- Esenciales
- Empezando
- Agent
- API
- Rastreo de APM
- Contenedores
- Dashboards
- Monitorización de bases de datos
- Datadog
- Sitio web de Datadog
- DevSecOps
- Gestión de incidencias
- Integraciones
- Internal Developer Portal
- Logs
- Monitores
- OpenTelemetry
- Generador de perfiles
- Session Replay
- Security
- Serverless para Lambda AWS
- Software Delivery
- Monitorización Synthetic
- Etiquetas (tags)
- Workflow Automation
- Centro de aprendizaje
- Compatibilidad
- Glosario
- Atributos estándar
- Guías
- Agent
- Arquitectura
- IoT
- Plataformas compatibles
- Recopilación de logs
- Configuración
- Automatización de flotas
- Solucionar problemas
- Detección de nombres de host en contenedores
- Modo de depuración
- Flare del Agent
- Estado del check del Agent
- Problemas de NTP
- Problemas de permisos
- Problemas de integraciones
- Problemas del sitio
- Problemas de Autodiscovery
- Problemas de contenedores de Windows
- Configuración del tiempo de ejecución del Agent
- Consumo elevado de memoria o CPU
- Guías
- Seguridad de datos
- Integraciones
- Desarrolladores
- Autorización
- DogStatsD
- Checks personalizados
- Integraciones
- Build an Integration with Datadog
- Crear una integración basada en el Agent
- Crear una integración API
- Crear un pipeline de logs
- Referencia de activos de integración
- Crear una oferta de mercado
- Crear un dashboard de integración
- Create a Monitor Template
- Crear una regla de detección Cloud SIEM
- Instalar la herramienta de desarrollo de integraciones del Agente
- Checks de servicio
- Complementos de IDE
- Comunidad
- Guías
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Aplicación móvil de Datadog
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft
- En la aplicación
- Dashboards
- Notebooks
- Editor DDSQL
- Reference Tables
- Hojas
- Monitores y alertas
- Watchdog
- Métricas
- Bits AI
- Internal Developer Portal
- Error Tracking
- Explorador
- Estados de problemas
- Detección de regresión
- Suspected Causes
- Error Grouping
- Bits AI Dev Agent
- Monitores
- Issue Correlation
- Identificar confirmaciones sospechosas
- Auto Assign
- Issue Team Ownership
- Rastrear errores del navegador y móviles
- Rastrear errores de backend
- Manage Data Collection
- Solucionar problemas
- Guides
- Change Tracking
- Gestión de servicios
- Objetivos de nivel de servicio (SLOs)
- Gestión de incidentes
- De guardia
- Status Pages
- Gestión de eventos
- Gestión de casos
- Actions & Remediations
- Infraestructura
- Cloudcraft
- Catálogo de recursos
- Universal Service Monitoring
- Hosts
- Contenedores
- Processes
- Serverless
- Monitorización de red
- Cloud Cost
- Rendimiento de las aplicaciones
- APM
- Términos y conceptos de APM
- Instrumentación de aplicación
- Recopilación de métricas de APM
- Configuración de pipelines de trazas
- Correlacionar trazas (traces) y otros datos de telemetría
- Trace Explorer
- Recommendations
- Code Origin for Spans
- Observabilidad del servicio
- Endpoint Observability
- Instrumentación dinámica
- Live Debugger
- Error Tracking
- Seguridad de los datos
- Guías
- Solucionar problemas
- Límites de tasa del Agent
- Métricas de APM del Agent
- Uso de recursos del Agent
- Logs correlacionados
- Stacks tecnológicos de llamada en profundidad PHP 5
- Herramienta de diagnóstico de .NET
- Cuantificación de APM
- Go Compile-Time Instrumentation
- Logs de inicio del rastreador
- Logs de depuración del rastreador
- Errores de conexión
- Continuous Profiler
- Database Monitoring
- Gastos generales de integración del Agent
- Arquitecturas de configuración
- Configuración de Postgres
- Configuración de MySQL
- Configuración de SQL Server
- Configuración de Oracle
- Configuración de MongoDB
- Setting Up Amazon DocumentDB
- Conexión de DBM y trazas
- Datos recopilados
- Explorar hosts de bases de datos
- Explorar métricas de consultas
- Explorar ejemplos de consulta
- Exploring Database Schemas
- Exploring Recommendations
- Solucionar problemas
- Guías
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Experiencia digital
- Real User Monitoring
- Pruebas y monitorización de Synthetics
- Continuous Testing
- Análisis de productos
- Entrega de software
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Visibility
- Configuración
- Network Settings
- Tests en contenedores
- Repositories
- Explorador
- Monitores
- Test Health
- Flaky Test Management
- Working with Flaky Tests
- Test Impact Analysis
- Flujos de trabajo de desarrolladores
- Cobertura de código
- Instrumentar tests de navegador con RUM
- Instrumentar tests de Swift con RUM
- Correlacionar logs y tests
- Guías
- Solucionar problemas
- Code Coverage
- Quality Gates
- Métricas de DORA
- Feature Flags
- Seguridad
- Información general de seguridad
- Cloud SIEM
- Code Security
- Cloud Security Management
- Application Security Management
- Workload Protection
- Sensitive Data Scanner
- Observabilidad de la IA
- Log Management
- Observability Pipelines
- Gestión de logs
- CloudPrem
- Administración
- Gestión de cuentas
- Seguridad de los datos
- Ayuda
Correlación basada en patrones
Este producto no es compatible con el sitio Datadog seleccionado. ().
Información general
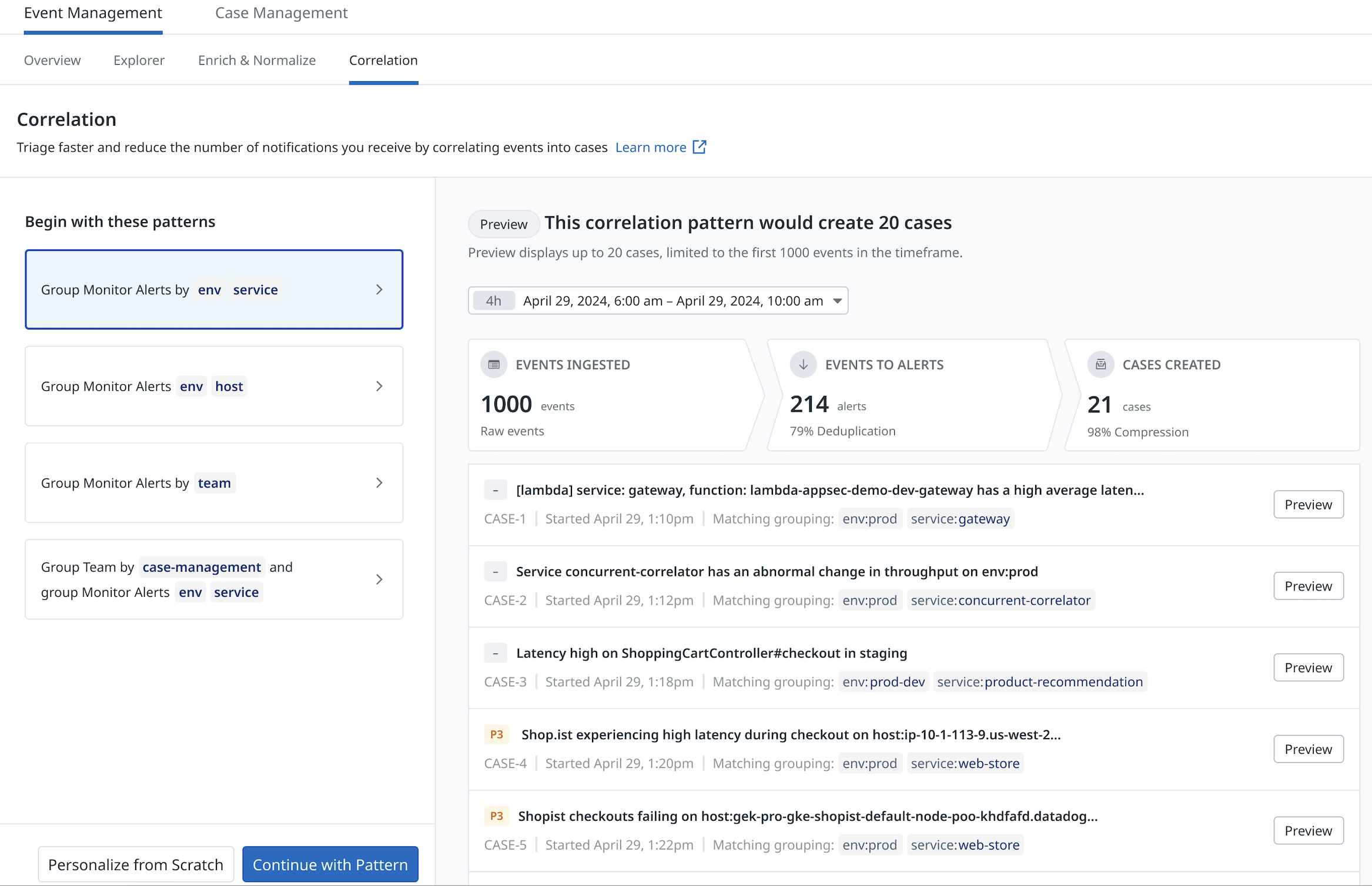
La correlación basada en patrones te permite controlar cómo se correlacionan los eventos. Datadog también utiliza Machine Learning para enriquecer automáticamente tu patrón con eventos de monitor de Datadog relacionados, utilizando la telemetría subyacente recopilada en Datadog y otros heurísticos.
Para empezar, Datadog sugiere automáticamente correlaciones basadas en patrones, en función de tu entorno. Haz clic en cualquiera de las recomendaciones para abrir la página de configuración correspondiente al patrón recomendado. Los campos de configuración ya están rellenados.
Crear un patrón
Para crear un patrón:
- Ve a Correlación.
- Haz clic en + Add a Pattern (+ Añadir un patrón), en la parte superior de la tabla de patrones. Se abrirá la página de configuración de patrones, que muestra los patrones sugeridos en la parte izquierda y una vista previa del resultado del patrón en la parte derecha.
- Puedes ajustar un patrón sugerido haciendo clic en + Continue With Pattern (+ Continuar con el patrón). Esto le llevará a la página de configuración para realizar ajustes adicionales. También puedes crear tu propio patrón haciendo clic en + Personalize From Scratch (+ Personalizar desde cero).
Primero, los eventos se deduplican en alertas en función de la clave de agregación de eventos. Luego, las alertas se correlacionan con un caso en función de la configuración.
Para obtener más información sobre cómo enviar eventos con claves de agregación, consulta el envío de eventos a Datadog. Los eventos sin claves de agregación se deduplican en una única alerta dentro del periodo de tiempo.Patrones sugeridos
Los patrones se recomiendan en función de tus etiquetas (tags) de servicios y entornos utilizadas con mayor frecuencia, para ayudarte a empezar con la correlación de eventos rápidamente.
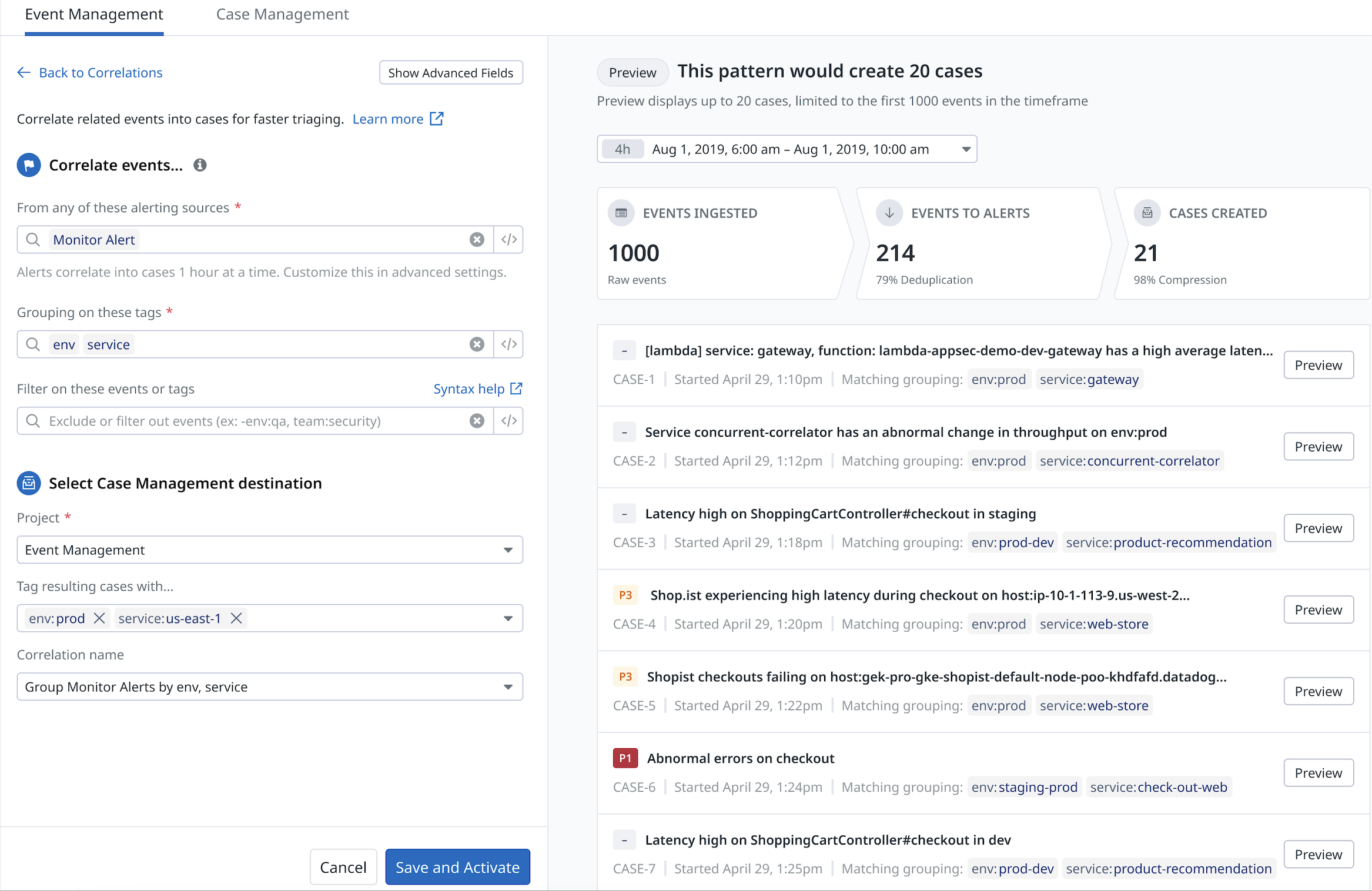
Configuración
De la página de configuración de las correlaciones
- En el desplegable, selecciona la fuente de eventos que quieres utilizar para agrupar.
- Para excluir eventos de la fuente definida anteriormente, añade una consulta de eventos en Filtrar por estos eventos o etiquetas (tags) para filtrarlos.
- Añade eventos relacionados a cambios asociados u otros eventos adicionales para apoyar la investigación del caso. Los eventos relacionados se añadirán a un caso pero no crearán nuevos casos.
- Define las etiquetas de agrupación. Las etiquetas de agrupación son facetas de eventos. Si no ves la etiqueta en el desplegable, consulta la sección de configuración avanzada a continuación. Nota: Puedes crear facetas en el atributo y en la etiqueta del evento. Para obtener más información, consulta la documentación sobre facetas.
Ajustes avanzados (opcional)
Haz clic en Show Advanced Settings (Mostrar configuración avanzada).
Puedes añadir etiquetas de agrupación para correlacionar eventos y personalizar el título del caso.
- Añadir etiquetas de agrupación
- añadir nuevas etiquetas de agrupación es lo mismo que añadir nuevas facetas de eventos.
- Personalizar el título del caso
- para crear una plantilla que sustituya al título del caso generado automáticamente. Puedes hacer referencia a las variables de plantilla de etiqueta utilizando la sintaxis de handlebar, por ejemplo “{{tag.service}}”, para incluir una lista separada por comas de valores de etiquetas.
En Lógica de correlación avanzada, puedes especificar el número mínimo de eventos correlacionados para crear un caso y actualizar el periodo de tiempo.
Periodos de tiempo
Correlacionar alertas con un caso por : la duración máxima durante la que las nuevas alertas se añadirán a un caso
Deduplicar eventos para esas alertas por : la duración máxima para reflejar las transiciones de estado de las alertas actuales que se correlacionaron, pero que siguen flapeando o no se resolvieron. Los eventos se deduplican en la alerta correspondiente del caso existente antes de abrir un nuevo caso.
Previsualizar el resultado del patrón
Previsualiza los posibles patrones y casos que tu configuración podría crear. El panel de vista previa muestra
- el número total de eventos ingeridos (limitado a los primeros 1000 eventos).
- el número de alertas que se deduplicarían de los eventos.
- el número de casos que se crearían en función de la configuración.
Utiliza estos datos para previsualizar el impacto de tus correlaciones y comprender el resultado esperado de un patrón.
Nota: El título por defecto en la vista previa del caso es la primera alerta en correlación. Luego de guardar un patrón, el título de caso de la gestión de eventos se genera de forma inteligente.
Seleccionar un destino de gestión de casos
- En el menú desplegable Proyecto, selecciona un caso existente al que enviar tus eventos agrupados.
- (Opcional) Añade una etiqueta a los casos resultantes.
- Haz clic en Save and Activate (Guardar y activar) para activar este patrón y agrupar eventos en casos.
Actualizar el patrón existente
Después de actualizar un patrón existente, todos los casos activos se dejarán de procesar. Los nuevos eventos que coincidan con el patrón crearán un nuevo caso.
Para leer más
Más enlaces, artículos y documentación útiles: