- Principales informations
- Getting Started
- Agent
- API
- Tracing
- Conteneurs
- Dashboards
- Database Monitoring
- Datadog
- Site Datadog
- DevSecOps
- Incident Management
- Intégrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profileur
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Surveillance Synthetic
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- Développeurs
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Application mobile
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Alertes
- Watchdog
- Métriques
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Conteneurs
- Processes
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Termes et concepts de l'APM
- Sending Traces to Datadog
- APM Metrics Collection
- Trace Pipeline Configuration
- Connect Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilité des services
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Suivi des erreurs
- Sécurité des données
- Guides
- Dépannage
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Exploring Database Schemas
- Exploring Recommendations
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- RUM et Session Replay
- Surveillance Synthetic
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Code Coverage
- Quality Gates
- DORA Metrics
- Feature Flags
- Securité
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- CloudPrem
- Administration
Authentification multifacteur (MFA)
Présentation
L’authentification multifacteur (MFA), ou authentification à deux facteurs (2FA), exige qu’un utilisateur présente plus d’un type de vérification pour s’authentifier à un système. Le MFA protège contre la majorité des attaques liées aux mots de passe, y compris les attaques par force brute, le credential stuffing et le password spraying.
Fonctionnalités
- MFA pour les comptes Datadog natifs : le MFA est disponible comme couche de sécurité supplémentaire lors de la connexion pour les comptes qui se connectent directement à Datadog avec un e-mail et un mot de passe. Les comptes e-mail/mot de passe natifs sont plus vulnérables aux attaques que les comptes gérés via un fournisseur d’identité.
- MFA facultatif : le MFA est disponible pour les utilisateurs finaux comme fonctionnalité optionnelle. Activez le MFA à tout moment via vos paramètres personnels.
- MFA obligatoire : les administrateurs peuvent exiger que tous les utilisateurs d’une organisation qui se connectent avec un e-mail et un mot de passe enregistrent un second facteur d’authentification avant d’accéder à l’organisation. Pour activer l’application du MFA, consultez la section relative aux méthodes de connexion.
- Applications d’authentification : toute application d’authentification prenant en charge l’authentification par mot de passe à usage unique basé sur le temps (TOTP) peut être utilisée pour le MFA. Exemples : Microsoft Authenticator, Google Authenticator, Authy et Duo.
Limites
- Le MFA n’est pas disponible pour les comptes utilisant uniquement l’authentification unique (SSO). Pour utiliser le MFA avec SAML et Google Auth, configurez-le via votre fournisseur d’identité (IdP).
- Le MFA ne protège pas contre tous les types d’attaques. Par exemple, si un attaquant a accès à votre e-mail, il peut être en mesure de désactiver le MFA et de compromettre votre compte.
- Le MFA prend en charge au maximum une seule application d’authentification.
Prérequis
Pour configurer le MFA pour votre compte, connectez-vous en utilisant votre e-mail et mot de passe. Les utilisateurs qui se connectent via SSO ne voient pas les options de configuration du MFA.
Configurer le MFA pour votre compte utilisateur
Pour accéder à la page Password & Authentication :
- Vérifiez que vous êtes connecté avec une combinaison nom d’utilisateur et mot de passe, et non via SSO.
- Accédez à Personal Settings dans le menu de votre compte.
- Sous Security, sélectionnez Password & Authentication.
La section d’authentification multifacteur répertorie toutes les applications d’authentification configurées.
- En regard de Authenticator App, sélectionnez Add.
- Suivez la documentation de votre application d’authentification pour savoir comment ajouter un nouveau code QR.
- Saisissez le dernier code généré par votre application d’authentification dans l’invite pour confirmer que l’appareil a été configuré correctement.
- Conservez une copie des codes de récupération dans un endroit sûr. Les codes ne peuvent pas être récupérés une fois la configuration terminée.
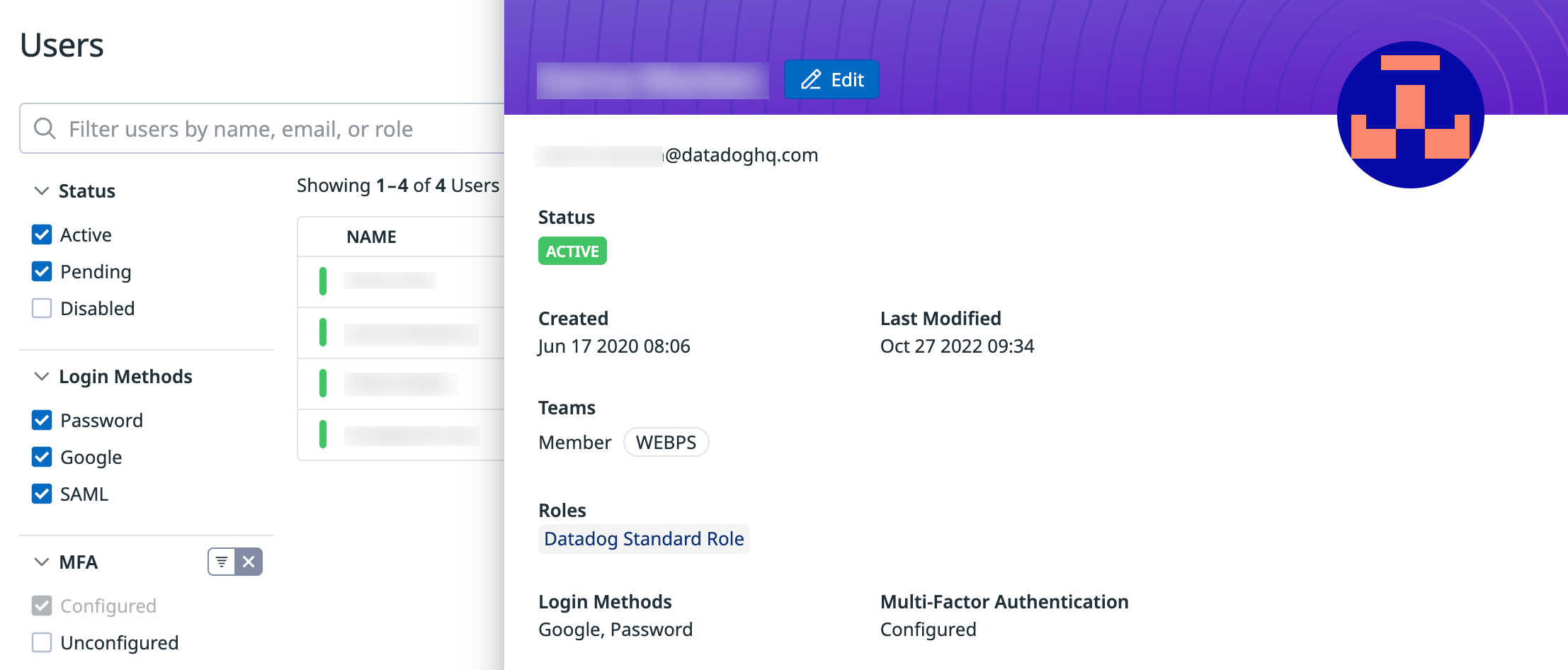
Consulter le statut du MFA d’un utilisateur
Pour savoir si un utilisateur a configuré le MFA ou non, vous pouvez filtrer le tableau Users. Le statut du MFA est également disponible dans le panneau des détails de l’utilisateur.
Récupération du MFA
Si vous n’avez pas accès à votre application d’authentification, vous pouvez utiliser un code de récupération au lieu d’un mot de passe à usage unique au cours de la procédure de connexion. Chaque code de récupération ne peut être utilisé qu’une seule fois.
- Accédez à la page de connexion.
- Saisissez votre adresse électronique et votre mot de passe, puis sélectionnez Log in.
- Sélectionnez Don’t have access to your authenticator?
- Saisissez l’un de vos codes de récupération inutilisés et cliquez sur Verify.
Récupération du MFA
Si vous n’avez pas accès à votre application d’authentification ou à vos codes de récupération, vous pouvez demander un lien de récupération unique par courrier électronique au cours de la procédure de connexion.
- Accédez à la page de connexion.
- Saisissez votre adresse électronique et votre mot de passe, puis sélectionnez Log in.
- Sélectionnez Don’t have access to your authenticator?
- Sélectionnez Don’t have access to your recovery codes? Get a one time recovery link via email.
- Consultez votre boîte mail et recherchez un message ayant pour objet « Recovery link for logging into your Datadog account ».
- Sélectionnez le lien Log in to Datadog pour terminer la connexion à votre compte.
Si vous avez perdu l’accès à votre application d’authentification enregistrée, Datadog recommande de supprimer l’appareil perdu et d’en ajouter un nouveau. Conserver une application d’authentification valide permet d’éviter des problèmes de connexion à votre compte à l’avenir.