- Principales informations
- Getting Started
- Agent
- API
- Tracing
- Conteneurs
- Dashboards
- Database Monitoring
- Datadog
- Site Datadog
- DevSecOps
- Incident Management
- Intégrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profileur
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Surveillance Synthetic
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- Développeurs
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Application mobile
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Alertes
- Watchdog
- Métriques
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Conteneurs
- Processes
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Termes et concepts de l'APM
- Sending Traces to Datadog
- APM Metrics Collection
- Trace Pipeline Configuration
- Connect Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilité des services
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Suivi des erreurs
- Sécurité des données
- Guides
- Dépannage
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Exploring Database Schemas
- Exploring Recommendations
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM et Session Replay
- Surveillance Synthetic
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- Securité
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- CloudPrem
- Administration
Forescout
Supported OS
Intégration1.0.0
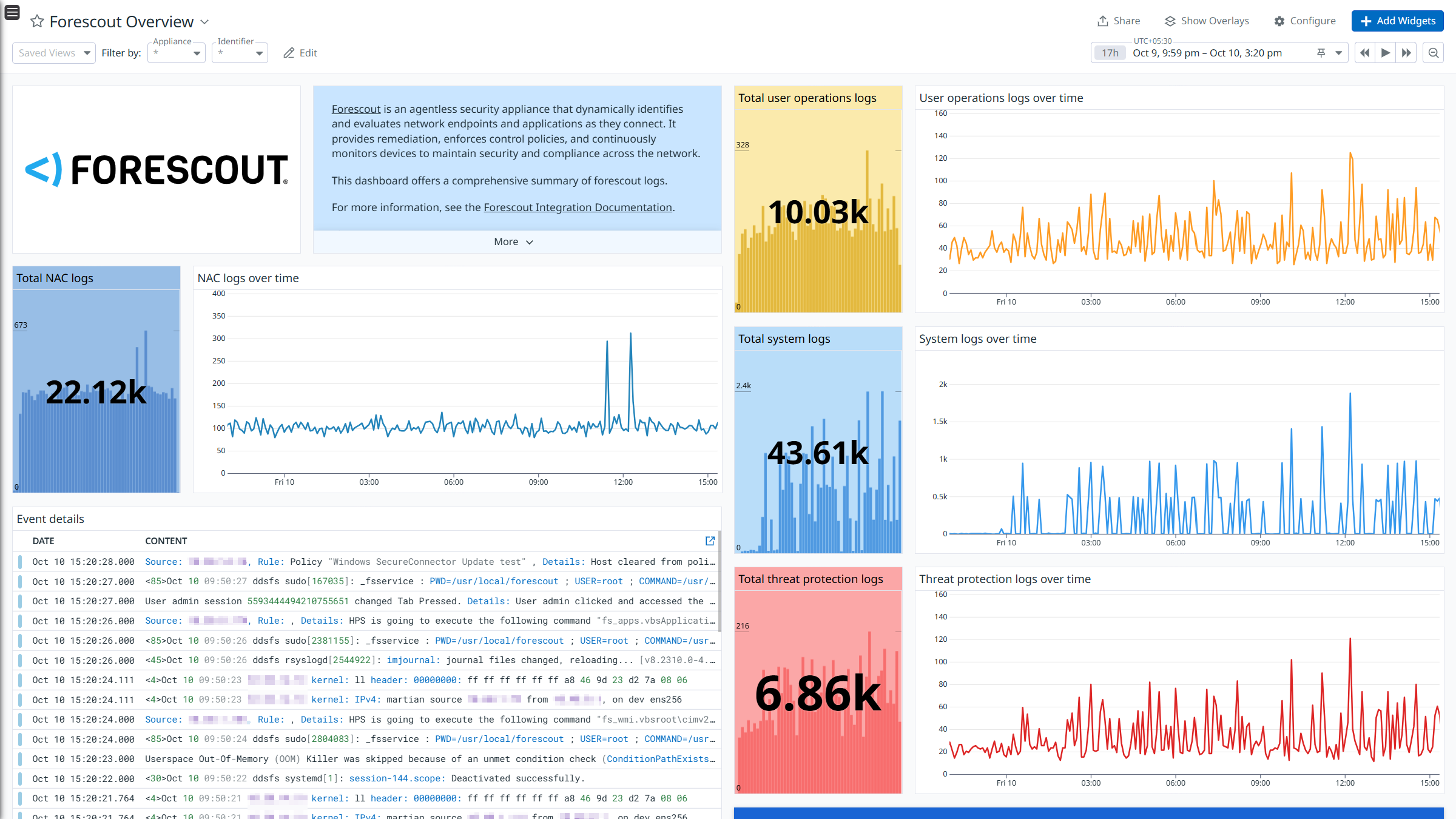
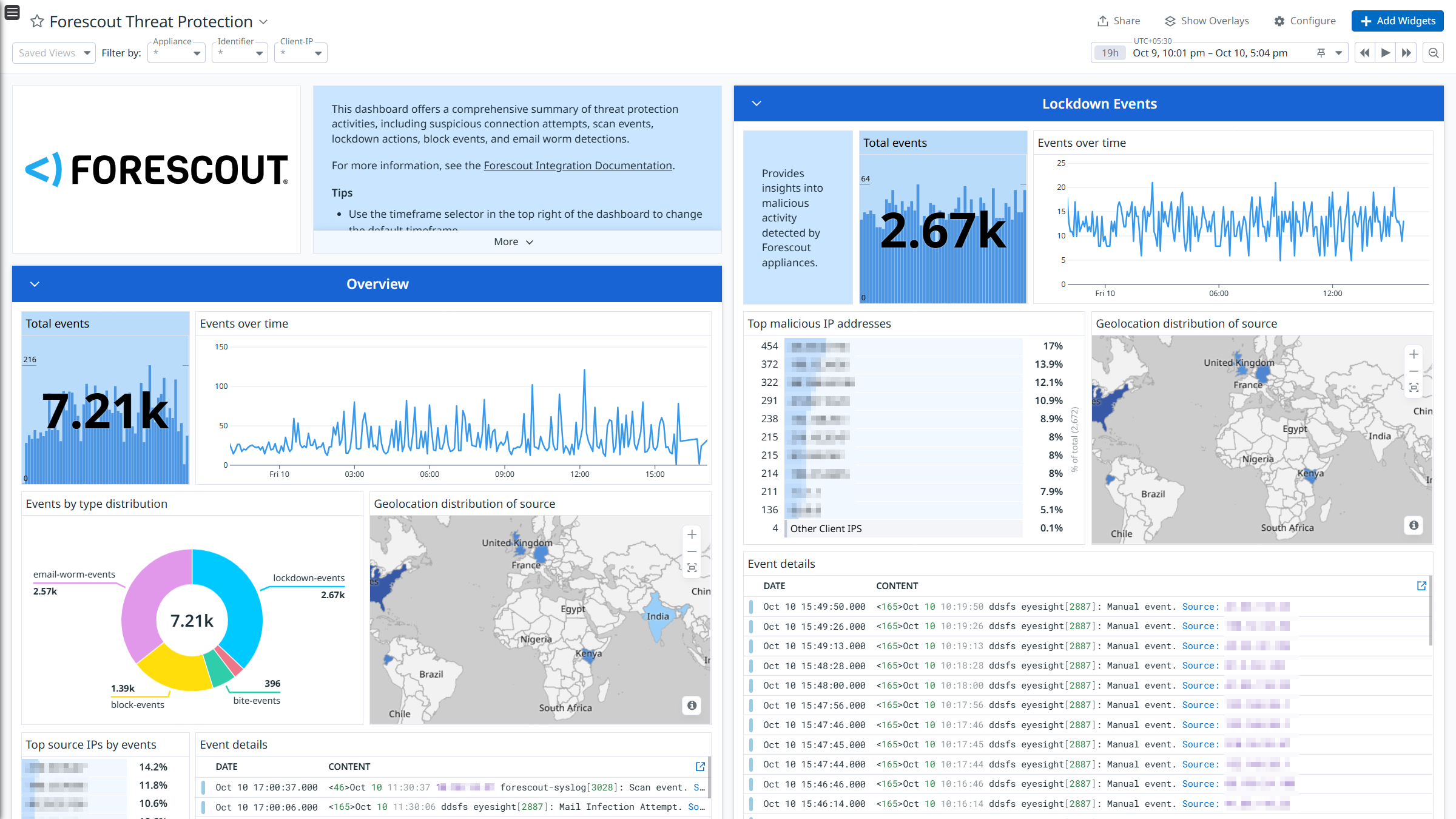
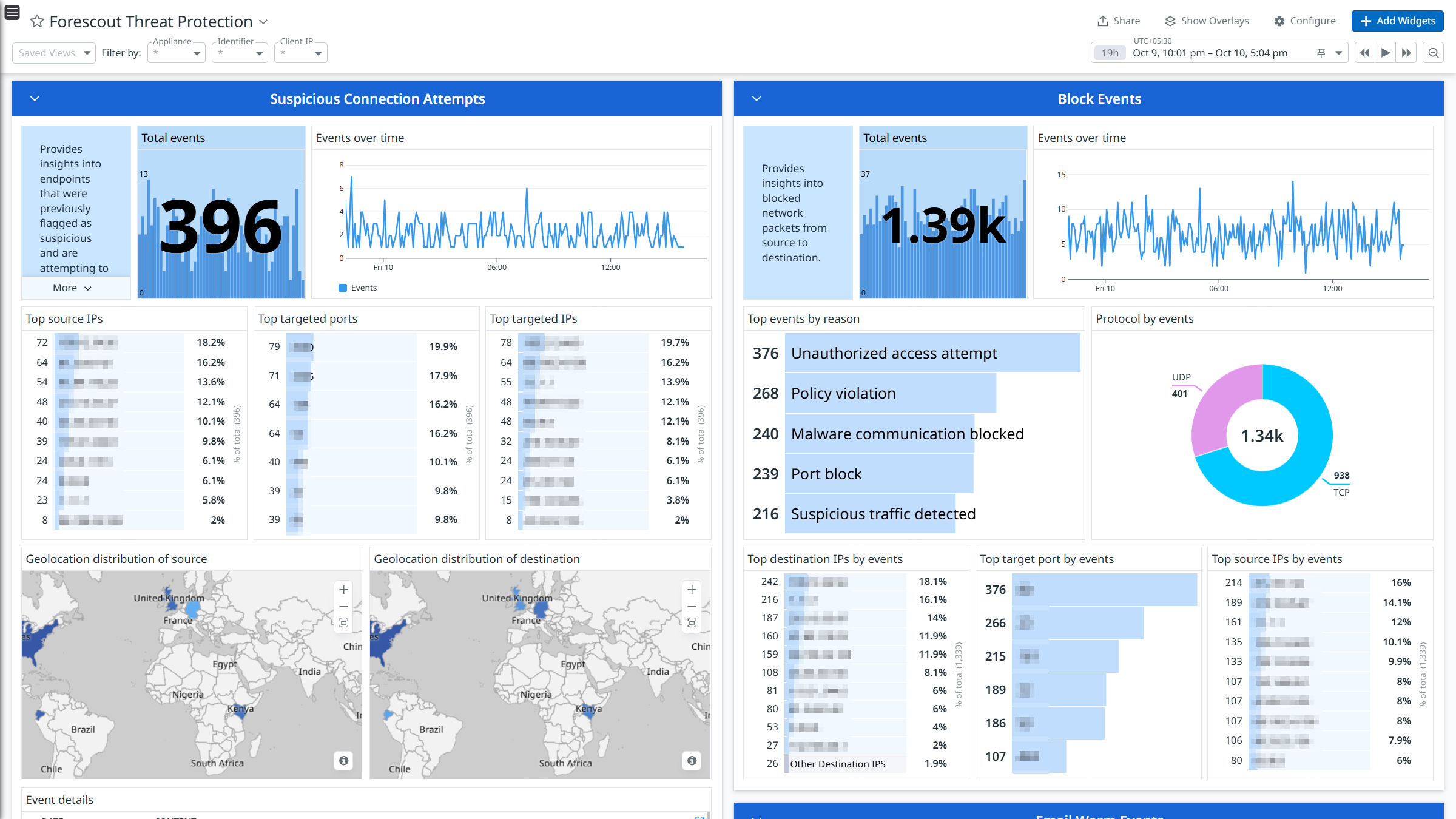
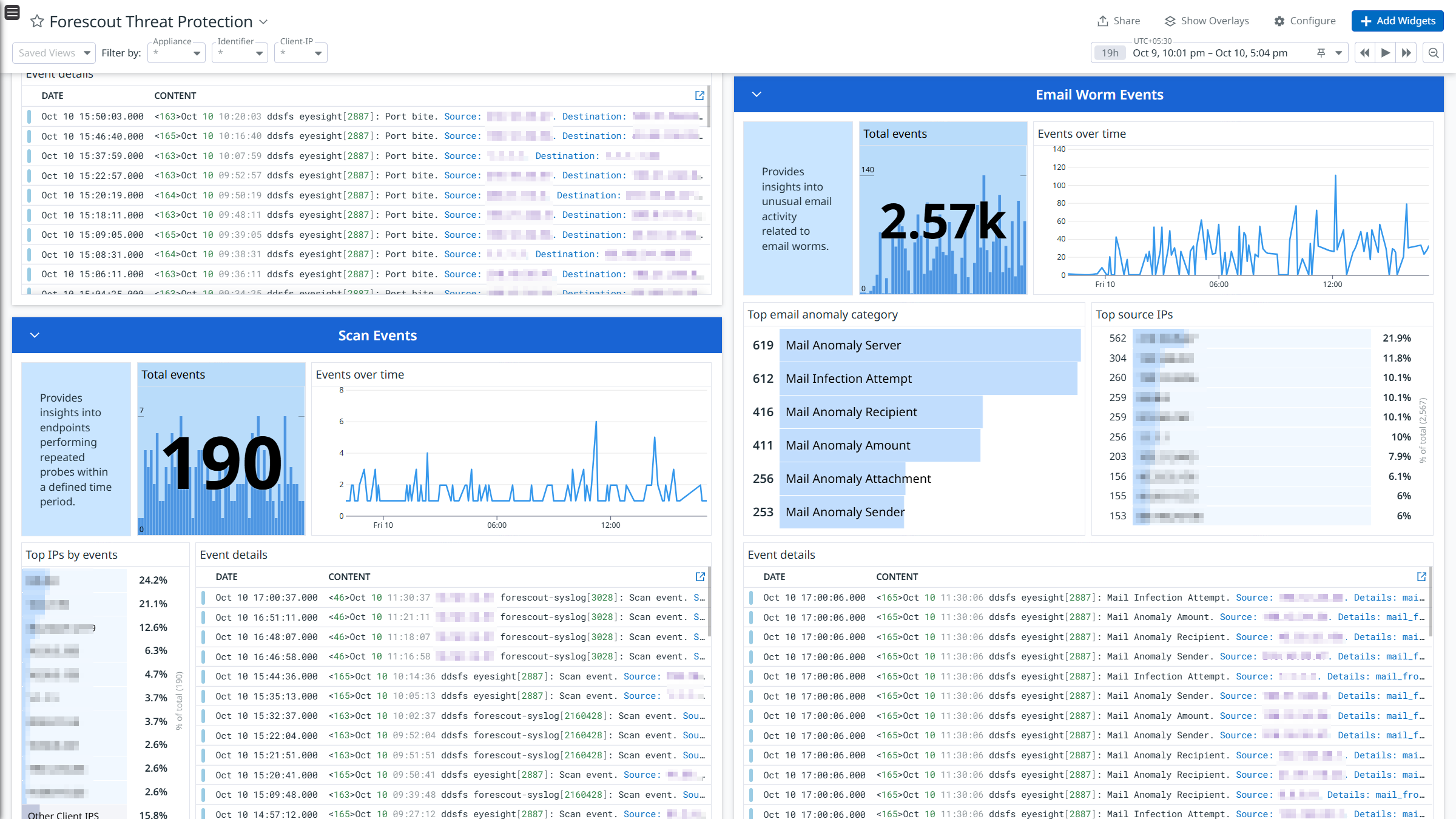
Forescout Overview
Forescout Threat Protection
Forescout Threat Protection
Forescout Threat Protection
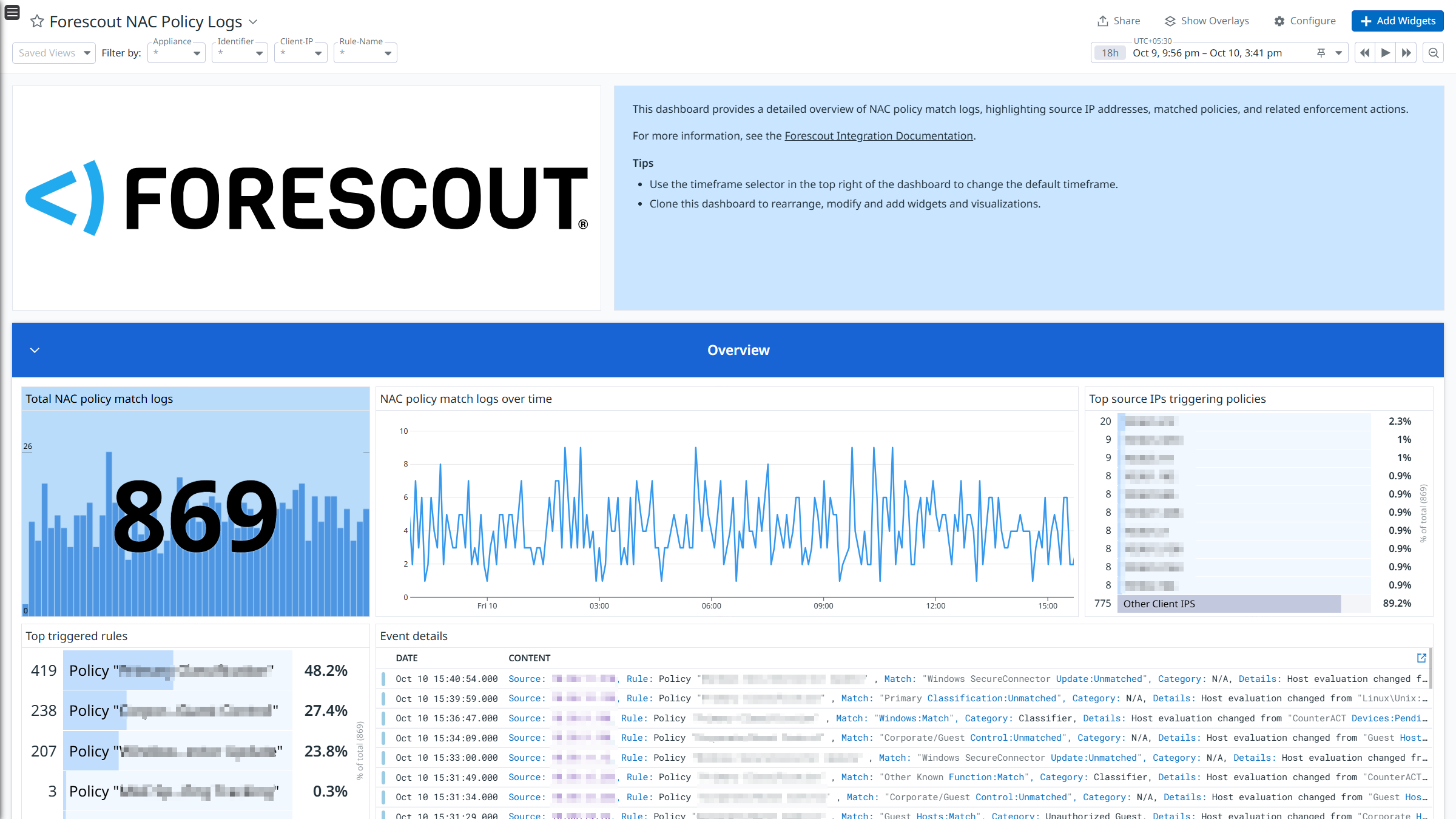
Forescout NAC Policy Logs
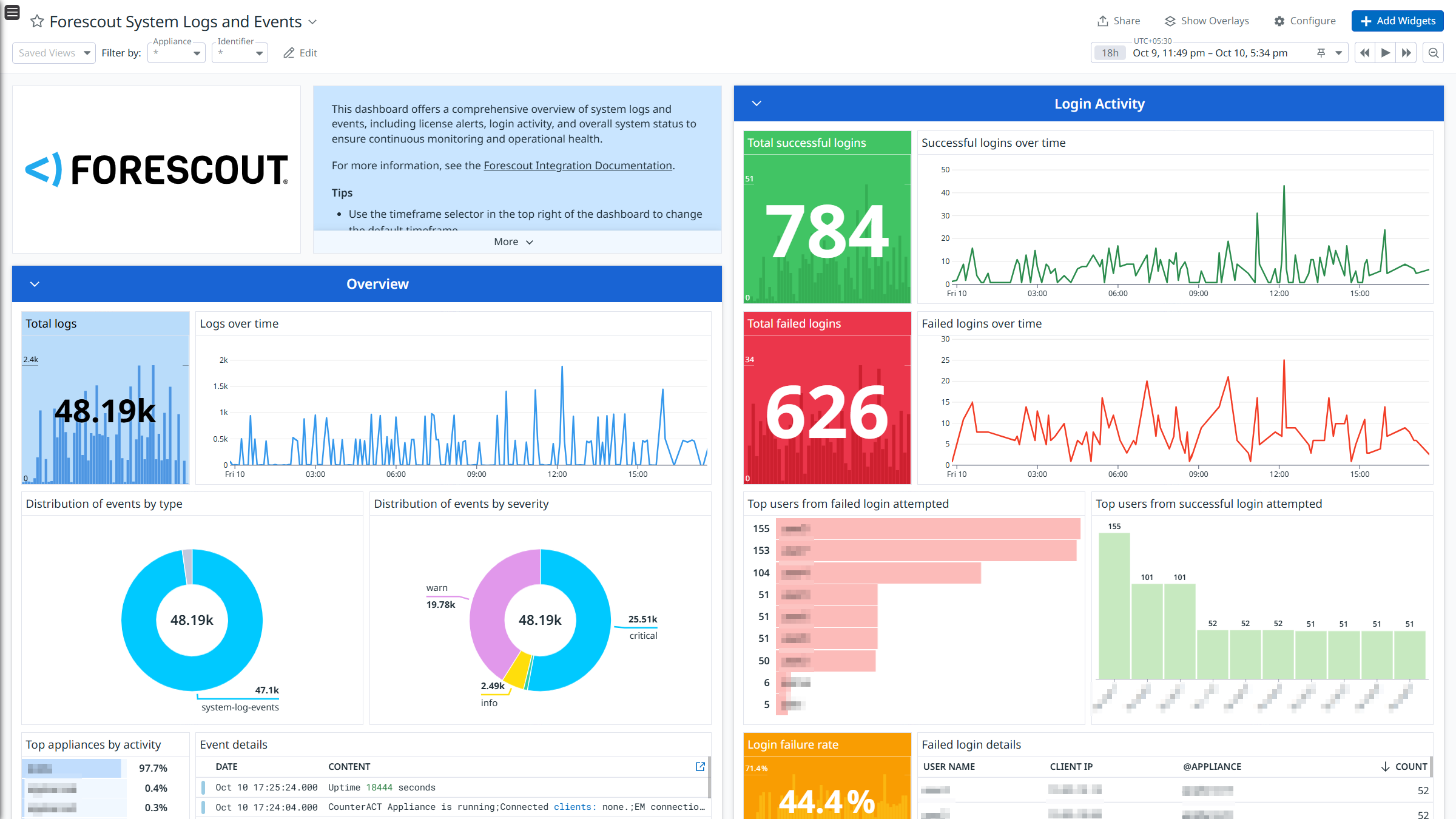
Forescout System Logs and Events
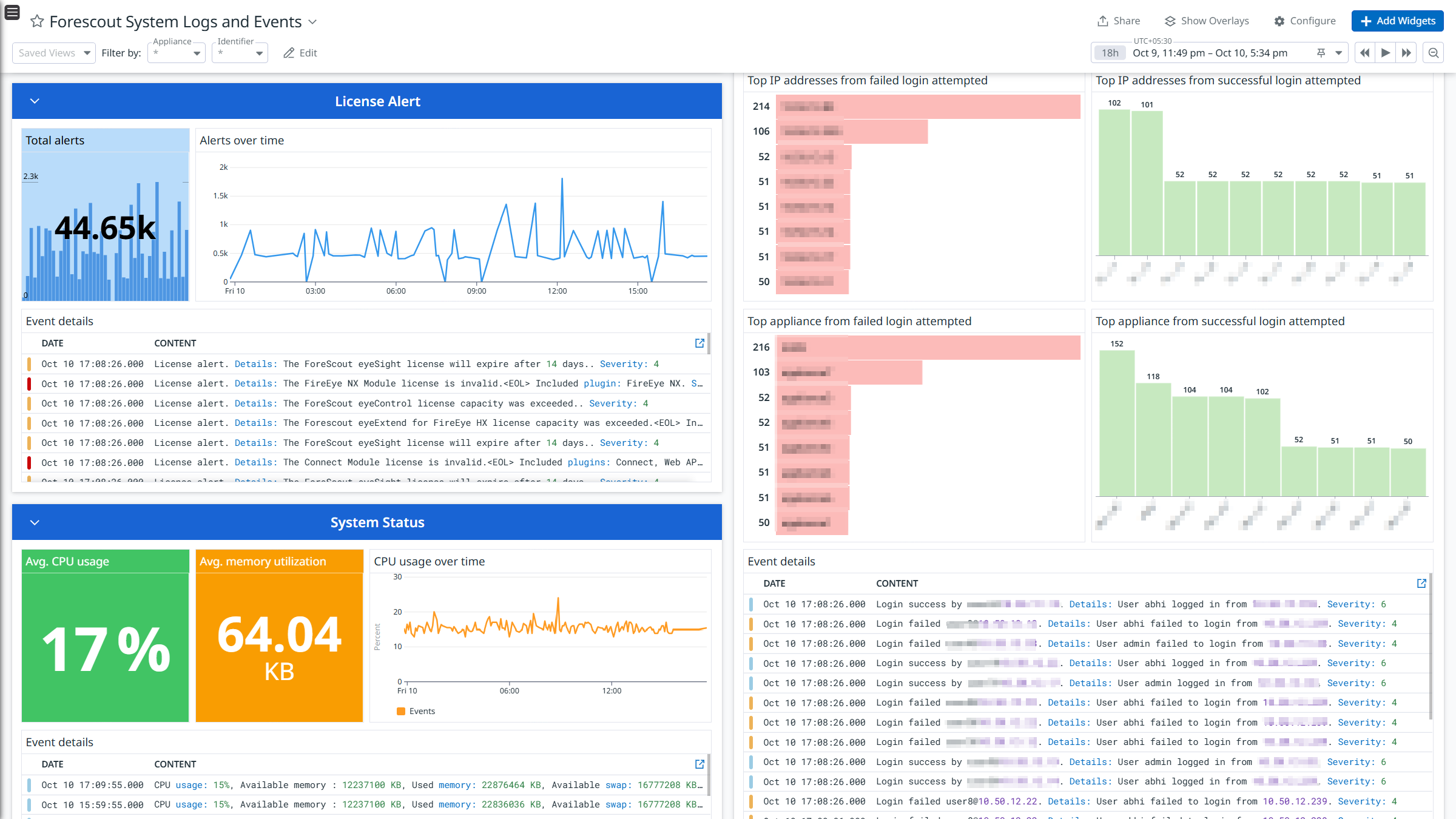
Forescout System Logs and Events
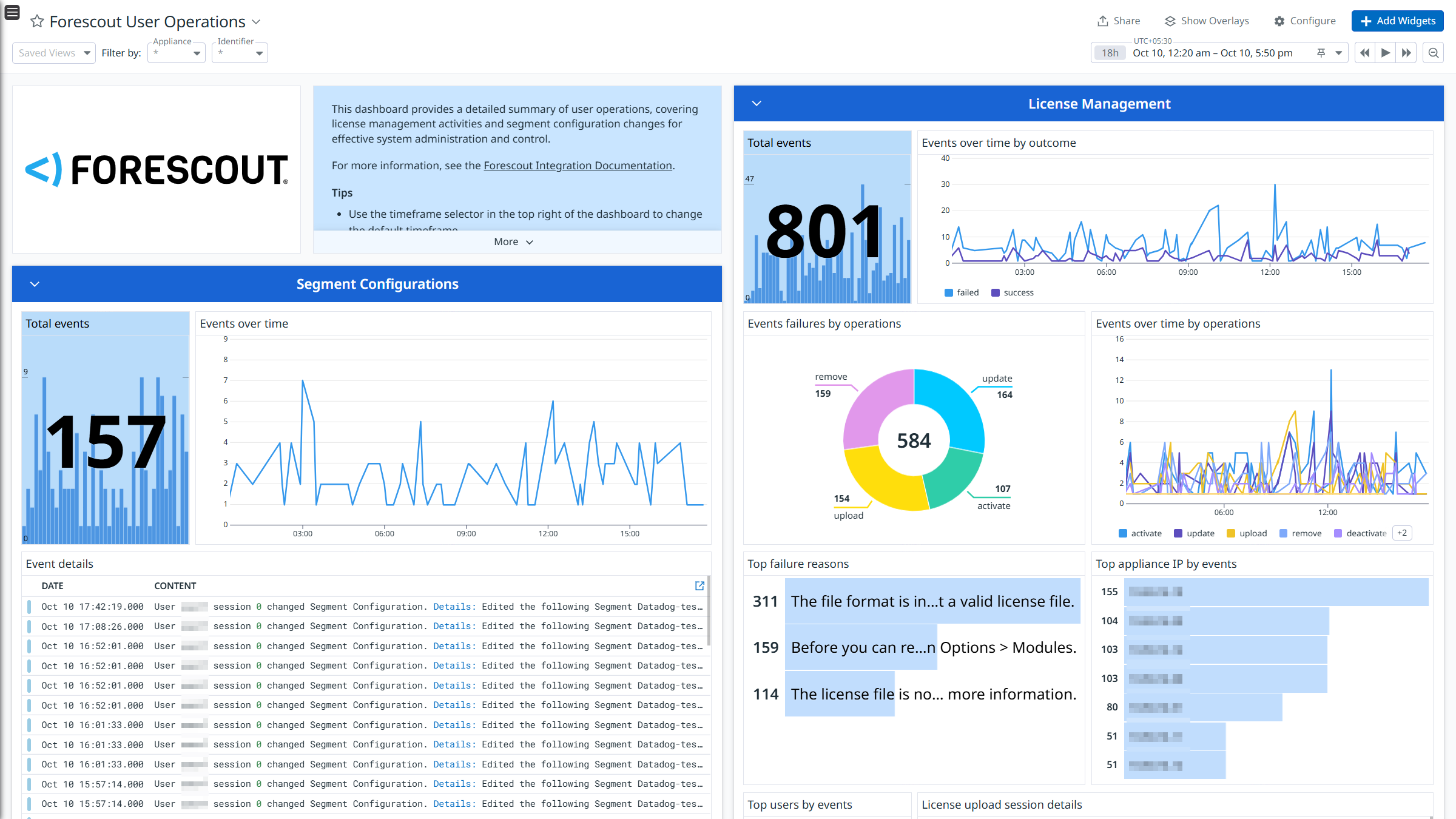
Forescout User Operations
Cette page n'est pas encore disponible en français, sa traduction est en cours.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Overview
Forescout is a security appliance designed to dynamically detect and assess network endpoints and applications as they connect. It enforces control policies, provides remediation, and continuously monitors devices to ensure security and compliance across the network.
Integrate Forescout with Datadog’s pre-built dashboard visualizations to gain insights into NAC Policy, Threat Protection, System Logs, and User Operations logs. With Datadog’s built-in log pipeline, you can parse and enrich these logs to facilitate easy search and detailed insights. The integration can also be used for Cloud SIEM detection rules for enhanced monitoring and security.
Minimum Agent version: 7.73.0
Setup
Prerequisites
- The
Syslogplugin must be installed in your Forescout setup.
Configuration
Log Collection
Collecting logs is disabled by default in the Datadog Agent. Enable it in the
datadog.yamlfile with:logs_enabled: trueAdd this configuration block to your
forescout.d/conf.yamlfile to start collecting your Forescout logs:logs: - type: tcp # or 'udp' port: <PORT> source: forescout service: forescoutSee the sample configuration file (forescout.d/conf.yaml) for available options.
Note: Do not change the source and service values, as these parameters are integral to the pipeline’s operation.
Configure timezone in Forescout
Follow these steps if the Forescout appliance is not in the GMT timezone.
- Log in to the Forescout CounterACT appliance using root access via the command shell.
- Run the timezone configuration command:
fstool tz - Follow the setup prompts and configure the options as needed:
Select different time-zone? (yes/no): yes Choice (1-2) [1]: 2 Enter the GMT offset (number between -14 and 12): 0 Confirm Set time-zone to GMT? (yes/no) [yes]: yes Reboot is required to fully apply the time-zone change. Reboot now: yes
Configure syslog message forwarding from Forescout
- Log in to the Forescout Console.
- Navigate to Tools > Options.
- Click Syslog from the options list.
- Go to the Send Events To section and click Add.
- Enter the details as below for syslog configuration:
- Server Address: Enter the IP address or hostname of the syslog server.
- Server Port: Specify the port number on which the syslog server is listening.
- Server Protocol: Select the protocol (UDP or TCP) to send the syslog messages.
- Identity: Set this to
forescout-syslog. - Facility: Set this to
syslog. - Severity: Set this to
info.
- Click OK.
- Go to the Syslog Triggers tab and configure the following:
- Ensure the Include only messages generated by the “Send Message to Syslog” action checkbox is deselected.
- In the Select format type for system log events and user operations dropdown, select Short.
- Under NAC Events, Threat Protection, System Logs and Events, and User Operations, include all the event types.
- Click Apply.
Note: The Server Port value should be similar to the port provided in the Log Collection section.
Validation
Run the Agent’s status subcommand and look for forescout under the Logs Agent section.
Data Collected
Logs
The Forescout integration collects NAC Policy, Threat Protection, System, and User Operations logs.
Metrics
The Forescout does not include any metrics.
Events
The Forescout integration does not include any events.
Troubleshooting
Need help? Contact Datadog support.
