- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Internal Developer Portal
- Logs
- Monitors
- Notebooks
- OpenTelemetry
- Profiler
- Search
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Build an Integration with Datadog
- Create an Agent-based Integration
- Create an API-based Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Remote Configuration
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Service Level Objectives
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Event Management
- Incident Response
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- End User Device Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Storage Management
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Observability
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Session Replay
- Software Delivery
- CI Visibility
- CD Visibility
- Deployment Gates
- Test Optimization
- Code Coverage
- PR Gates
- DORA Metrics
- Feature Flags
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- AI Guard
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Configuration
- Sources
- Processors
- Destinations
- Packs
- Akamai CDN
- Amazon CloudFront
- Amazon VPC Flow Logs
- AWS Application Load Balancer Logs
- AWS CloudTrail
- AWS Elastic Load Balancer Logs
- AWS Network Load Balancer Logs
- Cisco ASA
- Cloudflare
- F5
- Fastly
- Fortinet Firewall
- HAProxy Ingress
- Istio Proxy
- Juniper SRX Firewall Traffic Logs
- Netskope
- NGINX
- Okta
- Palo Alto Firewall
- Windows XML
- ZScaler ZIA DNS
- Zscaler ZIA Firewall
- Zscaler ZIA Tunnel
- Zscaler ZIA Web Logs
- Search Syntax
- Scaling and Performance
- Monitoring and Troubleshooting
- Guides and Resources
- Log Management
- CloudPrem
- Administration
Controls
Overview
Governance Console Controls audit and enforce organizational standards. You can use these controls to automate hygiene and quality tasks that typically require manual effort, such as managing unused API keys or enforcing tagging standards.
Using controls
On the Governance Console Controls page, select a control.
Configure detection.
Under Scope detections, enter parameters to define the control’s behavior. Datadog’s defaults are based on best practices, but you can adjust the value of each parameter to relax or tighten the standard for your organization.
If you are using multiple Datadog sub-organizations, control behavior and scoping is defined per organization and does not span across organizations.To verify your configuration, use the Manual Mitigation tab to see what is being detected by this control.
Configure notifications.
Under Notify users, select your notification recipients and frequency. The notification email summarizes identified and unresolved control detections and includes a link back to the Governance Console control to review and mitigate.
Configure automatic enforcement.
When Enforce control is disabled, a control requires manual mitigation. Toggling on Enforce control enables automated enforcement actions. Automation allows administrators to automate cleanup activity without having to manually review and apply each change.
For Select automated mitigation, select a mitigation. If you select Manual (default), the control detects noncompliant assets, and you can manually take actions based on these detections. See manual mitigation.
To delay mitigation, enter a number of days under Remediation Delay. You can delay remediation for up to 1 week. This grants additional time for administrators to take additional actions before automatic enforcement occurs.
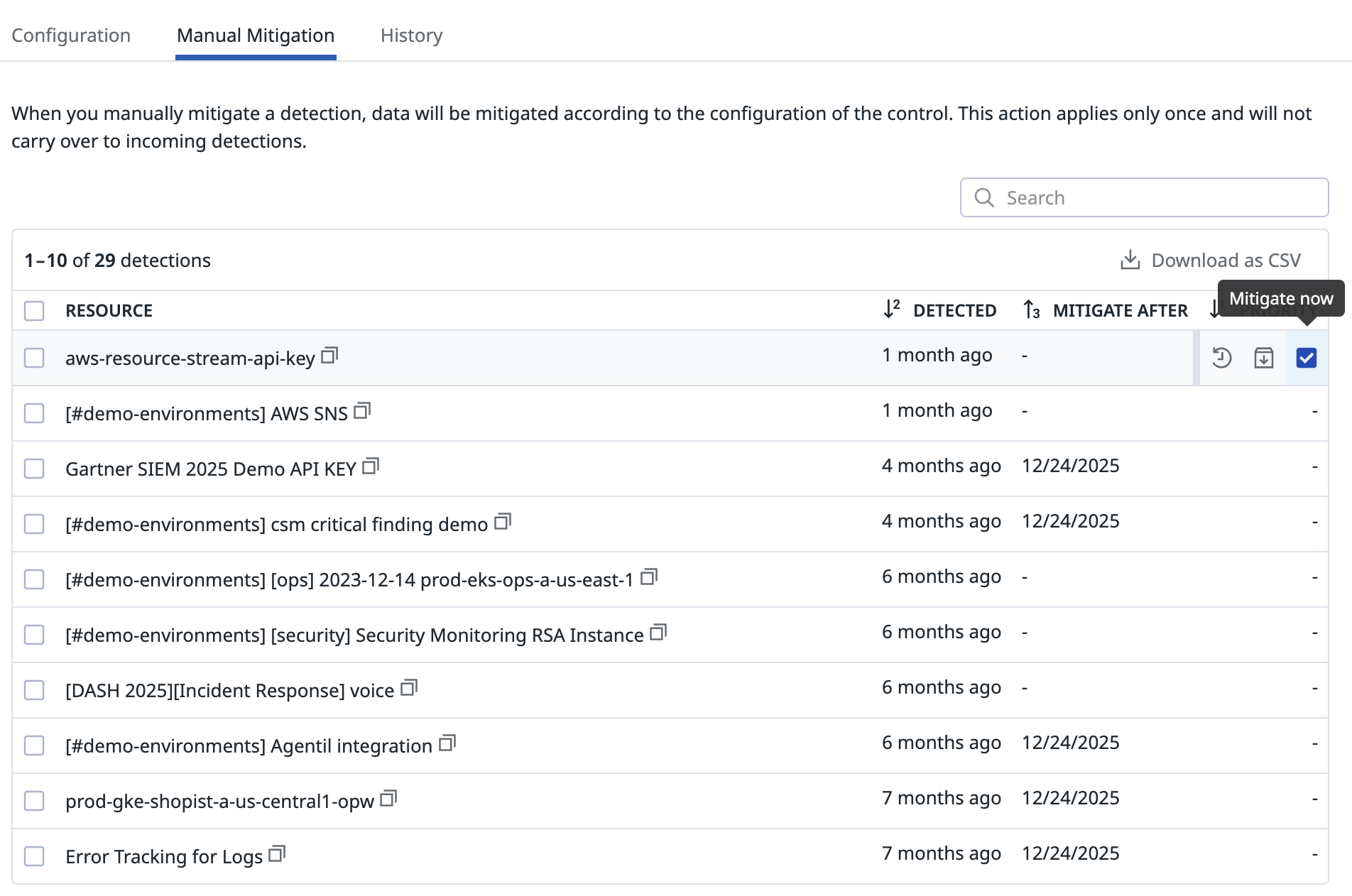
Manual mitigation
Use the Manual Mitigation tab to view all detections.
Hover over each detection for options:
- Delay mitigation: Delay mitigation of this asset for up to 1 week. This grants additional time for the administrator or owner to take additional actions before automated enforcement takes place.
- Ignore detection: Ignore this detection and remove it from consideration for mitigation.
- Mitigate now: Noncompliant assets are mitigated according to the configuration of the control. This action applies only once, and does not carry over to incoming detections. Mitigation requires the associated permission for modifying that asset.
All available controls
Controls are organized by usage concern: security, cost optimization, and data hygiene.
Security
Security
Security controls detect and correct configuration that could lead to increased risk of a security incident in your Datadog account.
- Unused API Keys
- Identifies API keys that have not been used within your specified time threshold, helping reduce security risks from dormant credentials. The default threshold is 30 days of inactivity, and can be adjusted.
Enforcement automatically identifies and revokes inactive API keys to improve security and reduce potential attack surface.
- Unused Application Keys
- Identifies application keys that have not been used within your specified time threshold, helping reduce security risks from dormant credentials. The default threshold is 30 days of inactivity, and can be adjusted.
Enforcement automatically identifies and revokes inactive application keys to improve security and reduce potential attack surface.
- Roles Without Users
- Identifies roles that have no active users assigned to them, indicating potential cleanup opportunities.
This control does not support enforcement. Manual removal of unused roles required.
- Users in No Teams
- Identifies active users that are not in any teams, indicating potential cleanup opportunities.
This control does not support enforcement.
Cost optimization
Cost optimization
Cost optimization controls detect and correct configuration that could lead to increased spending on low value usage.
- Unqueried Metrics
- Identifies metrics that are rarely or never queried and are not associated with any monitors, dashboards, SLOs, or notebooks, indicating potential cost savings opportunities.
Enforcement automatically removes unused metric tags using Metrics without Limits™ to optimize cardinality and reduce costs.
- Inactive Metric Tag
- Identifies metric tags that are rarely or never queried and are not associated with any monitors, dashboards, SLOs, or notebooks, presenting opportunities to reduce cardinality and costs.
Enforcement automatically configures Metrics without Limits™ to allowlist only active tags on filtered metrics, optimizing cardinality and cost efficiency.
- Synthetic Tests with Muted Monitors
- Identifies synthetic tests with muted monitors, which may indicate potential cost savings opportunities.
This control does not support enforcement.
Data hygiene
Data hygiene
Data hygiene controls detect and correct configuration that could lead to increased assets that are low quality or have unclear ownership.
- Unused Dashboards
- Identifies dashboards that have not been viewed within your specified time threshold, helping maintain a clean and organized workspace. The default Dashboard Query includes all dashboards, but can be adjusted to select a specific scope of dashboards. The default Dashboard Activity Lookback Period is 30 days of query activity, and can be adjusted.
Enforcement automatically deletes dashboards to maintain a clean and organized workspace.
- Dashboards Owned by Disabled Users
- Identifies dashboards whose owner is a disabled user, which may impact dashboard maintenance and updates. The default Dashboard Query includes all dashboards, but can be adjusted to select a specific scope of dashboards.
This control does not support enforcement.
- Dashboards Without Team Tags
- Identifies dashboards that lack a team tag, making it difficult to track ownership and maintain accountability. The default Dashboard Query includes all dashboards, but can be adjusted to select a specific scope of dashboards. The default Dashboard Activity Lookback Period is 30 days of query activity, and can be adjusted.
This control does not support enforcement.
- Notebooks Without Team Tags
- Identifies notebooks that lack a team tag, making it difficult to track ownership and maintain accountability.
This control does not support enforcement.
- Monitors Without Team Tags
- Identifies monitors that lack a team tag, making it difficult to track ownership and maintain accountability.
This control does not support enforcement.
- Monitors with Broken Notification Handles
- Identifies monitors that contain invalid or broken @-mention handles, which may prevent notifications from reaching the intended recipients.
This control does not support enforcement.