- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- OpenTelemetry
- Profiler
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Cloud Cost
- Application Performance
- APM
- APM Terms and Concepts
- Application Instrumentation
- APM Metrics Collection
- Trace Pipeline Configuration
- Correlate Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origins for Spans
- Service Observability
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Error Tracking
- Data Security
- Guides
- Troubleshooting
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Tag Pipelines
Overview
To effectively monitor cloud costs, you need a comprehensive understanding of how various services, teams, and products contribute to your overall spending. Tag Pipelines enforce the use of standardized tags across your cloud resources and ensure consistent, accurate cost attribution throughout your organization.
With Tag Pipelines, you can create tag rules to address missing or incorrect tags on your cloud bills. You can also create new inferred tags that align with specific business logic to enhance the accuracy of your cost tracking.
Tag pipelines are applied to Cloud Cost metrics from all providers. Tag pipelines are not applied to Cloud Cost Recommendations.
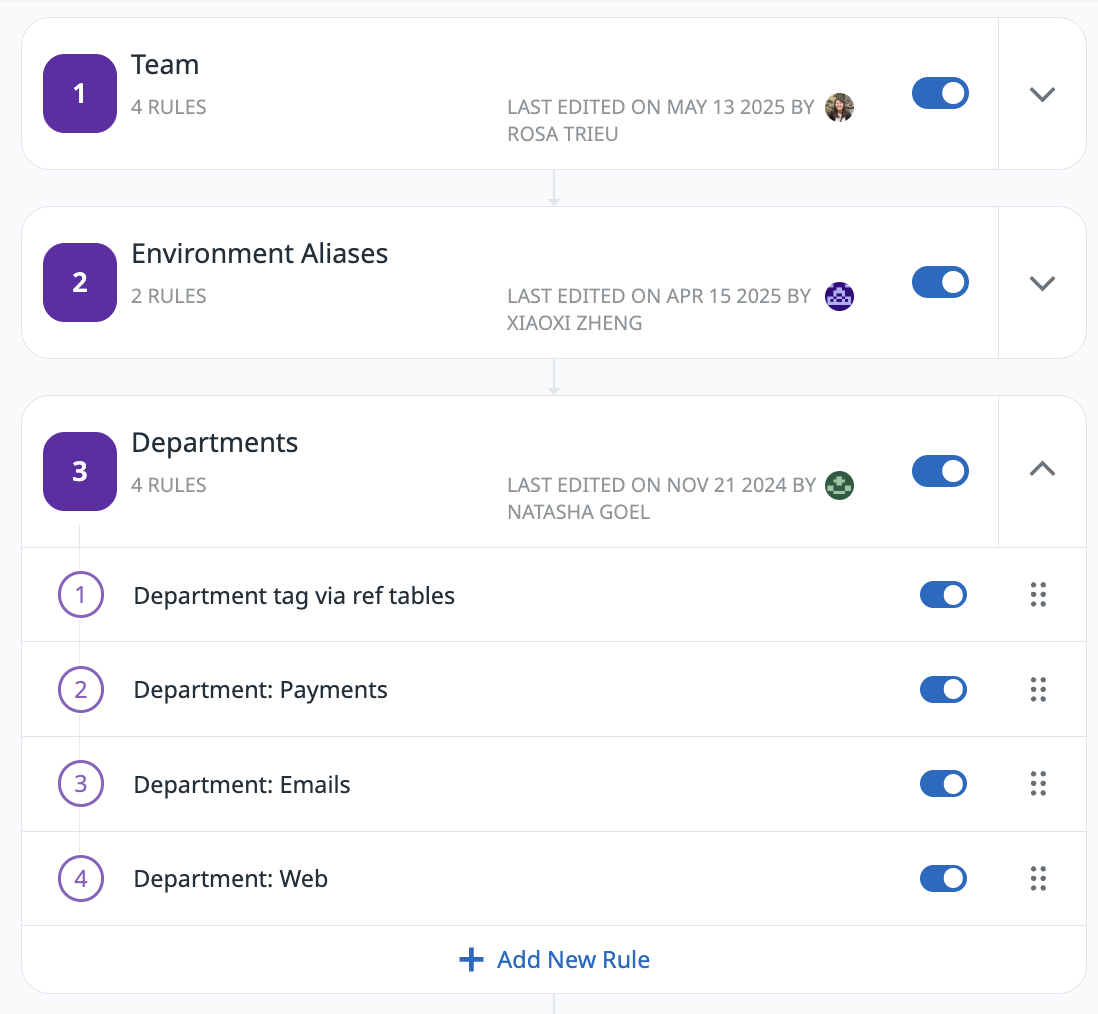
Create a ruleset
To create a ruleset, navigate to Cloud Cost > Settings > Tag Pipelines.
You can create up to 100 rules. API-based Reference Tables are not supported.
Before creating individual rules, create a ruleset (a folder for your rules) by clicking + New Ruleset.
Within each ruleset, click + Add New Rule and select a rule type: Add tag, Alias tag keys, or Map multiple tags. These rules execute in a sequential, deterministic order from top to bottom.
You can organize rules and rulesets to ensure the order of execution matches your business logic.
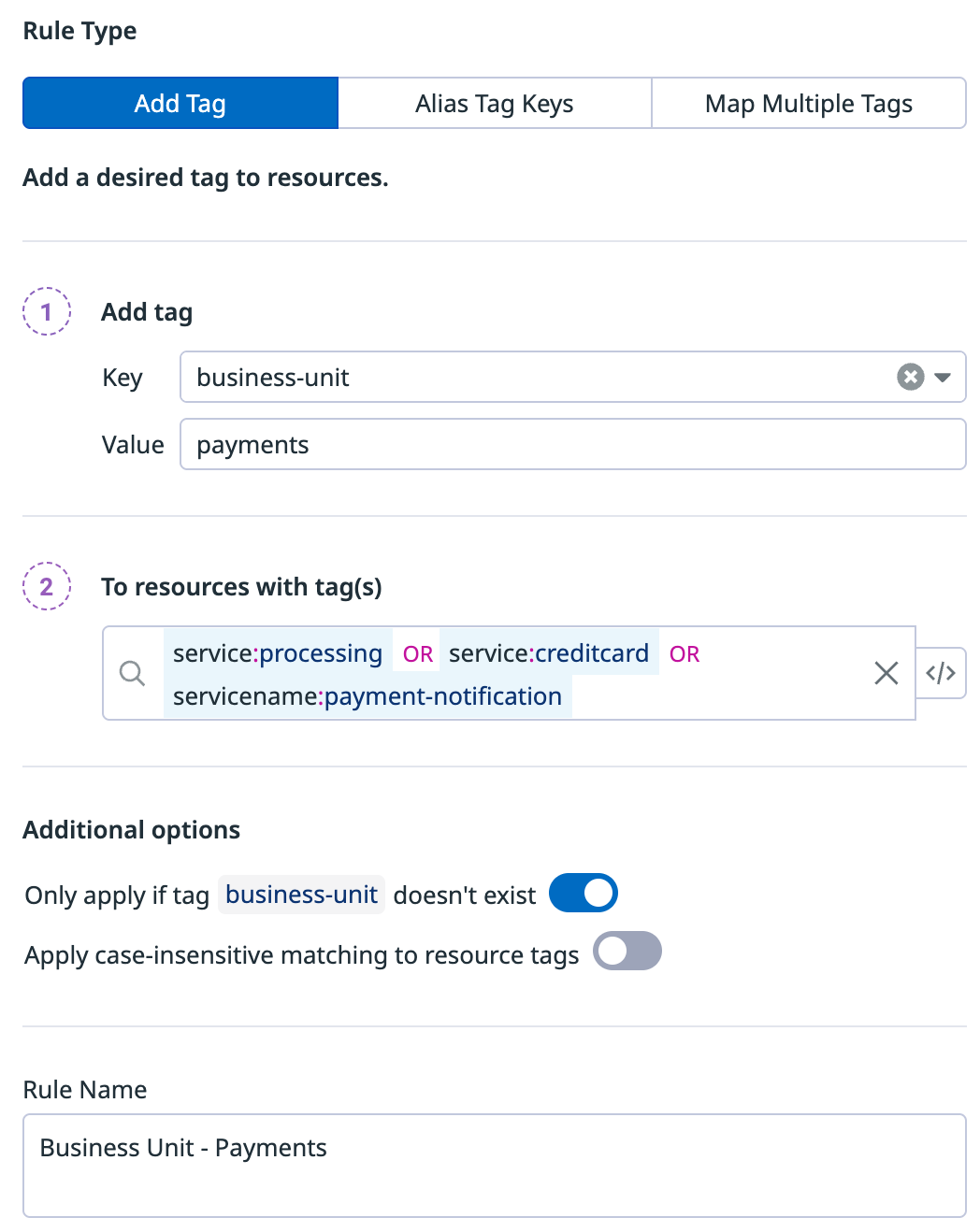
Add tag
Add a new tag (key + value) based on the presence of existing tags on your Cloud Costs data.
For example, you can create a rule to tag all resources with their business unit based on the services those resources are a part of.
Under the Additional options section, you have the following options:
- Only apply if tag
{tag}doesn’t exist - Ensures the rule only applies if the specified tag (business-unitin the example above) doesn’t already exist. - Apply case-insensitive matching to resource tags - Enables tags defined in the
To resources with tag(s)field and tags from the cost data to be case insensitive. For example, if resource tags from the UI is:foo:barand the tag from the cost data isFoo:bar, then the two can be matched.
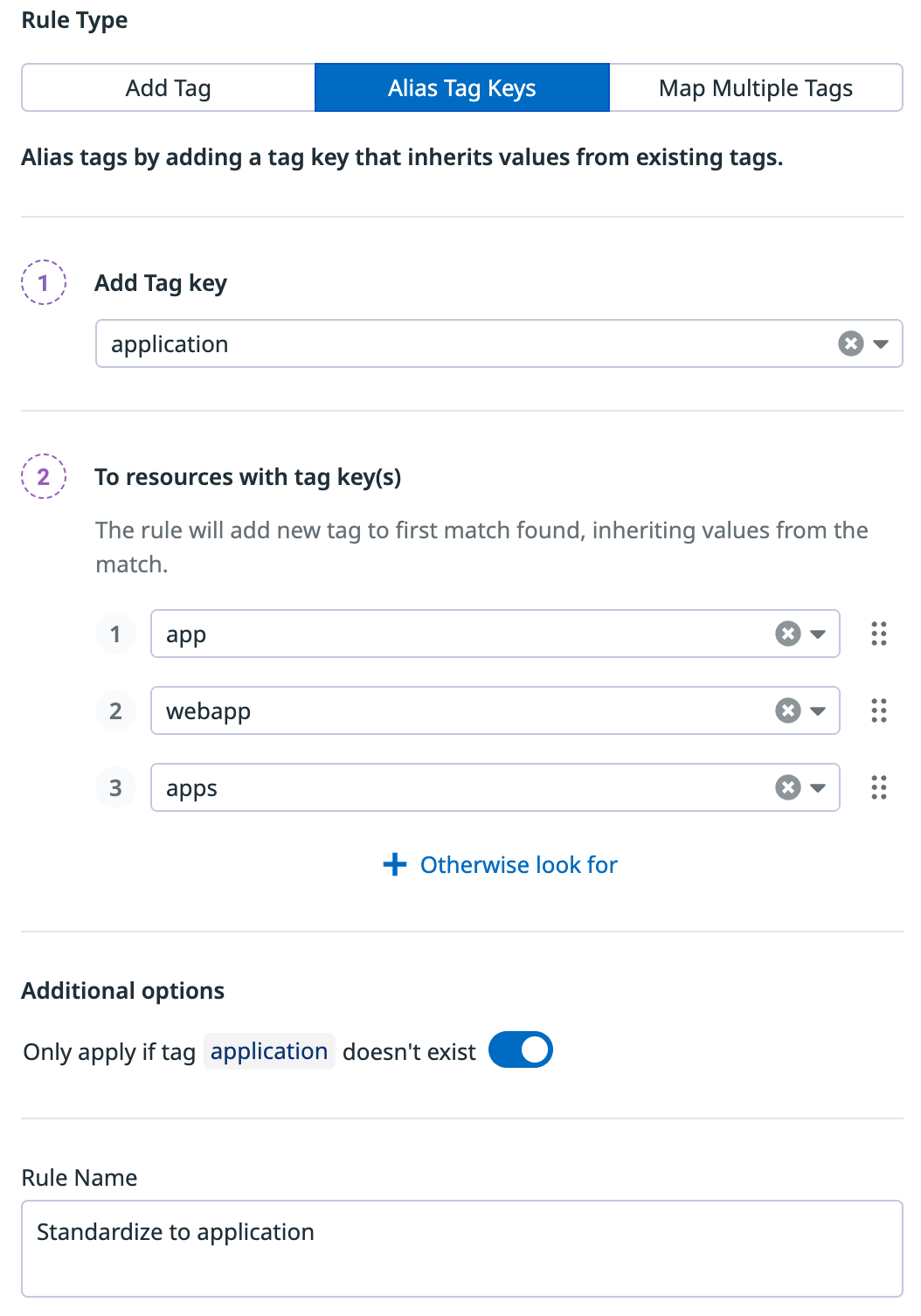
Alias tag keys
Map existing tag values to a more standardized tag.
For example, if your organization wants to use the standard application tag key, but several teams have a variation of that tag (like app, webapp, or apps), you can alias apps to application. Each alias tag rule allows you to alias a maximum of 25 tag keys to a new tag.
Add the application tag to resources with app, webapp, or apps tags. The rule stops executing for each resource after a first match is found. For example, if a resource already has a app tag, then the rule no longer attempts to identify a webapp or apps tag.
To ensure the rule only applies if the application tag doesn’t already exist, click the toggle in the Additional options section.
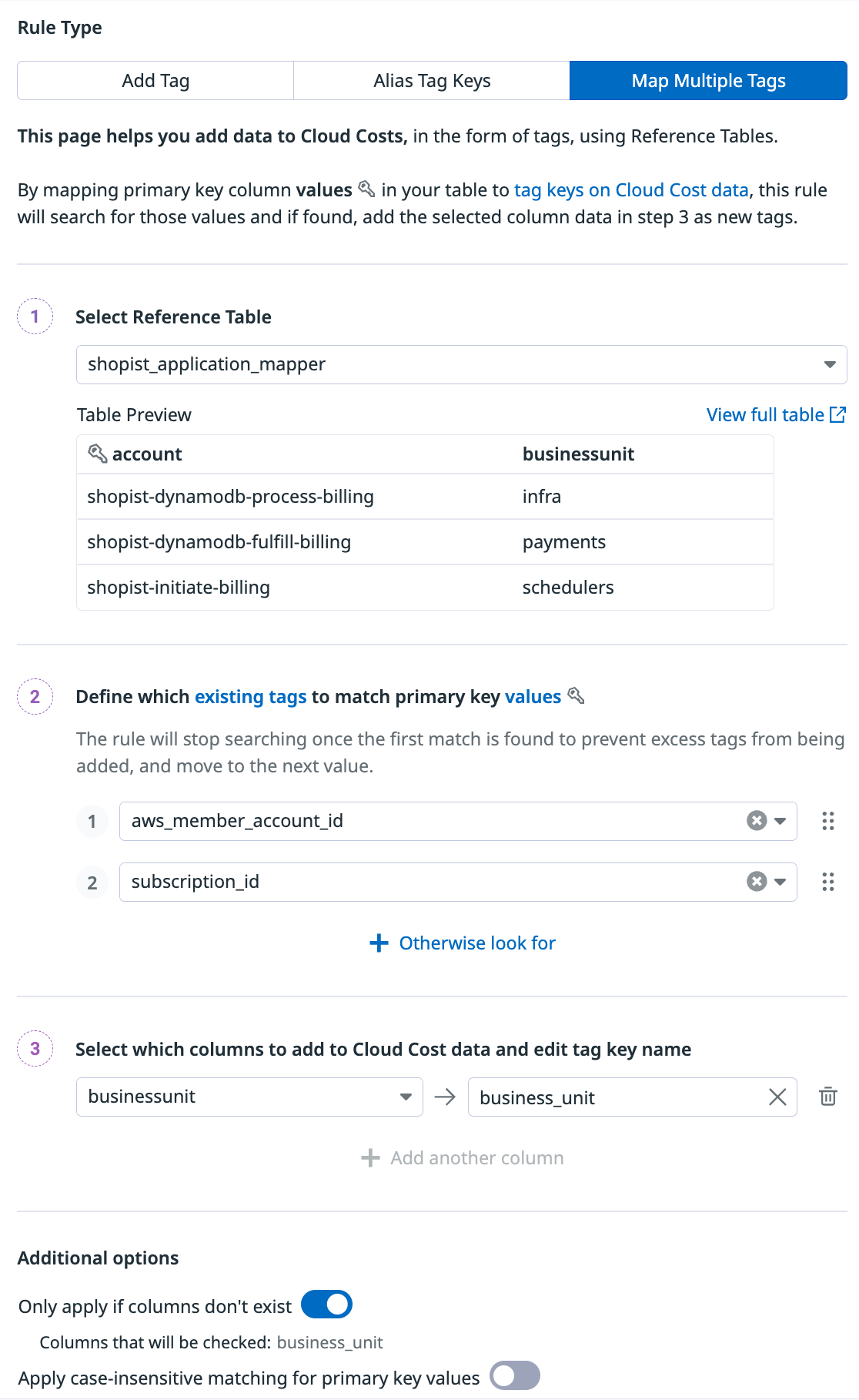
Map multiple tags
Use Reference Tables to add multiple tags to cost data without creating multiple rules. This maps the values from your Reference Table’s primary key column to values from cost tags. If found, the pipelines adds the selected Reference Table columns as tags to cost data.
For example, if you want to add information about which VPs, organizations, and business_units different AWS and Azure accounts fall under, you can create a table and map the tags.
Similar to Alias tag keys, the rule stops executing for each resource after a first match is found. For example, if an aws_member_account_id is found, then the rule no longer attempts to find a subscriptionid.
Under the Additional options section, you have the following options:
- Only apply if columns don’t exist - Ensures the defined columns are only added if they do not already exist with the associated tags from the cost data.
- Apply case-insensitive matching for primary key values - Enables case-insensitive matching between the primary key value from the reference table and the value of the tag in the cost data where the tag key matches the primary key. For example, if the primary key value pair from UI is: foo:Bar and the tag from the cost data is foo:bar, then the two can be matched.
Reserved tags
Certain tags such as env and host are reserved tags, and are part of Unified Service Tagging. The host tag cannot be added in Tag Pipelines.
Using tags helps correlate your metrics, traces, processes, and logs. Reserved tags like host provide visibility and effective monitoring across your infrastructure. For optimal correlation and actionable insights, use these reserved tags as part of your tagging strategy in Datadog.
Delete tags
To delete a tag created using Tag Pipelines, delete the rule that created it. Within 24 hours, the tag will be automatically removed from the most recent three months of data. To remove the tag from older data, request a backfill through [Datadog support][5].
Further reading
Additional helpful documentation, links, and articles: