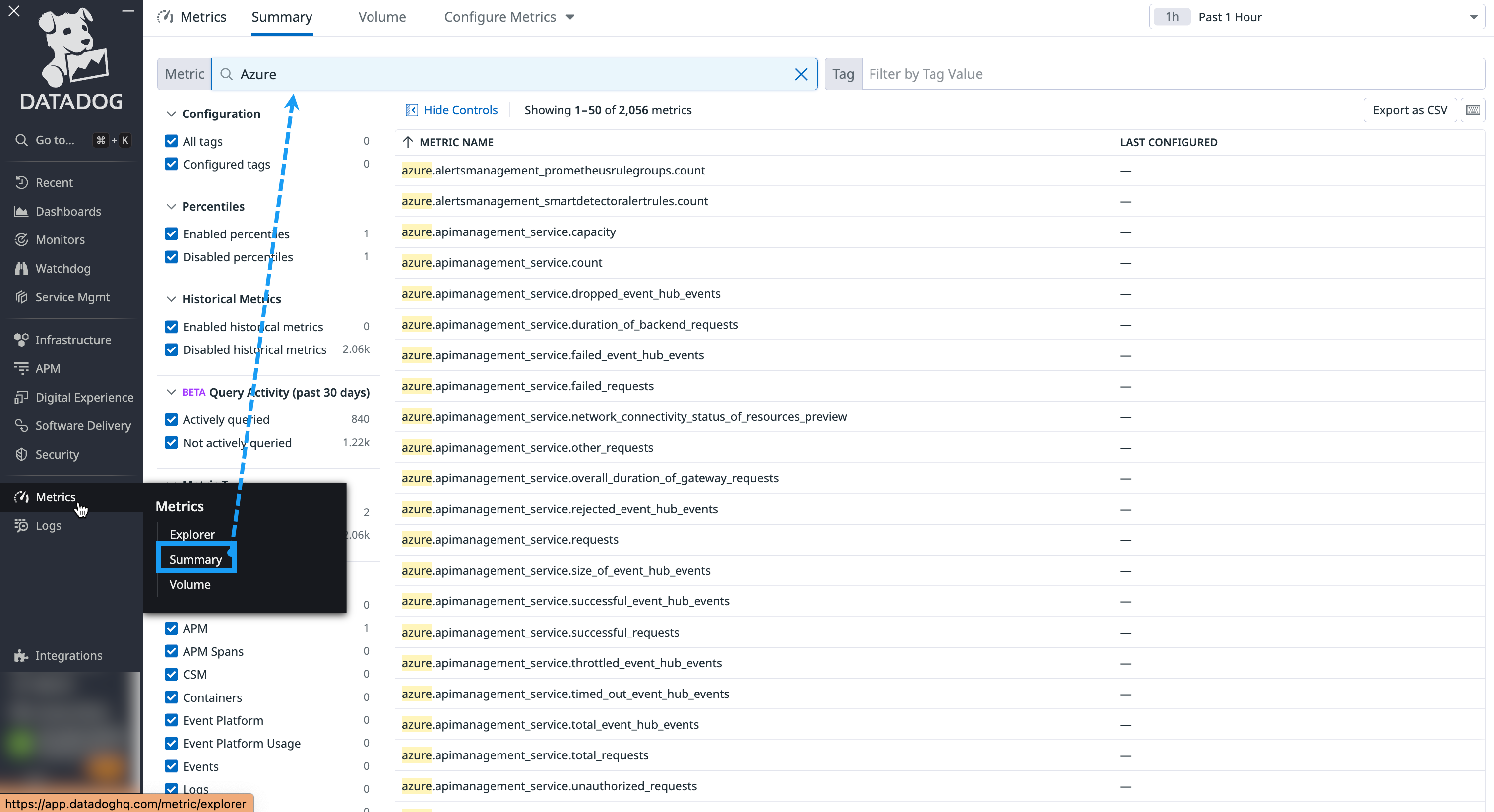
You can find your Azure metrics in the metrics summary page in the Datadog platform by navigating to Metrics > Summary and searching for Azure.
Enable log collection
You can use the automated log forwarding feature to setup and configure the services and diagnostic settings needed to forward logs to Datadog. If an automated log forwarding control plane already exists in the tenant, this flow modifies it and extends its scope to include the selected subscriptions or management groups. For more detail, see Azure Automated Log Forwarding Setup.
Datadog recommends using the Agent or DaemonSet to send logs from Azure. If direct streaming isn’t possible, you can use an Azure Resource Manager (ARM) template to automate log forwarding setup across your Azure environment with no manual configuration. This feature automatically manages and scales log forwarding services.
Automated (recommended)
Automated (recommended)
Choose the automated log forwarding setup method if…
- You haven’t already set up logs through the Quickstart setup method.
- You prefer a UI-based workflow and want to minimize the time it takes to create a service principal with the required monitoring permissions.
- You want to automate setup steps in scripts or CI/CD pipelines.
Instructions
- Open the Automated Log Forwarding ARM template in Azure.
- Configure your Azure project and instance details on the Basics tab.
- Enter your Datadog credentials on the Datadog Configuration tab.
- Acknowledge deployment warnings on the Deployment tab.
- Start the deployment process on the Review + create tab.
Log Archives require the app registration setup method. For Datadog accounts using the Azure Native integration, follow the steps on this page to create an app registration.
See Azure Automated Log Forwarding Architecture for more details.
Container App
Container App
Choose the Container App log forwarding method if…
- You prefer to manually configure diagnostic settings on the resources you want to forward logs from.
Instructions
Click the button below, and fill in the form on the Azure Portal. Datadog automatically deploys the Azure resources required to forward logs into your Datadog account.
After the template deployment finishes, set up diagnostic settings for each log source to send Azure platform logs (including resource logs) to the Storage Account created during deployment.
Note: Resources can only stream to a Storage Account in the same Azure region.
Log archiving
Archiving logs to Azure Blob Storage requires an App Registration. If you haven’t already, follow the automatic or manual setup instructions to configure the integration using an App Registration. App Registrations created for archiving purposes do not need the Monitoring Reader role.
After configuring an App Registration, create a log archive that writes to Azure Blob Storage.
Note: If your storage bucket is in a subscription being monitored through the Azure Native integration, a redundancy warning appears in the Azure integration tile. This warning can be safely ignored for log archiving.
Get more from the Datadog Platform
Install the Agent for greater visibility into your application
After you set up your Azure integration, Datadog crawlers automatically collect Azure metrics, but you can gain even deeper visibility into your Azure instances with the Datadog Agent. Installing the Datadog Agent into your environment allows you to collect additional data including, but not limited to:
- Application health
- Process utilization
- System-level metrics
You can also use the built-in StatsD client to send custom metrics from your applications, to correlate what’s happening with your applications, users, and system. See the guide on Why should I install the Datadog Agent on my cloud instances? for more information on the benefits of installing the Datadog Agent on your instances.
Use the Azure extension to install the Datadog Agent on Windows VMs, Linux x64 VMs, and Linux ARM-based VMs. You can also use the AKS Cluster Extension to deploy the Agent to your AKS Clusters.
- In the Azure portal, select the appropriate VM.
- From the left sidebar, under Settings, select Extensions + applications.
- Click + Add.
- Search for and select the
Datadog Agentextension. - Click Next.
- Enter your Datadog API key and Datadog site, and click OK.
To install the Agent based on operating system or CI and CD tool, see the Datadog Agent installation instructions.
Note: Domain controllers are not supported when installing the Datadog Agent with the Azure extension.
The Datadog AKS Cluster Extension allows you to deploy the Datadog Agent natively within Azure AKS, avoiding the complexity of third-party management tools. To install the Datadog Agent with the AKS Cluster Extension:
- Go to your AKS cluster in the Azure portal.
- From the left sidebar of the AKS cluster, select Extensions + applications under Settings.
- Search for and select the
Datadog AKS Cluster Extension. - Click Create, and follow the instructions in the tile using your Datadog credentials and Datadog site.
Troubleshooting
See Troubleshooting in the Azure Advanced Configuration guide.
Still need help? Contact Datadog support.
Further Reading
Additional helpful documentation, links, and articles: