- Principales informations
- Getting Started
- Agent
- API
- Tracing
- Conteneurs
- Dashboards
- Database Monitoring
- Datadog
- Site Datadog
- DevSecOps
- Incident Management
- Intégrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profileur
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Surveillance Synthetic
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- Développeurs
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Application mobile
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Alertes
- Watchdog
- Métriques
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Conteneurs
- Processes
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Termes et concepts de l'APM
- Sending Traces to Datadog
- APM Metrics Collection
- Trace Pipeline Configuration
- Connect Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilité des services
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Suivi des erreurs
- Sécurité des données
- Guides
- Dépannage
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Exploring Database Schemas
- Exploring Recommendations
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM et Session Replay
- Surveillance Synthetic
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- Securité
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- CloudPrem
- Administration
Architecture de l'Agent 5
Cette page couvre l’architecture de l’Agent 5. Pour en savoir plus sur l’architecture de la dernière version de l’Agent, consultez la section Architecture de l’Agent.
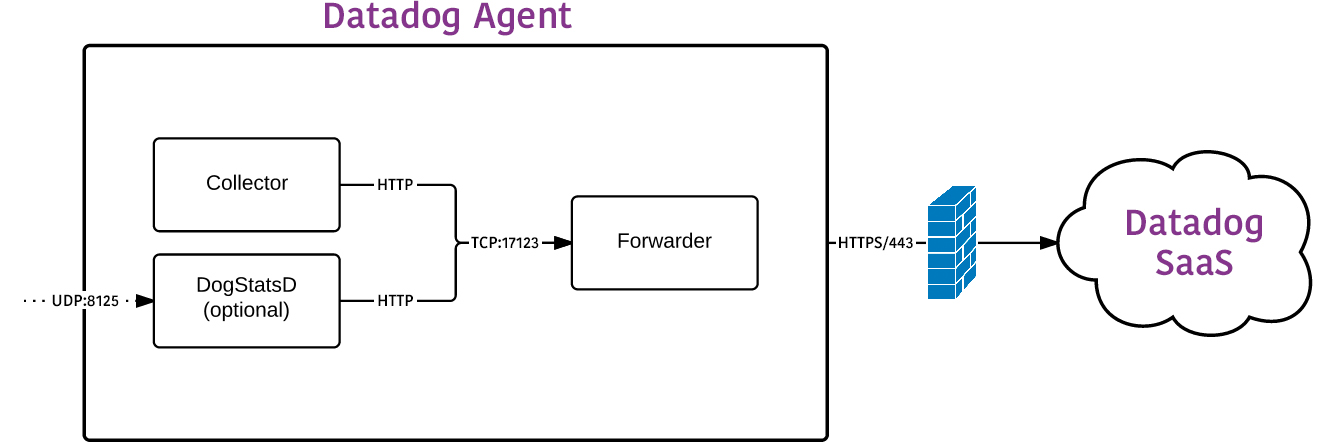
L’Agent 5 est composé de quatre composants majeurs, chacun écrit en Python et exécuté en tant que processus séparé :
- Collector (
agent.py) : le collector exécute des checks sur la machine actuelle pour les intégrations configurées et capture les métriques système, telles que la mémoire et le processeur. - DogStatsD (
dogstatsd.py) : il s’agit d’un serveur backend compatible StatsD auquel vous pouvez envoyer des métriques custom depuis vos applications. - Forwarder (
ddagent.py) : le forwarder récupère les données de DogStatsD et du collector, les met en file d’attente pour envoi, puis les envoie à Datadog. - SupervisorD : le collector, le serveur DogStatsD et le forwarder sont tous contrôlés par un seul processus superviseur. Le superviseur est maintenu séparé pour limiter la surcharge de chaque application si vous n’exécutez pas toutes les parties. Cependant, il est généralement recommandé d’exécuter toutes les parties.
Remarque : pour les utilisateurs de Windows, les quatre processus de l’Agent apparaissent sous forme d’instances de ddagent.exe, avec la description DevOps' best friend.
Supervision, privilèges et ports réseau
Un processus principal SupervisorD s’exécute en tant qu’utilisateur dd-agent, et tous les sous-processus créés s’exécutent en tant que même utilisateur. Cela s’applique également à tout appel système (iostat, netstat) initié par l’Agent Datadog. La configuration de l’Agent se trouve dans /etc/dd-agent/datadog.conf et /etc/dd-agent/conf.d. Toute la configuration doit être lisible par dd-agent. Les autorisations recommandées sont 0600, car les fichiers de configuration contiennent votre clé API et d’autres identifiants nécessaires pour accéder aux métriques.
Les ports suivants sont ouverts pour les opérations :
| Port | Rôle |
|---|---|
| tcp/17123 | Utilisé par le Forwarder pour les opérations normales |
| tcp/17124 | Utilisé par le Forwarder pour la prise en charge de Graphite |
| udp/8125 | DogStatsD |
Tous les processus d’écoute sont liés par défaut à 127.0.0.1 ou ::1 ou les deux, sur les versions d’Agent 3.4.1 ou ultérieures. Dans les versions antérieures, ils étaient liés à 0.0.0.0 (toutes les interfaces). Pour plus d’informations sur l’exécution de l’Agent via un proxy, consultez la section Configuration du proxy de l’Agent. Pour plus d’informations sur les plages d’adresses IP à autoriser, consultez la section Trafic réseau.
Nous vous conseillons de prévoir 1024 descripteurs de fichiers ouverts. Vous pouvez consulter cette valeur avec la commande ulimit -a. Si vous êtes contraint d’utiliser une valeur plus faible en raison d’une limite stricte (par exemple si l’option Shell Fork Bomb Protection est activée), vous pouvez ajouter la ligne suivante dans supervisord.conf :
[supervisord]
minfds = 100 # Votre limite stricte