- Principales informations
- Getting Started
- Agent
- API
- Tracing
- Conteneurs
- Dashboards
- Database Monitoring
- Datadog
- Site Datadog
- DevSecOps
- Incident Management
- Intégrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profileur
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Surveillance Synthetic
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- Développeurs
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Application mobile
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Alertes
- Watchdog
- Métriques
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Conteneurs
- Processes
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Termes et concepts de l'APM
- Sending Traces to Datadog
- APM Metrics Collection
- Trace Pipeline Configuration
- Connect Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilité des services
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Suivi des erreurs
- Sécurité des données
- Guides
- Dépannage
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Exploring Database Schemas
- Exploring Recommendations
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM et Session Replay
- Surveillance Synthetic
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- Securité
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- CloudPrem
- Administration
Détection des changements de code
Ce produit n'est pas pris en charge par le site Datadog que vous avez sélectionné. ().
Rejoignez la version Preview !
CD Visibility est en version Preview. Si cette fonctionnalité vous intéresse, remplissez le formulaire pour demander l'accès.
Request AccessPrésentation
La détection des changements de code permet à Datadog d’identifier les commits appliqués dans le cadre d’un déploiement. Cette fonctionnalité présente plusieurs avantages :
- Elle permet de comprendre où des changements spécifiques ont été déployés, par exemple en surveillant le moment où les mises à jour sont appliquées à l’environnement
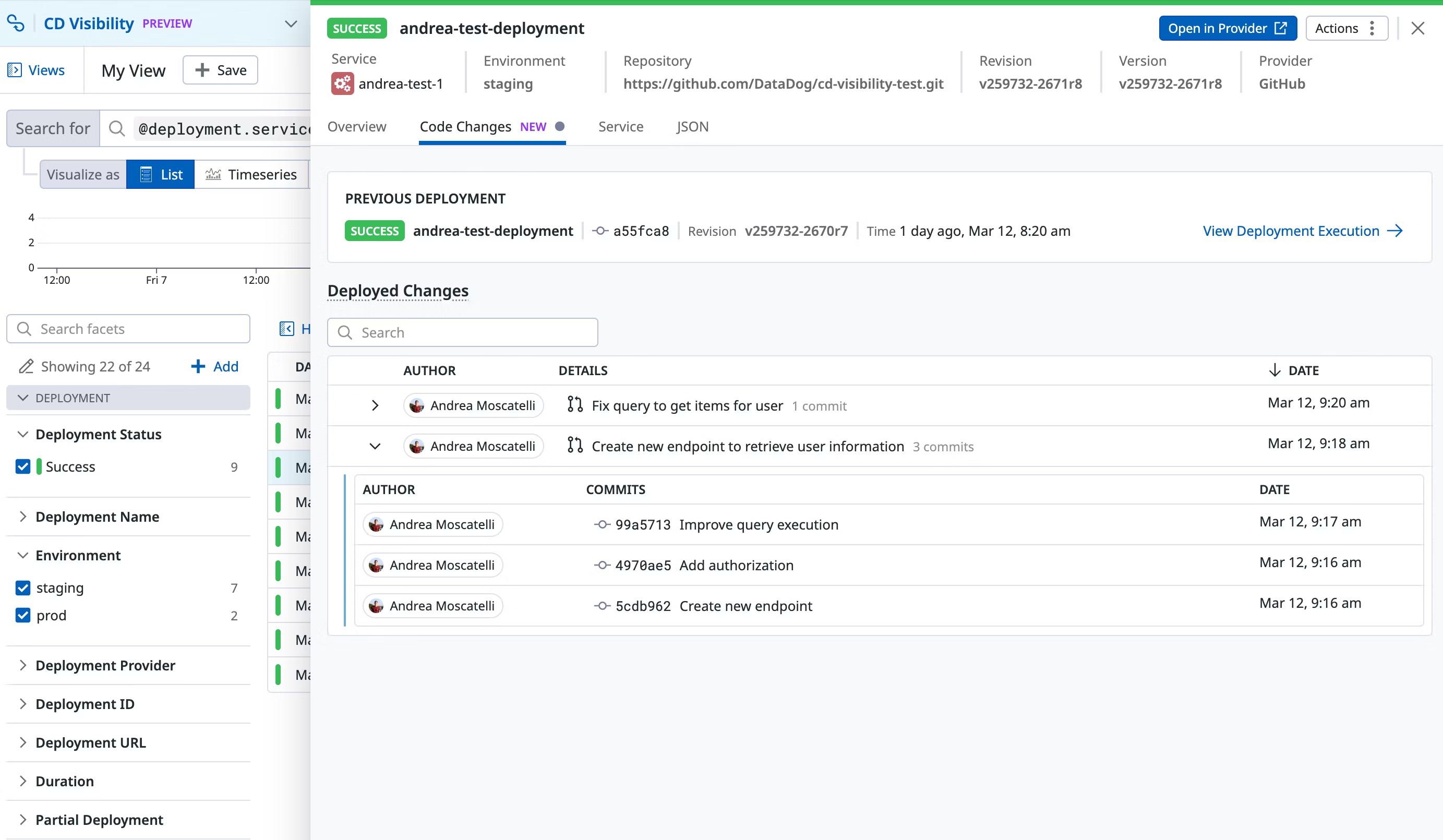
production. - Elle permet de diagnostiquer les incidents liés à un déploiement en fournissant des données sur les changements précis appliqués, afin que les équipes puissent identifier rapidement les causes fondamentales potentielles et ainsi résoudre plus rapidement les problèmes.
Pour détecter les changements de code déployés, Datadog exécute git log entre le SHA du commit de déploiement actuel et celui du déploiement précédent. Les commits de fusion sont exclus du calcul.
Les changements de code déployés sont affichés dans toutes les exécutions de déploiement de la page Deployment Executions. L’onglet Code Changes indique le déploiement précédent pris en compte ainsi que les changements de code détectés entre les deux déploiements.
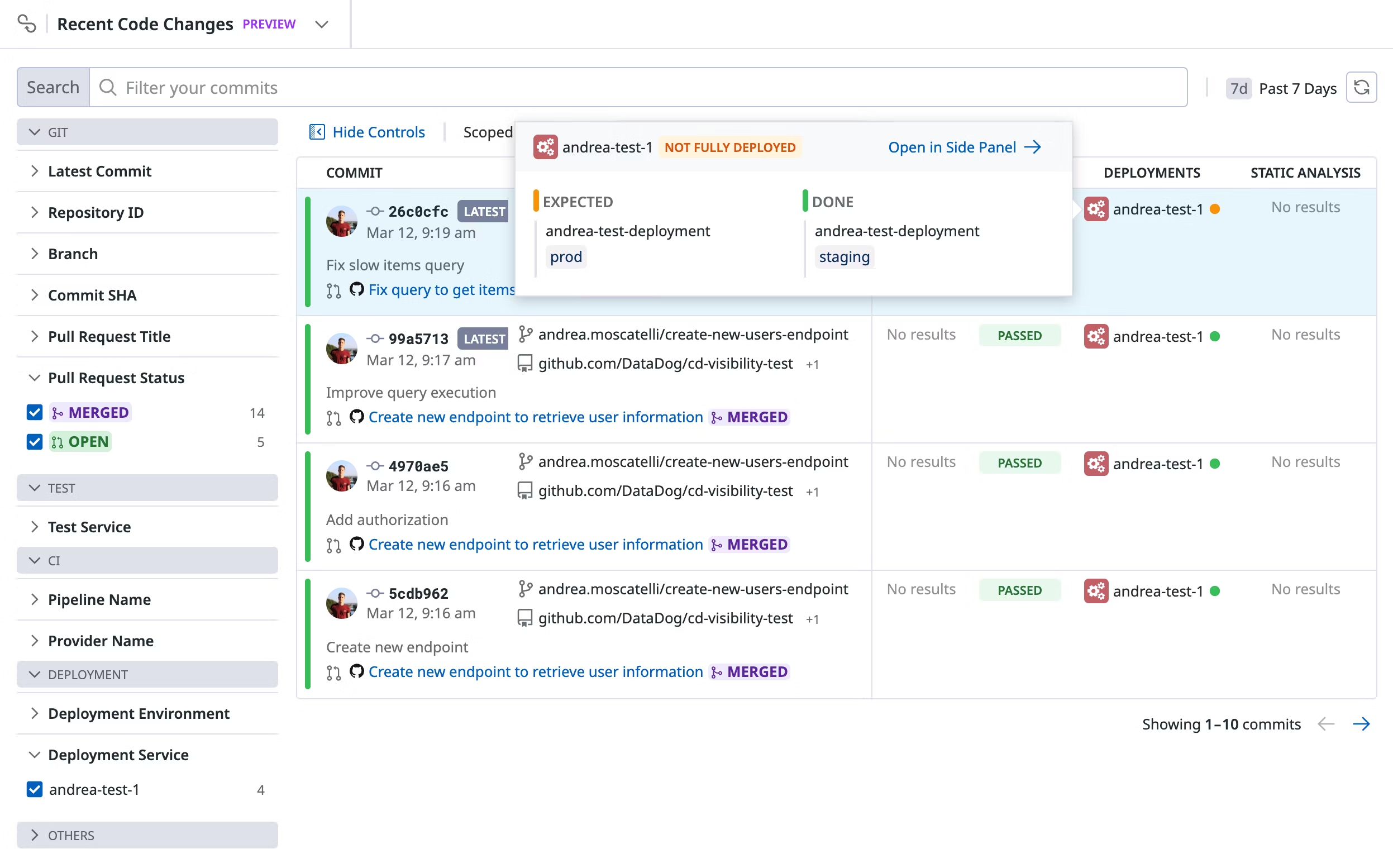
En outre, la colonne Deployments de la page Recent Code Changes affiche les détails du service et de l’environnement pour tous les déploiements qui incluent un commit spécifique. Cette vue permet de comprendre rapidement si (et où) des changements de code ont été appliqués. Survolez la valeur de service pour découvrir si le déploiement a atteint tous les environnements prévus, en fonction des emplacements où le service est généralement déployé.
Les changements de code ne sont détectés que pour les déploiements qui :
- possèdent un service (
@deployment.service) avec des spécifications de chemin de fichier définies dans le Software Catalog (voir les instructions de configuration pour en savoir plus) ; - possèdent un environnement (
@deployment.env) ; - possèdent une URL de référentiel (
@deployment.git.repository_url) et un SHA de commit (@deployment.git.commit.sha).
Configuration
Pour autoriser la détection des changements de code pour vos déploiements, vous devez suivre deux étapes :
- Synchronisez vos métadonnées de référentiel avec Datadog.
- Spécifiez le chemin du fichier de code source pour vos services.
Synchroniser vos métadonnées de référentiel avec Datadog
Les workflows GitHub exécutant le déclencheur
pull_request ne sont pas pris en charge par l'intégration GitHub.
Si vous utilisez le déclencheur pull_request, utilisez l'autre méthode.Si vous n’avez pas encore installé l’intégration GitHub, installez-la depuis le carré d’intégration GitHub.
Lors de la configuration de l’application GitHub :
- Sélectionnez au minimum les autorisations de référentiel Read pour Contents et Pull Requests.
- Abonnez-vous au moins aux événements Push, PullRequest et PullRequestReview.
Pour confirmer que la configuration est valide, sélectionnez votre application GitHub dans le carré d’intégration GitHub et vérifiez que, dans le tableau Datadog Features, la fonctionnalité Pull Request Information est indiquée comme valide.
Suivez le processus d’intégration dans l’application pour configurer l’intégration du code source GitLab.
Remarque : la portée du token d’accès personnel du compte de service doit être au minimum définie sur read_api.
Vous pouvez télécharger vos métadonnées de référentiel Git avec la commande datadog-ci git-metadata upload. À l’exécution de cette commande, Datadog reçoit l’URL du référentiel, le SHA de commit de la branche actuelle et la liste des chemins de fichier suivis.
Exécutez cette commande dans CI pour chaque nouveau commit. Lorsqu’un déploiement est exécuté pour un SHA de commit spécifique, assurez-vous que la commande datadog-ci git-metadata upload est exécutée pour ce commit avant que l’événement de déploiement ne soit envoyé.
Ne spécifiez pas l'option
--no-gitsync dans la commande datadog-ci git-metadata upload. Lorsqu'elle est incluse, cette option annule l'envoi des informations de commit à Datadog, ce qui empêche la détection des changements.Vous pouvez vérifier que la configuration de la commande est correcte en consultant la sortie de la commande. Voici un exemple de sortie correcte :
Reporting commit 007f7f466e035b052415134600ea899693e7bb34 from repository git@github.com:organization/example-repository.git.
180 tracked file paths will be reported.
✅ Handled in 0.077 seconds.
Spécifier des patterns de chemin de fichier de service
Pour pouvoir comprendre les changements de code introduits par un déploiement, vous devez uniquement prendre en compte les commits affectant le service déployé.
Pour y parvenir dans le Software Catalog, spécifiez, pour les services pertinents, des patterns de chemin de fichier globaux pour le code source dans la définition du service.
Si la définition du service contient une URL GitHub ou GitLab complète vers le dossier de l’application, un pattern de chemin unique est automatiquement utilisé. Le type de lien doit être défini sur repo et le nom du lien doit correspondre à « Source » ou au nom du service (shopist dans les exemples ci-dessous).
Si votre référentiel contient un seul service et que vous souhaitez que tous les répertoires soient pris en compte pour la détection des changements de code, vous pouvez ignorer cette étape. Si vous déployez plusieurs services à partir d’un référentiel, il est nécessaire de spécifier des patterns de chemin de code source.
Exemple (schéma v2.2) :
links:
- name: shopist
type: repo
provider: github
url: https://github.com/organization/example-repository/tree/main/src/apps/shopist
links:
- name: shopist
type: repo
provider: gitlab
url: https://gitlab.com/organization/example-repository/-/tree/main/src/apps/shopist?ref_type=heads
La détection des changements de code pour les déploiements du service shopist ne prend en compte que les commits Git qui incluent des changements dans le chemin src/apps/shopist/**. Vous pouvez configurer un contrôle plus granulaire avec extensions[datadoghq.com/cd-visibility] ou extensions[datadoghq.com/dora-metrics]. Si les deux extensions sont détectées, l’extension extensions[datadoghq.com/cd-visibility] est utilisée.
Exemple (schéma v2.2) :
extensions:
datadoghq.com/cd-visibility:
source_patterns:
- src/apps/shopist/**
- src/libs/utils/**
La détection des changements de code pour les déploiements du service shopist ne prend en compte que les commits Git qui incluent des changements dans le chemin src/apps/shopist/** ou le chemin src/libs/utils/**.
Si des patterns de code source pour un service sont définis à la fois dans un lien et dans une extension, seule l’extension est prise en compte lors du filtrage des commits.
Utiliser des patterns de chemins de fichier de service pour suivre les modifications dans l’ensemble du référentiel
Pour détecter les changements dans l’ensemble du référentiel, utilisez des patterns de chemin de fichier appropriés. Par exemple, "**" renvoie tous les fichiers.
Exemple (schéma v2.2) :
extensions:
datadoghq.com/cd-visibility:
source_patterns:
- "**"
Dans cet exemple, la détection des changements de code pour les déploiements du service shopist prend en compte les commits Git qui incluent des changements dans l’ensemble de l’arborescence du référentiel.
Si un pattern correspond exactement à
** ou commence par ces caractères, ajoutez des guillemets autour des astérisques, car le caractère * est réservé aux ancres dans YAML.Pour aller plus loin
Documentation, liens et articles supplémentaires utiles: